Posts by Justin Ryburn

























About Justin Ryburn
Justin Ryburn is the Field CTO here at Kentik. He has 20 years of experience in various operations, engineering, sales, and marketing positions with companies such as Savvis, Nortel, XO, Juniper, and Kentik. Justin contributed content to Cyber Forensics (Auerbach Publishing, 2007) and authored “Day One: Deploying BGP FlowSpec” (Juniper, 2015). He has also spoken at numerous industry conferences on the topics of network monitoring and security. Justin holds an MBA and an MS in IT Management from Webster University in St. Louis, Missouri, as well as numerous industry certifications. He currently lives in St. Louis with his wife and two kids.
Agentic AI is the next evolution in network management, moving beyond simple automation to intelligent systems that can reason, plan, and act autonomously. Justin Ryburn, Kentik Field CTO, highlights how this shift automates expertise, enables proactive problem-solving, and empowers human engineers for strategic innovation.
AutoCon3 in Prague offered important takeaways on network automation’s evolution, from hands-on learning and design principles to the impact of AI and the power of community. Read Justin Ryburn’s recap to learn about key insights from the event, showing why network automation is now a core competency you’ll want to understand.
NANOG 93 brought the networking community together for insightful discussions on the future of connectivity, emphasizing continuous learning, adaptation, and collaboration. Justin Ryburn highlights key takeaways from this premier event in the world of networking.
AWS re:Invent 2024 brought together a record-breaking 80,000 attendees in Las Vegas to explore the latest innovations in cloud computing, from generative AI to sustainability. In this post, Justin Ryburn shares his key takeaways from the event, highlighting AWS’s vision for the future and the vibrant energy of the conference.
AutoCon2 gathered network automation professionals in Denver for three days of insights, workshops, and discussions on the future of automation. Justin Ryburn, Kentik Field CTO, shares his key takeaways, highlights, and why this conference stands out as a top destination for the network automation community.
NANOG 92 has wrapped up, and Kentik’s Field CTO, Justin Ryburn, is here to recap the event. From Kentik-led sessions to IPv6 adoption, real-time routing analysis, and networking for AI data centers, learn about everything that made NANOG 92 an event to remember.
NANOG 91 gathered network professionals to discuss emerging trends and challenges in networking. The event featured keynotes and technical sessions focused on critical areas such as cloud-induced network complexities, the advent of network digital twins, IPv6 deployment, network automation, and BGP routing security. In this post, Justin Ryburn, Field CTO, summarizes his takeaways from the event.
We’re excited to announce a new collaboration between Kentik and Red Hat. This partnership will enable organizations to enhance network monitoring and management by integrating network observability with open-source automation tools.
BGP Flowspec is one of the critical technologies gaining traction in DDoS mitigation strategies. In this article, Justin Ryburn outlines the adoption rates and best practices of this emerging and effective DDoS mitigation tool.
From infrastructure and chipsets to data solutions and development tools, it’s clear that artificial intelligence will play a massive role in the future of the cloud. Read Justin Ryburn’s latest recap to learn about many of the exciting unveilings at Google Cloud Next 2024.
While many wifi access points and SD-WAN controllers have a rich data set available via their APIs, most do not support exporting this data via SNMP or streaming telemetry. In this post, Justin Ryburn walks you through configuring Telegraf to feed API JSON data into Kentik NMS.
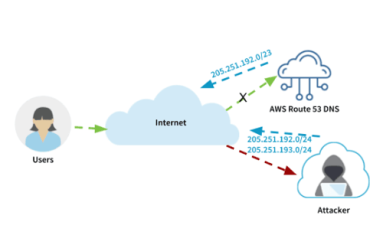
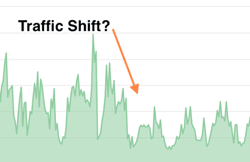
News broke last week that attackers attempted to steal cryptocurrencies from users of MyEtherWallet.com by using a BGP route hijack attack. Numerous Kentik Detect customers saw changes in their traffic patterns, allowing them to detect this attack. In this post, we look at how the attack worked and the visibility that Kentik Detect provided our customers.
Kentik Detect now incorporates IP reputation data from Spamhaus, enabling users to identify infected or compromised hosts. In this post we look at the types of threat feed information we use from Spamhaus, and then dive into how to use that information to reveal problem hosts on an ad hoc basis, to generate scheduled reports about infections, and to set up alerting when your network is found to have carried compromised traffic.
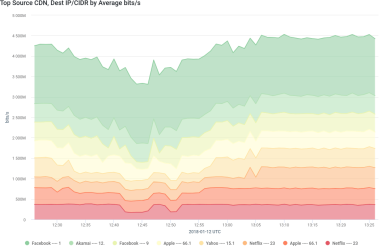
CDNs have been around for years, but they’ve gained new importance with the rise of video streaming services like Netflix and Hulu. As traffic from those sites soars, CDNs introduce new challenges for network operations teams at both service providers and enterprises. Kentik Detect’s new CDN Attribution makes identifying and tracking CDN traffic a whole lot easier. In this blog, we provide examples of how companies can implement this functionality.
