Summary
Azure VNet flow logs significantly improve network observability in Azure. Compared to NSG flow logs, VNet flow logs provide broader traffic visibility, enhanced encryption status monitoring, and simplified logging at the virtual network level enabling advanced traffic analysis and a more comprehensive solution for modern cloud network management.
First introduced in early 2024, Azure Virtual Network (VNet) flow logs expand upon NSG flow logs, improving network visibility in Azure. Before VNet flow logs, NSG flow logs were the primary method to capture network traffic information. However, NSG flow logs lacked visibility of several key resources and were limited in scope and application. VNet flow logs fill in many of these visibility gaps and enhance network observability in Azure virtual networks.
Expanded capabilities
VNet flow logs both simplify and expand on the breadth of traffic monitoring by logging traffic at the virtual network level. This means that network traffic flowing through the workloads in a virtual network is logged, in contrast to NSG flow logs, which capture traffic flowing only through a specific network security group or NSG.
First, VNet flow logs simplify network monitoring by eliminating the need to enable multiple-level flow logging, which is necessary for NSG flow logging. NSG logs require configuring NSGs at both the subnet and network interface levels and skips important information when no NSG is applied.
In contrast, VNet flow logs provide a broader scope of visibility by enabling logging at the virtual network, subnet, or even network interface level, eliminating the need for NSGs to be attached to specific resources at the network security group level only.
Next, VNet flow logs provide more enhanced traffic analysis by identifying traffic allowed or denied by both NSG rules and the Azure Virtual Network Manager security admin rules. NSG flow logs capture information only at the network security group level.
Lastly, VNet flow logs also provide a form of encryption status monitoring, meaning that by using VNet flow logs, we can evaluate the encryption status of network traffic, especially in scenarios utilizing virtual network encryption.
In this short video, I give a quick overview of how VNet flow logs differ from and improve upon NSG flow logs (and you can find more quick overviews like this in our Kentik Bytes video collection):
How VNet flow logs work
VNet flow logs operate at Layer 4 and record network flows through a virtual network. They are collected at one-minute intervals and generally do not impact resource performance.
Like NSG flow logs, VNet flow logs are stored in JSON format, which isn’t new for Azure but is an important distinction from other cloud flow records like AWS VPC flow logs. JSON organizes log information into key-value pairs, providing a clear and consistent structure. That uniformity simplifies data parsing and analysis and enables more efficient extraction of relevant information, which is critical for network observability and integration with various third-party tools.
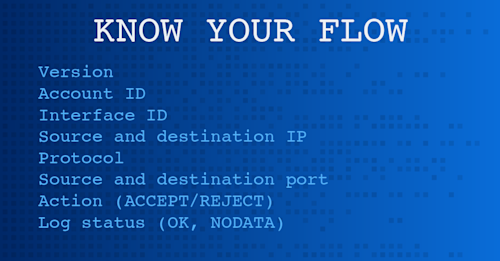
VNet flow logs include information such as source and destination IP, source and destination port, protocol, and the network interface identifier. They also include traffic direction, the flow state, the encryption state, and throughput information, a significant improvement over NSG flow logs.
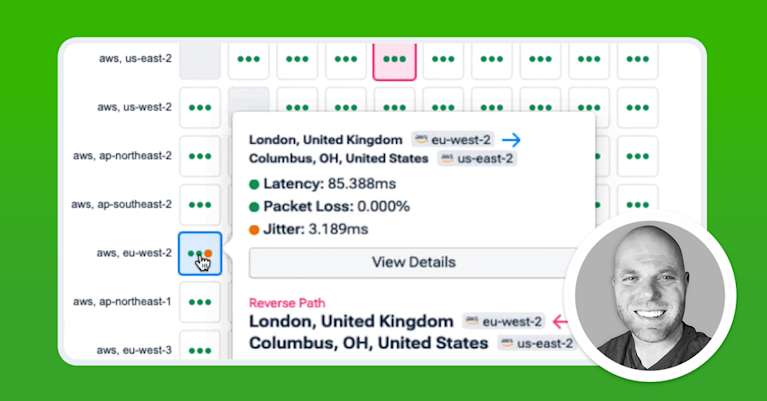
After flow records are generated, they are sent to Azure Storage, where they can be accessed and exported to visualization tools such as Kentik.
Uses for VNet flow logs
VNet flow logs have several specific uses for monitoring cloud traffic.
First, they’re used for general-purpose network monitoring, meaning they are used to identify unknown or undesired traffic, monitor traffic levels, and understand application behavior over the network.
Beyond that, VNet flow logs are used for usage optimization, such as identifying the top talkers in your cloud network, analyzing cross-region traffic, and forecasting capacity needs. Because VNet flow logs can be enabled at multiple levels, we can use them to monitor various services, such as Azure Firewall, VPN gateways, or ExpressRoute gateways.
(NSG flow logs are limited to monitoring traffic through resources with associated NSGs, which means they provide an incomplete picture of cloud network traffic.)
From a security perspective, these logs are used for compliance, such as ensuring network isolation, verifying encryption standards, and adhering to organizational access rules. In fact, they can also be used for security analysis tasks, such as analyzing network flows from compromised IPs, detecting intrusions, recognizing suspicious traffic patterns, and so on. When used along with an SIEM or IDS tool, VNet flow logs can help provide advanced threat detection.
NSG flow logs don’t provide information regarding the encryption status of network traffic, making this use case unique to VNet flow logs.
