How to Harden Zero-Trust Cloud Network Policy with Kentik

Summary
Zero trust in the cloud is no longer a luxury in the modern digital age but an absolute necessity. Learn how Kentik secures cloud workloads with actionable views of inbound, outbound, and denied traffic.
Is managing the security of your cloud network a technical nightmare? The evolving nature of cloud workloads forces you to focus on the visibility of your security posture, but figuring out where to begin can be daunting. This is where a zero-trust cloud network policy can make a big difference.
Zero trust is based on the assumption that everything is potentially a threat, which means there can be no implicit trust. It doesn’t matter where a request is coming from or from which device; it’s assumed to be potentially unsafe.
In this article, you’ll learn all about zero-trust cloud network policies, why they’re important to enterprises, and how Kentik can help you secure one.
What is a zero-trust framework?
For a long time, cybersecurity was based on the concept of trust but verify, which worked when threats existed outside the network. This traditional security model operated on the assumption that the external network was not to be trusted, while everything within it was granted implicit trust. In other cases, network engineers who moonlit as security engineers often focused only (or mainly) on perimeter security. However, changes such as remote work, bring your own device (BYOD), and cloud computing have made this model obsolete. The perimeter is now much more fluid, and the old bad guys out, good guys in philosophy doesn’t work.
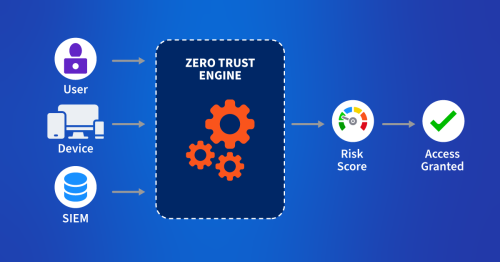
This is where zero trust comes in. Zero trust helps to mitigate the ever-present threat of malicious insiders (i.e., users who misuse the authorized access they’ve been granted). It achieves this by individually evaluating every request, regardless of where it originated.
Moreover, zero trust significantly enhances cybersecurity mitigation against cyber threats. This means that within a zero-trust environment, the network is not dependent on different security solutions; instead, it becomes a security control by assuming every request is potentially malicious.
The principles of zero trust closely align with the mandates and guidelines set out in regulatory frameworks and standards like the General Data Protection Regulation (GDPR), Payment Card Industry Data Security Standard (PCI DSS), and Health Insurance Portability and Accountability Act (HIPAA). Therefore, following a zero-trust policy for cybersecurity can help you avoid costly fines for noncompliance.
Additionally, zero trust streamlines employee onboarding by eliminating traditional bureaucratic barriers, enabling quicker integration of new hires. Employees can use personal devices for the initial onboarding processes, and chief information security officers (CISOs) can rest easy knowing the zero-trust engine is evaluating and assessing every request against its trust policies:
While embracing a zero trust policy can reap many rewards, it comes with unique challenges. For instance, implementing a network policy that spans both on-premise and cloud networks can be challenging, and you’ll probably consider using a solutions provider that can cover as much of your network infrastructure as possible. This becomes particularly crucial when adopting a multicloud strategy, which balances cost savings among different cloud providers and their products. However, this approach is often complicated since you have to manage all the other services offered by the various providers.
The key to implementing a zero-trust network lies in translating the principles into actionable technical controls that can fortify your cloud environments.
Imagine a scenario where you’re responsible for the cloud environment of a major fintech company. The holiday season is about to begin, and you want to lock down the environment against cybercriminals who are all too eager to compromise it. Following the principles of zero trust seems like a great place to start, but how do you actually implement it? What should you focus on, and how do you do it without getting bogged down in the complexities of it all?
This is where solutions like Kentik can help. The Kentik Network Observability Platform gives companies insights into their cloud environments, enabling them to detect security issues, establish baselines for network activity, understand how traffic flows through the network and public internet, and see what SaaS applications are in use.
In the next section, you’ll learn how easy it is to use Kentik to lock down security groups and cloud access and monitor rejected traffic volume.
