Posts by Doug Madory

























About Doug Madory
Doug Madory is the director of internet analysis for Kentik where he works on internet infrastructure analysis. The Washington Post dubbed him “The Man who can see the Internet” for his reputation in identifying significant developments in the global layout of the internet. Doug is regularly quoted by major news outlets about developments ranging from national blackouts to BGP hijacks to the activation of submarine cables. Prior to Kentik, he was the lead analyst for Oracle’s internet intelligence team (formerly Dyn Research and Renesys).
Starlink, the revolutionary low-earth-orbit satellite-based internet service, has quickly become one of the most transformative technologies in the world of internet communications. Using over three years of GeoIP data, we analyze the growth of Starlink as it expanded from 41 to 157 countries. This evolution included the emergence of “Community Gateways” and notable GeoIP entries for locations like Mars, Antarctica, SpaceX launch sites, and politically sensitive areas such as the Palestinian Territories, Kosovo, Venezuela, Myanmar, and Sudan.
This post expands on our analysis from last year that revealed that as much as 20% of IPv4 space has migrated out of Ukraine in the years following the Russian invasion in February 2022. This update reveals that AT&T (a popular destination for Ukrainian IPs) has since implemented a policy ridding itself of customers using AS7018 to originate their routes, often to support residential proxies.
Iran is in the midst of one of the world’s most severe communications blackouts. This post uses Kentik data to detail how this historic event unfolded, where this event lies in the context of previous Iranian shutdowns, and finally discusses what might be in store next for Iran.
This year-end wrap-up covers topics from BGP security (including ASPA and excessive AS-SETs) and the geopolitical (Ukraine’s IPv4 exodus, the Iran internet shutdown, and Red Sea cable cuts) to the year’s most significant outages (TikTok, the Spain/Portugal blackout, and cloud failures at AWS, Azure, and Cloudflare). Plus, we explore Starlink’s new Community Gateways, and revisit the evolving landscape of AS ranking and OTT service tracking.
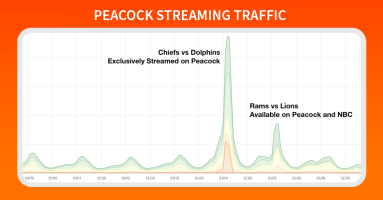
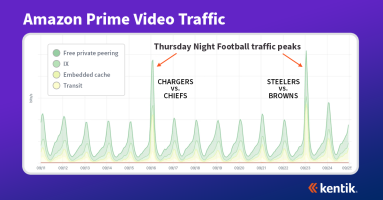
In this edition of Anatomy of an OTT Traffic Surge, we look at Thursday Night Football on Amazon Prime Video. Based on traffic stats, TNF is the most watched program on the streaming service. Using Kentik’s OTT capabilities, we’ll see how this program gets delivered and how that has changed over 11 weeks of the NFL season.
Loaf and behold, this retrospective covers nearly 20 years of the Baker’s Dozen style annual ranking of the biggest ASes of the internet. In it we discuss the DFZ, de-peerings, and partitions. It was the yeast we could do.
Afghanistan has imposed its first nationwide internet shutdown, cutting off connectivity to “prevent immorality” — a blow to digital freedoms, education, and media already under severe strain since the Taliban’s 2021 return.
In this post, we dig into the impacts from the latest submarine cable cuts in the Red Sea from loss of transit for regional providers to the increase in latency for the major public clouds.
Last month, Starlink suffered its largest outage in years, arguably its biggest since becoming a major internet provider. In addition to the millions of individual customers around the world, the outage disconnected the Community Gateways, customers of Starlink’s new transit service. In this post, we delve into the outage and its impact on these far-flung networks.
On July 14, Cloudflare’s popular public DNS service (known as 1.1.1.1) suffered an outage lasting over two hours. As rumors swirled about the cause, we were the first to push back on the theory that a BGP hijack had caused the outage. In fact, the hijack was actually a consequence. How did we know this so early when other internet watchers did not? We’ll discuss in this post.