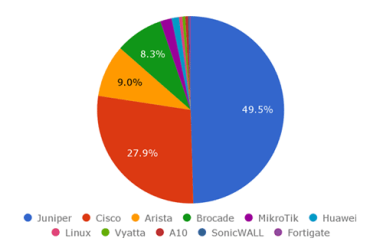
What brands of network devices are Kentik customers using? Where does their international traffic come from and go to? What’s the current norm for packet sizes and internet traffic protocols? Drawing on Kentik Detect’s ability to see and analyze network traffic, this post shares some intriguing factoids, and it sheds light on some of the insights about your own network traffic that await you as a Kentik customer.
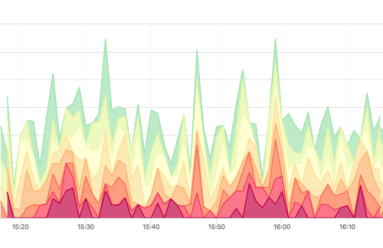
Media reports tell us that Cyber Monday marked a single-day record for revenue from online shopping. We can assume that those sales correlated with a general spike in network utilization, but from a management and planning perspective we might want to go deeper, exploring the when and where of traffic patterns to specific sites. In this post we use Kentik Detect to see what can be learned from a deeper dive into holiday traffic.
Managing network capacity can be a tough job for Network Operations teams at Service Providers and Enterprise IT. Most legacy tools can’t show traffic traversing the network and trend that data over time. In this post, we’ll look at how Kentik Detect changes all that with new Dashboards, Analytics, and Alerts that enable fast, easy planning for capacity changes and upgrades.
In today’s world of heterogeneous environments and distributed systems, APIs drive synergistic innovation, creating a whole that’s more powerful than the parts. Even in networking, where the CLI rules, APIs are now indispensable. At Kentik, APIs have been integral to our platform from the outset. In this post we look at how partners and customers are expanding the capabilities of their systems by combining Kentik with external tools.
Domain Name Server (DNS) is often overlooked, but it’s one of the most critical pieces of Internet infrastructure. As driven home by last October’s crippling DDoS attack against Dyn, the web can’t function unless DNS resolves hostnames to their underlying IP addresses. In this post we look at how combining Kentik’s software host agent with Dashboards in Kentik gives you the tools you need to ensure DNS availability and performance.
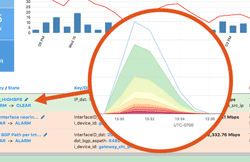
Major cyber-security incidents keep on coming, the latest being the theft from HBO of 1.5 terabytes of private data. We often frame Kentik Detect’s advanced anomaly detection and alerting system in terms of defense against DDoS attacks, but large-scale transfer of data from private servers to unfamiliar destinations also creates anomalous traffic. In this post we look at several ways to configure our alerting system to see breaches like the attack on HBO.
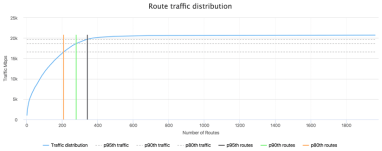
With BGP and NetFlow correlated into a unified datastore, Kentik Detect’s advanced analytics provide valuable insights for both engineering and sales. In this post we look into a fairly recent addition to Kentik Detect, Route Traffic Analytics. Especially useful for capacity planners and peering coordinators, RTA makes it easy to see how many unique routes are represented in a given percent of your traffic, which indicates the route capacity needed in your edge routers.
Can BGP routing tables provide actionable insights for both engineering and sales? Kentik Detect correlates BGP with flow records like NetFlow to deliver advanced analytics that unlock valuable knowledge hiding in your routes. In this post, we look at our Peering Analytics feature, which lets you see whether your traffic is taking the most cost-effective and performant routes to get where it’s going, including who you should be peering with to reduce transit costs.
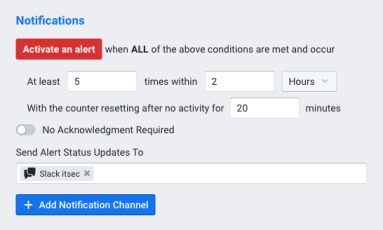
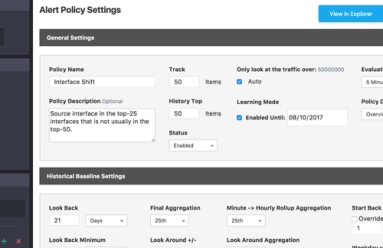
Operating a network means staying on top of constant changes in traffic patterns. With legacy network monitoring tools, you often can’t see these changes as they happen. Instead you need a comprehensive visibility solution that includes real-time anomaly detection. Kentik Detect fits the bill with a policy-based alerting system that continuously evaluates incoming flow data. This post provides an overview of system features and configuration.
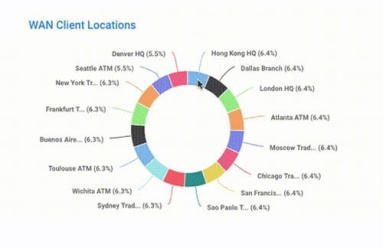
As one of 2017’s hottest networking technologies, SD-WAN is generating a lot of buzz, including at last week’s Cisco Live. But as enterprises rely on SD-WAN to enable Internet-connected services — thereby bypassing Carrier MPLS charges — they face unfamiliar challenges related to the security and availability of remote sites. In this post we take a look at these new threats and how Kentik Detect helps protect against and respond to attacks.