Implementing a zero-trust cloud network policy with Kentik
Let’s take a look at how Kentik can enable a zero-trust network in the cloud.
Lock down security groups
Security groups are often the entry points into cloud workloads. The rules defined in security groups dictate how and where workloads can be accessed.
A frequent oversight in cloud environments is opening up security groups to troubleshoot issues and then forgetting to close them. This violates zero-trust principles and becomes a vulnerability that attackers can exploit.
Locking down security groups is essential but far from easy, especially given how quickly cloud environments change. Thankfully, Kentik can help to automate and streamline the process.
Following are the steps you can take in Kentik to lock down your cloud environment:
If you don’t already have one, create a Kentik account and log in.
Once you’ve configured one of your cloud providers to send flow logs to Kentik, you should be able to see directional data flow on your dashboard.
Navigate to the Dashboard to get a 360-degree view of your cloud posture, and use Kentik’s filtering options to identify open security groups that should be locked down.
Now, you can harden the security group settings to a more restrictive state, allowing only the needed traffic. This step is essential as it creates a baseline for expected and/or unexpected traffic patterns.
Then create alerts that inform you if the security groups deviate from your set baseline.
By enabling these settings, Kentik continually monitors your cloud environment and prevents any future instances of network security groups from being left open accidentally, misconfigured security groups, or previously unknown attack vectors.
Monitor rejected traffic volume and update cloud policies as needed
The cloud’s noisy nature means filtering out data signals indicating a threat is essential. A high volume of rejected traffic can reveal many things, including a potential cyber threat trying every entry point to gain access. Properly performing policies will deny all traffic except the tiny sliver of allowed traffic. Either way, a good zero-trust network policy should continually be adjusted in response to changing conditions and threats.
Striking the balance between securing your network and allowing productivity can be challenging, but Kentik can help. Kentik allows you to analyze rejected data volumes and fine-tune policies in real time. Essentially, it is a balance of allowing access while also maintaining a policy of least privilege.
To do so, you just need to log into your Kentik account and navigate to the dashboard. There, you can look for instances of rejected traffic and any potential spikes.
Kentik’s analytical features allow you to dive deep into trends and isolate their origins and where the traffic was headed. This enables you to identify both potential threats and bottlenecks within your network.
Once you’ve identified the issue causing problems, navigate to the cloud policy settings within Kentik and fine-tune the specified policies. Make sure you harden the policy more if you feel that the rejected traffic indicates a broader threat.
Finally, create alerts that can notify you in case of surges of rejected traffic. This helps you proactively respond before a potential threat can materialize.
Using data to fine-tune security controls is a vital characteristic of a zero-trust network. Kentik makes this entire process intuitive and easy to manage, enabling you to balance usability and security.
Locking down cloud access
The principle of least privilege is one of the most fundamental aspects of zero trust, but it can also be one of the most challenging to implement in the cloud. Every user, workload, and API call needs permissions to function, which can become hard to manage over time. However, the consequence of not locking down your cloud environment is that you could potentially leave overly permissive access open that an attacker can misuse.
Applying the principles of least privilege in a cloud environment is even more challenging due to cloud resources’ dynamic and ephemeral nature. This is where Kentik adds value by providing an easy way to restrict access without bogging the user down.
To lock down cloud access with Kentik, navigate to the Dashboard and identify which users need to be able to access your cloud resources. Remember to create alerts that notify you if other user activities are observed (ie if any actors other than your created baseline are observed).
Kentik provides users with an intuitive way of restricting access to the bare minimum required and enforcing zero-trust principles within the cloud.
Audit access to cloud resources
Your cloud environment can house some sensitive assets, like client databases or signed documents uploaded to an Amazon Simple Storage Service (Amazon S3) bucket. It’s essential that you maintain constant vigilance over these assets, as unauthorized access can lead to a data breach.
For zero trust to be effective, it’s critical to have real-time insights into who is performing which actions and where within your cloud environment. Unfortunately, given the sheer volume of activities that can take place, it’s difficult to extract any meaningful information.