In this post, we discuss how the ongoing war in Ukraine has led to a significant decline in the amount of IPv4 address space announced by Ukrainian Autonomous Systems (ASes), and why those addresses are often now being announced by western ISPs and major public clouds.
On Monday April 28, 2025, the countries of Spain and Portugal experienced a widespread electrical blackout of historic proportions. In this post, we look into the internet outages caused by the loss of power including impacts outside of the Iberian Peninsula and to Starlink service in Spain.
An AS-SET is a special object that represents a group of ASNs and forms the basis for IRR-based route filtering. However, many AS-SETs in circulation today have grown so big that they effectively whitelist much of the routing table, rendering them ineffective. According to recent analysis, there are currently 2,192 AS-SETs which expand to over 1,000 ASNs each! In this blog post, we’ll describe what an AS-SET is, its role in route filtering, and how to deal with excessively large AS-SETs.
In this edition of Beyond Their Intended Scope, we take a look at last week’s BGP leak by a DDoS mitigation company which impacted networks around the world. We look at the impacts in both BGP and traffic data, and discuss how RFC 9234’s “Only to Customer” BGP Path Attribute could have helped.
Starlink moves beyond being strictly a direct-to-consumer service provider with the recent activations of its Community Gateways. In recent months, Starlink has become a transit provider to a small but growing number of service providers in remote parts of the world as its unique and groundbreaking service continues to evolve.
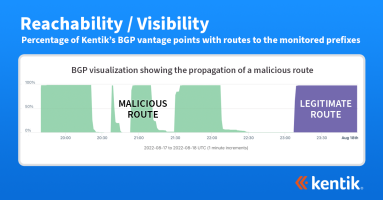
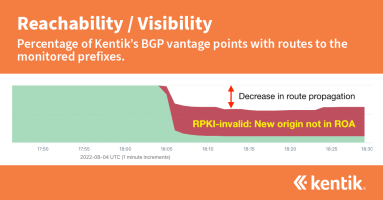
On March 18, 2025, North Korea’s BGP routes became RPKI-invalid due to the publication of a faulty ROA. In this post, we’ll visualize the impact on the propagation of affected routes and what North Korea (and you too!) can do to avoid problems with the optional maxLength attribute.
CLM Chowder is a new series which highlights notable observations of cloud connectivity surfaced by Kentik’s Cloud Latency Map. In this edition, we look at measurements from Alibaba (China), latency swings from South Africa, and a temporary latency jump from Marseilles to Asia.
In this second installment of Beyond Their Intended Scope, we analyze a recent BGP leak out of Brazil that briefly affected networks around the world. Because this routing mishap was a path leak (i.e., did not involve any mis-originations and therefore immune from RPKI ROV protection), it demonstrates why we need a thing called ASPA … ASAP.
Kentik’s Doug Madory looks into this weekend’s 14-hour outage of popular video sharing service TikTok, which was slated to be banned from the US per recent legislation. While TikTok came back, it is notably no longer being served by parent company Bytedance’s US CDN. We delve into the traffic statistics in this blog post.
On Monday, Netflix debuted professional wrestling as its latest foray into live event streaming. The airing of WWE’s Monday Night Raw followed Netflix’s broadcasts of a heavily-promoted boxing match featuring a 58-year-old Mike Tyson and two NFL games on Christmas Day. In this post, we look into the traffic statistics of how these programs were delivered.
In this post, Doug Madory reviews the highlights of his wide-ranging internet analysis from the past year, which included covering the state of BGP (leaks and the state of RPKI adoption), submarine cables (both cuts), major outages, and how geopolitics has shaped the internet in 2024.
On November 15, Netflix made another venture into the business of live event streaming with the highly-anticipated, if somewhat absurd, boxing match between the 58-year-old former heavyweight champion Mike Tyson and social media star Jake Paul. The five hour broadcast also included competitive undercard fights including a bloody rematch between Katie Taylor and Amanda Serrano. Doug Madory looks at how Netflix delivered the fight using Kentik’s OTT Service Tracking.
