Posts by Jim Frey

























About Jim Frey
Jim has 24 years of experience in network and infrastructure management products and services, straddling both enterprise and service provider sectors. At Kentik, Jim is responsible for channel and alliance partnership development.
Prior to joining Kentik, Jim was an independent industry analyst, working as VP Research at Enterprise Management Associates (EMA). During his 6.5 years at EMA, Jim covered the ever evolving landscape of enterprise network and infrastructure management tools, technologies, and practices via direct primary research, practitioner dialogue, and technical product studies.
Before that, Jim spent six years with NetScout Systems as Vice President of Marketing, where he was responsible for global programs including product marketing, solution marketing, field events, sales training, marketing communications, press & analyst relations, channel marketing, and competitive analysis. Other prior experiences include working as Vice President of Strategic Marketing at Micromuse, Director of Product Marketing at Objective Systems Integrators (acquired by Agilent Technologies) and six years working at Cabletron Systems on the SPECTRUM line of products in program, product, and partner management roles.
Jim holds an M.Sc. in Computer and Information Sciences from RPI, and a B.Sc. in Geological Engineering from the Colorado School of Mines.
Sciens is one of Kentik’s newest channel partners, serving the Korean market. In this Q&A, we highlight a bit about the team behind Sciens, who they are and what they do.
Edgeworx is one of Kentik’s largest and most active channel partners, specialized in the Canadian region. In this Q&A, we highlight a bit about who they are and what they do.
TechEnabler is a Kentik Channel Partner headquartered in Sao Paulo, Brazil. In this Q&A, VP of Channel Sales Jim Frey highlights a bit about the partner, who they are and what they do.
Kentik is growing! Today we marked our permanent landing in Europe. Kentik’s SaaS solution has already been embraced by dozens of organizations across the European continent — and our new presence will support even more organizations who deliver or depend on routed networks and the Internet as an essential part of their operations and business.
Kentik’s VP of Channels Jim Frey takes a look back at RSA 2018. After walking the show floor, in this post he highlights how the event has grown over the years as the security vendor landscape has gotten more complex and bloated. He also explains why good technology alone is not the answer.
From telcos, to financial services, to tech companies, we asked 30 of our peers one question: What are your 2018 networking predictions? Yes, it’s a broad question. But respondents (hailing from network, data center, and security operations teams) surfaced five main predictions for the year ahead.
After presenting at the recent CIOArena conference in Atlanta, Kentik VP of Strategic Alliances Jim Frey came away with a number of insights about the adoption of digital business operations in the enterprise. In his first in a series of related posts, Jim looks at audience survey responses indicating how reliant enterprises — even those that aren’t digital natives or located in tech industry hotspots — have become on the Internet for core elements of their business.
While Kentik Detect’s ground-breaking DDoS detection is field-proven to catch 30% more attacks than legacy systems, our DDoS capabilities aren’t limited to standalone detection. We’re also actively working with leading mitigation providers to create end-to-end DDoS protection solutions. So we’re excited to be partnering with A10 Networks, whose products help defend some of the largest networks in the world, to enable seamless integration of Kentik Detect with A10 Thunder TPS mitigation.
Kentik enhances DDoS protection by partnering with Radware and integrating Radware DefensePro. PenTeleData, a joint customer, saw a 30% improvement in stopping DDoS attacks after deploying the combined solution. Read the post to learn more.
Can legacy DDoS detection keep up with today’s attacks, or do inherent constraints limit network protection? In this post Jim Frey, Kentik VP Strategic Alliances, looks at how the limits of appliance-based detection systems contribute to inaccuracy — both false negatives and false positives — while the distributed big data architecture of Kentik Detect significantly enhances DDoS defense.
In this post, based on a webinar presented by Jim Frey, VP Strategic Alliances at Kentik, we look at how changes in network traffic flows — the shift to the Cloud, distributed applications, and digital business in general — has upended the traditional approach to network performance monitoring, and how NPM is evolving to handle these new realities.
As Gartner Research Director Sanjit Ganguli pointed out last May, network performance monitoring appliances that were designed for the era of WAN-connected data centers leave significant blind spots when monitoring modern applications that are distributed across the cloud. In this post Jim Frey, VP Strategic Alliances, explores Ganguli’s analysis and explains how Kentik NPM closes the gaps.
Cisco Live 2016 gave us a chance to meet with BrightTalk for some video-recorded discussions on hot topics in network operations. This post focuses on the first of those videos, in which Kentik’s Jim Frey, VP Strategic Alliances, talks about the complexity of today’s networks and how Big Data NetFlow analysis helps operators achieve timely insight into their traffic.
By actively exploring network traffic with Kentik Detect you can reveal attacks and exploits that you haven’t already anticipated in your alerts. In previous posts we showed a range of techniques that help determine whether anomalous traffic indicates that a DDoS attack is underway. This time we dig deeper, gathering the actionable intelligence required to mitigate an attack without disrupting legitimate traffic.
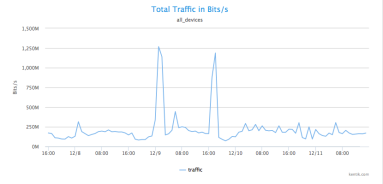
With massive data capacity and analytical flexibility, Kentik Detect makes it easy to actively explore network traffic. In this post we look at how to use this capability to rapidly discover and analyze interesting and potentially important DDoS and other attack vectors. We start with filtering by source geo, then zoom in on a time-span with anomalous traffic. By looking at unique source IPs and grouping traffic by destination IP we find both the source and the target of an attack.