Posts by Job Snijders
























An AS-SET is a special object that represents a group of ASNs and forms the basis for IRR-based route filtering. However, many AS-SETs in circulation today have grown so big that they effectively whitelist much of the routing table, rendering them ineffective. According to recent analysis, there are currently 2,192 AS-SETs which expand to over 1,000 ASNs each! In this blog post, we’ll describe what an AS-SET is, its role in route filtering, and how to deal with excessively large AS-SETs.
In RPKI, determining when exactly a ROA expires is not a simple question. In this post, BGP experts Doug Madory and Fastly’s Job Snijders discuss the difference between the expiration dates embedded inside ROAs and the much shorter effective expiration dates used by validators. Furthermore, we analyze how the behavior effective expiration dates change over time due to implementation differences in the chain of certificate authorities.
In this blog post, BGP experts Doug Madory of Kentik and Job Snijders of Fastly review the latest RPKI ROV deployment metrics in light of a major milestone.
In this blog post, BGP experts Doug Madory of Kentik and Job Snijders of Fastly update their RPKI ROV analysis from last year while discussing its impact on internet routing security.
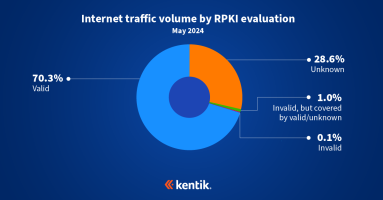
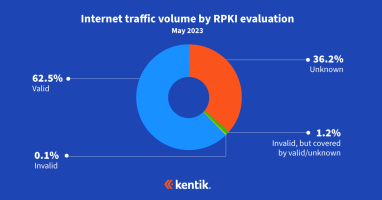
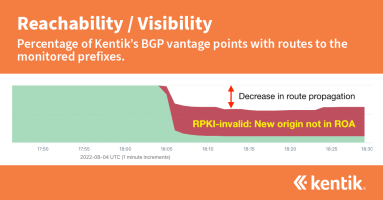
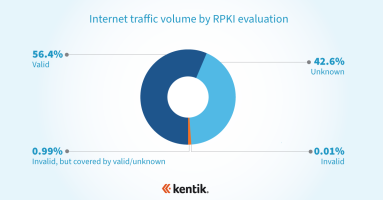
Our analysis from earlier this year estimated that the majority of internet traffic now goes to routes covered by ROAs and is thus eligible for the protection that RPKI ROV offers. This analysis takes the next step in understanding RPKI ROV deployment by measuring the rejection of invalid routes.
RPKI is the internet’s best defense against BGP hijacks. What is it? And how does it protect the majority of your outbound traffic from accidental BGP hijacks without posing a risk to legitimate traffic?