On Saturday, November 2, the wildly popular video game Fortnite released its latest game update: Fortnite Chapter 2 Remix. The result was a surge of traffic as gaming platforms around the world downloaded the latest update for the seven-year-old game. Doug Madory looks at how the resulting traffic surge can be analyzed using Kentik’s OTT Service Tracking.
Today, we’re excited to announce the launch of Kentik’s Cloud Latency Map, a public service that uses Kentik Synthetics to continuously measure latency between the regions of the biggest cloud providers.
The first installment of our new blog series, Beyond Their Intended Scope, covers BGP mishaps that may have escaped the community’s attention but are worthy of analysis. In this post, we review a recent BGP leak that redirected internet traffic through Russia and Central Asia as a result of a path error leak by Uztelecom, the incumbent service provider of Uzbekistan.
In this post, we dig into the impacts from Hurricane Helene which came ashore late last month wreaking destruction and severe flooding in the Southeastern United States. Using Kentik’s traffic data as well as Georgia Tech’s IODA, we detail the impacts in three of the hardest-hit states: Georgia, South Carolina, and North Carolina.
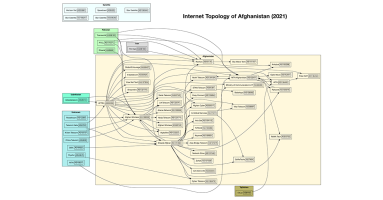
Kentik’s Director of Internet Analysis uses BGP to see how the internet of Afghanistan has changed in the three years following the US military’s departure.
Last Tuesday, August 13 was the second Tuesday of the month, and for anyone running a network or working in IT, you know what that means: another Microsoft Patch Tuesday. Doug Madory looks at how the resulting traffic surge can be analyzed using Kentik’s OTT Service Tracking.
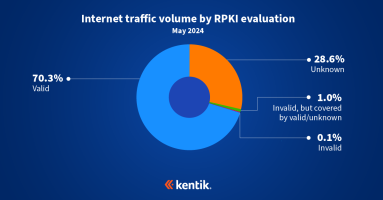
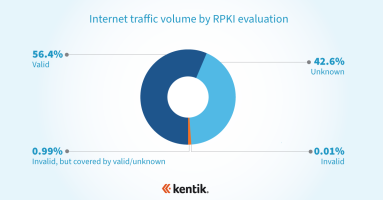
The FCC recently published a proposal to require nine major US internet service providers to deploy RPKI Route Origin Validation (ROV). In this post, we’ll look at the proposal and where the nine service providers currently stand with respect to ROV.
In RPKI, determining when exactly a ROA expires is not a simple question. In this post, BGP experts Doug Madory and Fastly’s Job Snijders discuss the difference between the expiration dates embedded inside ROAs and the much shorter effective expiration dates used by validators. Furthermore, we analyze how the behavior effective expiration dates change over time due to implementation differences in the chain of certificate authorities.
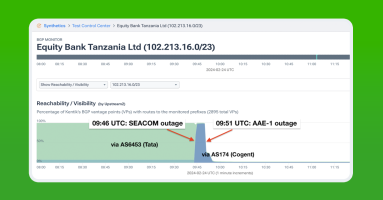
In this post, Doug Madory digs into the latest submarine cable failure impacting internet connectivity in Africa: the Seacom and EASSy cables suffered breaks on May 12 near the cable landing station in Maputo, Mozambique.
In this blog post, BGP experts Doug Madory of Kentik and Job Snijders of Fastly review the latest RPKI ROV deployment metrics in light of a major milestone.
In the latest collision between geopolitics and the physical internet, three major submarine cables in the Red Sea were cut last month likely as a result of attacks by Houthi militants in Yemen on passing merchant vessels. In this post, we review the situation and delve into some of the observable impacts of the subsea cable cuts.