Also, from a security perspective, VNet flow logs provide more enhanced traffic analysis by identifying traffic allowed or denied by both NSG rules and the Azure Virtual Network Manager security admin rules. NSG flow logs, on the other hand, capture traffic decisions only based on NSG rules, lacking insights into other security configurations.
Comparing NSG and VNet flow logs side-by-side
Because VNet flow logs fill many of the visibility gaps of NSG flow logs, it’s helpful to compare supported features and visibility side-by-side.
| Scope | NSG flow logs | VNet flow logs |
|---|---|---|
| Identifying virtual network encryption | No | Yes |
| Azure Application Gateway | No | Yes |
| ExpressRoute Gateway | No | Yes |
| VPN Gateway | No | Yes |
| Virtual machine scale sets | Yes | Yes |
| Bytes and packets in stateless flows | No | Yes |
| Azure API management | No | Yes |
| Azure Virtual Network Manager | No | Yes |
How to analyze VNet flow logs (Azure-native vs. third-party)
Azure sends VNet flow log data to Azure Storage, where you can export it to the tool you prefer for dashboards, troubleshooting, and security investigations.
- Azure-native: Use Traffic Analytics / Log Analytics to build dashboards and basic flow summaries.
- Kentik (network observability): Ingest flow logs from your Azure storage account to run fast traffic analytics, correlate flows with cloud metadata, and operationalize monitoring across Azure and multi-cloud networks. For detailed setup instructions, see our Kentik for Azure knowledgebase article.
- SIEM / IDS: Export flow logs to security tooling for detection workflows and investigations.
Tip: Don’t run NSG flow logs and VNet flow logs on the same underlying workloads. Microsoft recommends disabling NSG flow logs before enabling VNet flow logs to avoid duplicate records and extra costs.
Using Kentik to monitor VNet traffic
To use Kentik with VNet flow logs, export flow logs to an Azure storage account and configure a Kentik Azure cloud export to ingest flow logs and relevant metadata. Once configured, Kentik can be used to monitor Azure network traffic, visualize utilization, and support performance and security workflows. For detailed setup instructions, see our Kentik for Azure knowledgebase article.
Kentik provides comprehensive Azure observability
Azure VNet flow logs mark a significant advancement in network observability for Azure environments. They address many of the limitations of NSG Flow Logs and offer a comprehensive solution for monitoring and analyzing network traffic. Kentik leverages VNet flow logs to capture traffic at the virtual network level, extending visibility to a wide range of Azure resources. By using VNet flow logs, Kentik provides unparalleled insight into network behavior and performance.
Related resources about cloud flow logs
For more on cloud flow logs, see our post “Understanding the Differences Between Flow Logs on AWS and Azure” and our Kentipedia article, “What are VPC Flow Logs?”
FAQ: Monitoring VNet traffic with flow logs
How do I monitor VNet traffic in Azure?
To monitor VNet traffic, enable Azure Virtual Network (VNet) flow logs in Azure Network Watcher and send flow data to Azure Storage. From there, analyze and alert on traffic patterns using a tool such as Kentik, or export the logs to your SIEM/IDS or another visualization platform. Kentik can ingest Azure flow logs from your storage account and help you investigate traffic by source/destination, ports, direction, and throughput across Azure and hybrid environments.
What are VNet flow logs?
VNet flow logs are an Azure Network Watcher feature that logs information about IP traffic flowing through a virtual network. The flow data is sent to Azure Storage for analysis and export.
What’s the difference between VNet flow logs and NSG flow logs?
NSG flow logs capture traffic through a specific network security group, while VNet flow logs operate at the virtual network scope and provide broader visibility across supported workloads. VNet flow logs also include capabilities like identifying traffic evaluated by Azure Virtual Network Manager security admin rules and tracking encryption status in supported scenarios.
Are NSG flow logs being retired?
Yes. Microsoft has announced that NSG flow logs will be retired on September 30, 2027, and you can no longer create new NSG flow logs after June 30, 2025. Microsoft recommends migrating to VNet flow logs.
Should I enable both NSG flow logs and VNet flow logs?
No. Microsoft recommends disabling NSG flow logs before enabling VNet flow logs on the same workloads to avoid duplicate traffic recording and additional costs.
How often are VNet flow logs collected, and do they affect performance?
VNet flow logs operate at Layer 4 and are collected at one-minute intervals through the Azure platform. Microsoft states they don’t affect your Azure resources or network traffic.
What fields do VNet flow logs include?
VNet flow logs include the network interface identifier and 5-tuple information (source/destination IP, ports, protocol) plus traffic direction, flow state, encryption state, and throughput information.
Can VNet flow logs help me track encrypted vs unencrypted traffic?
Yes. VNet flow logs include an encryption state field that can help evaluate whether flows are encrypted in scenarios using virtual network encryption.
How do I export VNet flow logs to Kentik?
Export VNet flow logs to an Azure storage account, then configure Kentik’s Azure cloud export to ingest flow logs and metadata from that account. Kentik can then be used to monitor Azure network traffic, visualize utilization, and support troubleshooting and security workflows.
What are the most common use cases for VNet flow logs?
Common use cases include identifying unknown traffic, monitoring bandwidth consumption, understanding application behavior by filtering on IP and port, finding top talkers and cross-region traffic, forecasting capacity, validating segmentation and compliance, and supporting security investigations.