Kentik Blog: RPKI
























In this blog post, BGP experts Doug Madory of Kentik and Job Snijders of Fastly update their RPKI ROV analysis from last year while discussing its impact on internet routing security.
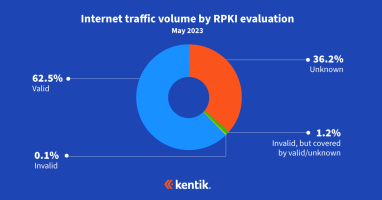
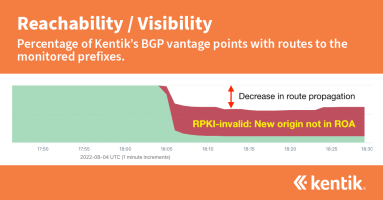
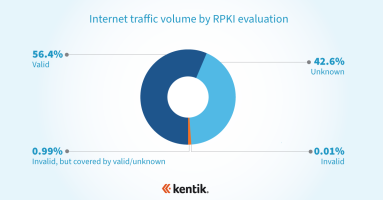
Our analysis from earlier this year estimated that the majority of internet traffic now goes to routes covered by ROAs and is thus eligible for the protection that RPKI ROV offers. This analysis takes the next step in understanding RPKI ROV deployment by measuring the rejection of invalid routes.
RPKI is the internet’s best defense against BGP hijacks. What is it? And how does it protect the majority of your outbound traffic from accidental BGP hijacks without posing a risk to legitimate traffic?
Kentik’s Greg Villain and Jason Philippon explain the basics of using Resource Public Key Infrastructure (RPKI) to protect against BGP prefix hijack attacks and stop them from propagating across the internet.
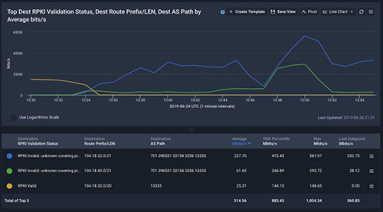
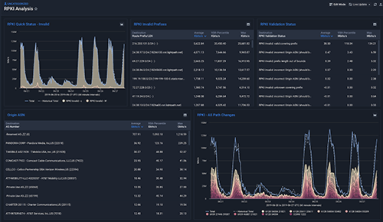
Crystal Li’s new Technical Guide walks you through new Kentik features for supporting Resource Public Key Infrastructure (RPKI), explaining Kentik’s new RPKI Validation Status and RPKI Quick Status dimensions.