NFL playoffs are here, and Doug Madory tells us how Saturday’s first-ever exclusively live-streamed NFL playoff game was delivered without making any references to pop superstar Taylor Swift or her sizzling romance with nine-time Pro Bowler Travis Kelce.
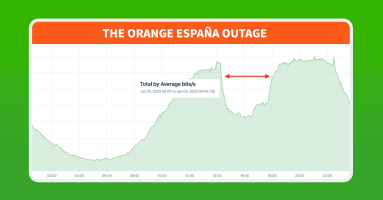
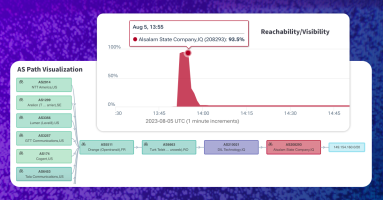
Orange España, Spain’s second largest mobile operator, suffered a major outage on January 3, 2024. The outage was unprecedented due to the use of RPKI, a mechanism designed to protect internet routing security, as a tool for denial of service. In this post, we dig into the outage and the unique manipulation of RPKI.
In this post, Doug Madory reviews the highlights of his wide-ranging internet analysis from the past year, which included covering the state of BGP (both routing leaks and progress in RPKI), submarine cables (both cuts and another historic activation), major outages, and how geopolitics has shaped the internet in 2023.
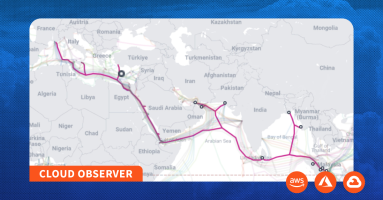
In this edition of the Cloud Observer, we dig into the impacts of recent submarine cable maintenance on intercontinental cloud connectivity and call for the greater transparency from the submarine cable industry about incidents which cause critical cables to be taken out of service.
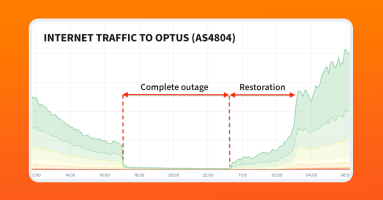
Last week a major internet outage took out one of Australia’s biggest telecoms. In a statement out yesterday, Optus blames the hours-long outage, which left millions of Aussies without telephone and internet, on a route leak from a sibling company. In this post, we discuss the outage and how it compares to the historic outage suffered by Canadian telecom Rogers in July 2022.
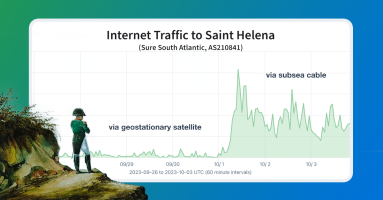
Just after midnight on October 1, 2023, the remote island of Saint Helena in the South Atlantic began passing internet traffic over its long-awaited, first-ever submarine cable connection. In this blog post, we cover how Kentik’s measurements captured this historic activation, as well as the epic story of the advocacy work it took to make this development possible.
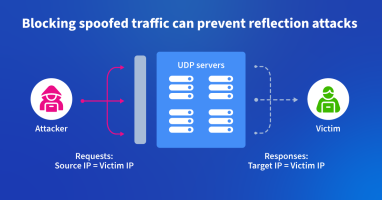
In this blog post, we describe how one backbone service provider uses Kentik to identify and root out spoofed traffic used to launch DDoS attacks. It’s a “moral responsibility,” says their chief architect.
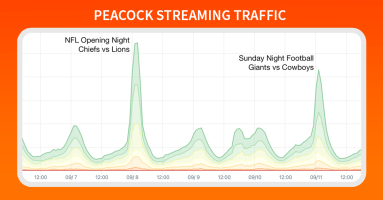
Football is officially back, and Doug Madory is here to show you exactly how well the NFL’s streaming traffic was delivered.
Doug Madory investigates two large BGP leaks from August 28 and 29, 2023 and how RPKI ROV and other technologies can help mitigate widespread internet disruptions that can result for incidents like these.
On Sunday, August 6, an undersea landslide in one of the world’s longest submarine canyons knocked out two of the most important submarine cables serving the African internet. The loss of these cables knocked out international internet bandwidth along the west coast of Africa. In this blog post, we review some history of the impact of undersea landslides on submarine cables and use some of Kentik’s unique data sets to explore the impacts of these cable breaks.
This past weekend, the government of Iraq blocked the popular messaging app Telegram, citing the need to protect Iraqi’s personal data. However, when an Iraqi government network leaked out a BGP hijack used for the block, it became yet another BGP incident that was both intentional, but also accidental. Thankfully disruption was minimized by Telegram’s use of RPKI.
Stretching back to the AS7007 leak of 1997, this comprehensive blog post covers the most notable and significant BGP incidents in the history of the internet, from traffic-disrupting BGP leaks to crypto-stealing BGP hijacks.
In this blog post, BGP experts Doug Madory of Kentik and Job Snijders of Fastly update their RPKI ROV analysis from last year while discussing its impact on internet routing security.
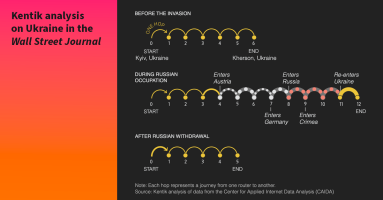
It has now been over a year since Russian forces invaded its neighbor to the west leading to the largest conflict in Europe since World War II. Kentik’s Doug Madory reviews what has happened with internal connectivity within Ukraine over the course of the war in this analysis done for a collaboration with the Wall Street Journal.
In this article, Doug Madory uncovers the little-known “Russification” of Ukrainian IP addresses — a phenomenon that complicates the task of internet measurement and impacts Ukrainians connecting to the internet using IP addresses suddenly considered Russian.
In the early hours of Wednesday, January 25, Azure, Microsoft’s public cloud, suffered a major outage that disrupted their cloud-based services and popular applications such as Sharepoint, Teams, and Office 365. In this post, we’ll highlight some of what we saw using Kentik’s unique capabilities, including some surprising aftereffects of the outage that continue to this day.
This week marks a decade since the ALBA-1 submarine cable began carrying traffic between Cuba and the global internet. And last month’s recommendation by the US Department of Justice to deny the request by the ARCOS cable system to connect Cuba shows that, almost a decade later, geopolitics continues to shape the physical internet — especially when it comes to Cuba.
Only two days into the new year and we had our first BGP routing leak. It was followed by a couple more in subsequent days. In this blog post, we use some of Kentik’s unique capabilities to take a look at what happened, what the impacts were, and what might prevent these in the future.
This past year was another busy one for the internet. This year-end blog post highlights some of the top pieces of analysis that we published in the past 12 months. This analysis employs Kentik’s data, technology, and expertise to inform the industry and the public about issues involving the technical underpinnings of the global internet and how global events can impact connectivity.
The populations in Cuba and Iran were only the latest to experience what has become an increasingly common tactic of digital authoritarianism: the internet curfew. This tactic, in which internet service is temporarily disabled on a recurring basis, lowers the costs and thus increases the likelihood of government-directed internet disruptions.
This fall Amazon Prime Video became the exclusive broadcaster of the NFL’s Thursday Night Football. This move continued Prime Video’s push into the lucrative world of live sports broadcasting. As you can imagine, these games have led to a surge in traffic for this OTT service.
On August 17, 2022, an attacker was able to steal $235,000 in cryptocurrency by employing a BGP hijack against Celer Bridge, a cryptocurrency service. While this incident is the latest such attack, there are lessons beyond the world of cryptocurrency for any organization that conducts business on the internet.
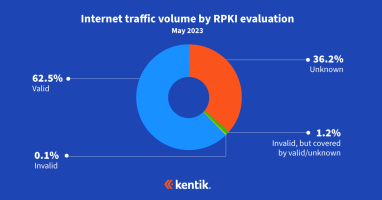
Our analysis from earlier this year estimated that the majority of internet traffic now goes to routes covered by ROAs and is thus eligible for the protection that RPKI ROV offers. This analysis takes the next step in understanding RPKI ROV deployment by measuring the rejection of invalid routes.
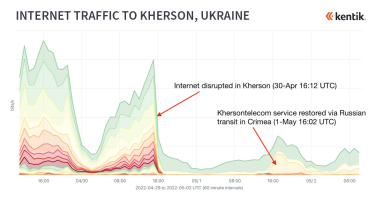
Since the beginning of June 2022, internet connectivity in the Russian-held Ukrainian city of Kherson has been rerouted through Crimea, the peninsula in southern Ukraine that has been occupied by Russia since March 2014. As I explain in this blog post, the rerouting of internet service in Kherson appears to parallel what took place following the Russian annexation of Crimea.
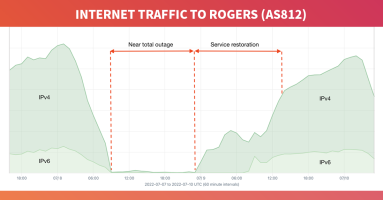
On July 8, 2022, Canadian telecommunications giant Rogers Communications suffered a catastrophic outage taking down nearly all services for its 11 million customers in the largest internet outage in Canadian history. We dig into the outage and debunk the notion that it was caused by the withdrawal of BGP routes.
On Tuesday, June 7, internet users in numerous countries from East Africa to the Middle East to South Asia experienced an hours-long degradation in service due to an outage at one of the internet’s most critical chokepoints: Egypt. In this blog post, we review some of the impacts as well as compare how this disruption affected connectivity within the three major public cloud providers.
RPKI is the internet’s best defense against BGP hijacks. What is it? And how does it protect the majority of your outbound traffic from accidental BGP hijacks without posing a risk to legitimate traffic?
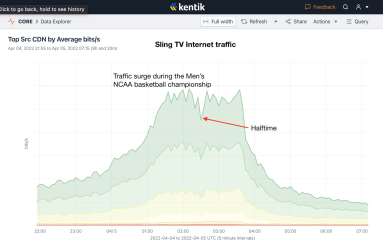
Last night, Kansas topped the University of North Carolina in a thrilling come-from-behind victory to win their fourth championship in men’s college basketball. It was also notable in how viewers saw the game. Instead of being aired on network television like in the past, the game was carried on TBS requiring viewers to have either a cable TV package or use a streaming service to watch the game. Here’s what we saw.
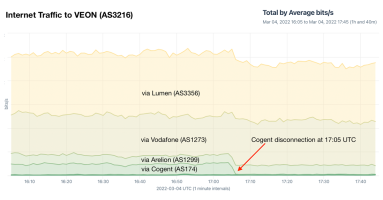
In our updated blog post, read why international telcos Cogent and Lumen say they are taking action against Russia.
Just in time for Valentine’s Day, we’re announcing our newest labor of love: Kentik Market Intelligence (KMI), a new product that spells out the internet ecosystem.
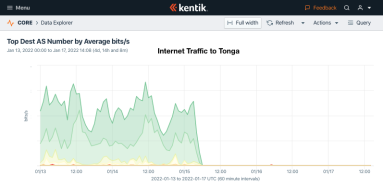
On Saturday, the pacific island nation of Tonga was decimated by a massive volcanic eruption that was visible from space. At 5:27pm local time, the underwater volcano Hunga Tonga-Hunga Ha’apai unexpectedly erupted, sending ash and debris for hundreds of miles. As of this writing, all internet and telephone communications between Tonga and the rest of the world are still down.
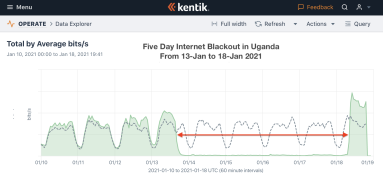
Every year the internet suffers numerous disruptions and outages, and 2021 was no exception. Kentik’s Doug Madory recaps the top 10. And now the world’s network engineers deserve a load of #HugOps in 2021.
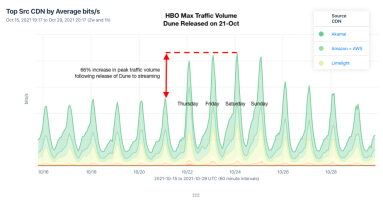
Last month, the long-awaited film adaptation of Frank Herbert’s sci-fi epic Dune was released in theaters and on HBO Max. Directed by Canadian filmmaker Denis Villeneuve, the movie was a hit at the box office as well as via streaming, leading to another OTT traffic surge.
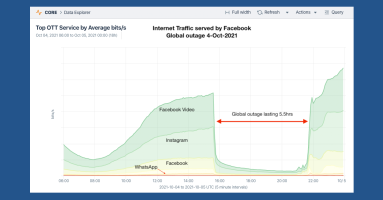
Facebook suffered a historic and nearly six-hour global outage on October 4. In this post, we look at Kentik’s view of the outage.
Last Tuesday, September 14th was the second Tuesday of the month, and for anyone running a network or working in IT, you know what that means: another Microsoft Patch Tuesday. Doug Madory looks at how the resulting traffic surge can be analyzed using Kentik’s OTT Service Tracking.
There has been a new development in The Mystery of AS8003.
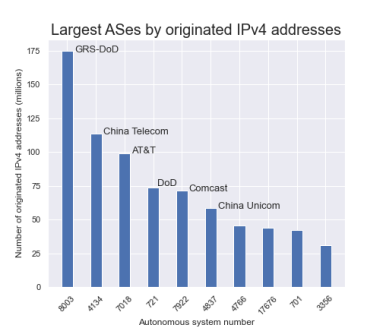
As you may recall, this was the AS number registered to a defunct company in Florida that appeared earlier this year in the global routing table announcing over 175 million IPv4 addresses belonging to the US Department of Defense.
Well, that just changed.
As the last US military aircraft depart Kabul, so closes a chapter of U.S. involvement in the country. Will it also end a period of growth of the domestic internet in Afghanistan?
Africa’s regional internet registry, AFRINIC, is involved in a legal dispute over an increasingly valuable commodity: IPv4 address space. Kentik’s Doug Madory takes a deeper look at what’s happening.
On January 20, 2021, a great mystery appeared in the internet’s global routing table. An entity that hadn’t been heard from in over a decade began announcing large swaths of formerly unused IPv4 address space belonging to the U.S. Department of Defense. Registered as GRS-DoD, AS8003 began announcing 11.0.0.0/8 among other large DoD IPv4 ranges.
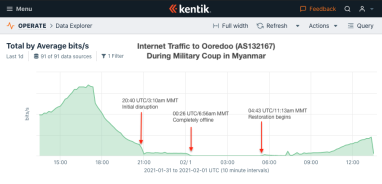
In the past 24hrs, Myanmar experienced a military coup d’état during which prominent government figures like Nobel laureate Aung San Suu Kyi were detained and internet service was almost entirely blacked out.
Here is what the shutdown looked like in our data (with annotations for timing) for Myanmar’s big four: Myanma Posts and Telecommunications (MPT), Telenor Myanmar, Ooredoo Myanmar, and Mytel.
Last week I had the honor to participate in the PTC 2021 conference. Held in Hawaii every January, PTC’s annual conference is the Pacific Rim’s premier telecommunications event. Although this year’s conference was all virtual (no boondoggles to Honolulu!), it was no less important as the theme this year was New Realities. In the following blog post, I summarize what I presented in my PTC panel entitled Strategies to Meet Network Needs.
The shutdown in Egypt not only shifted the dynamics of protest in the 21st century, it was a watershed moment for the internet community — from technical organizations like Renesys to digital rights advocacy groups like Access Now. The era of the large-scale government-directed internet shutdown had truly begun.