Early detection of suspicious activity can mean the difference between a simple alert and a full-on data breach. Kentik offers a simple way of extracting useful information without drowning you in it. All you need to do is navigate to your dashboard and analyze Kentik’s access logs to get an overview of what is happening within your cloud environment.
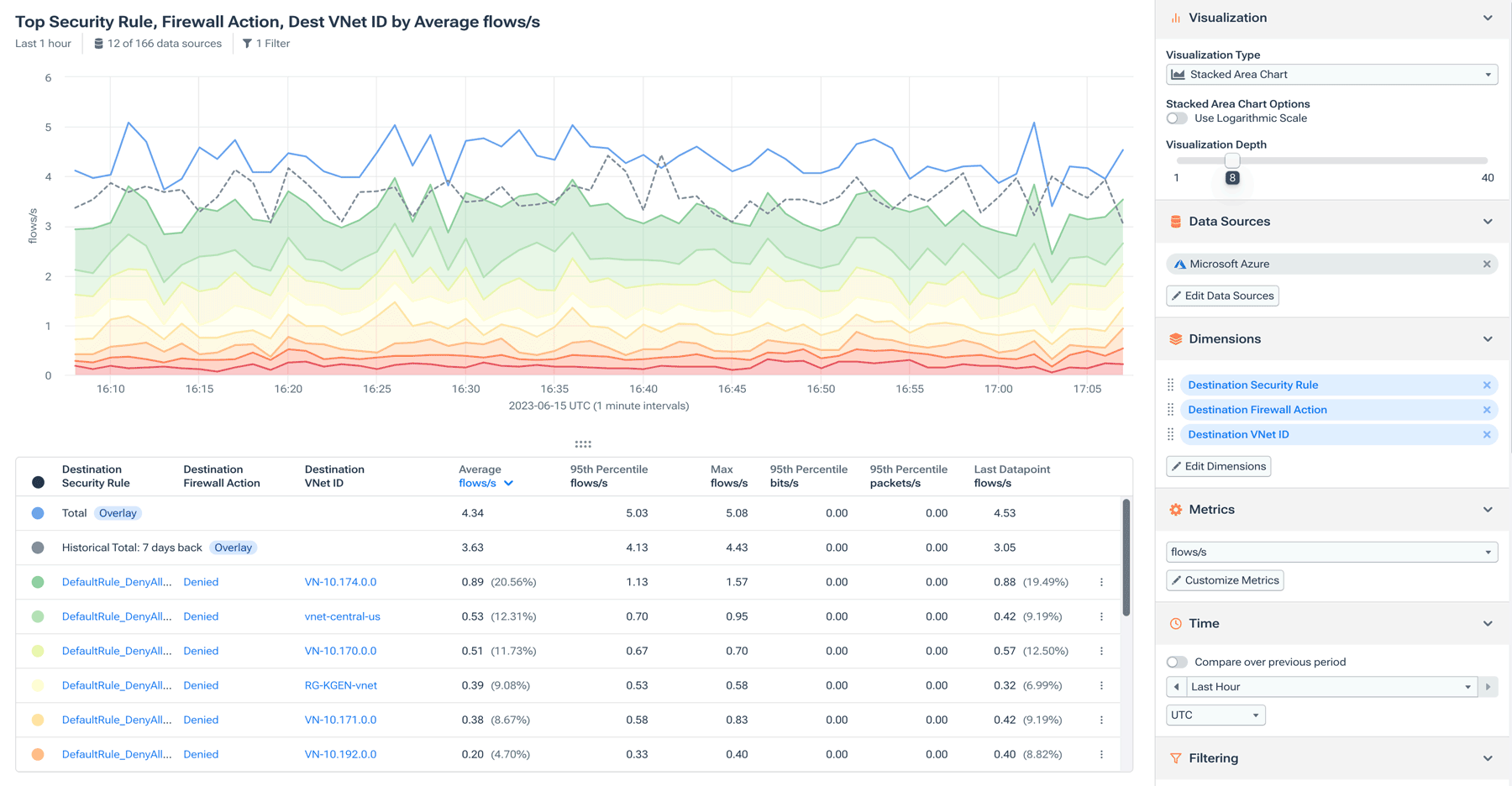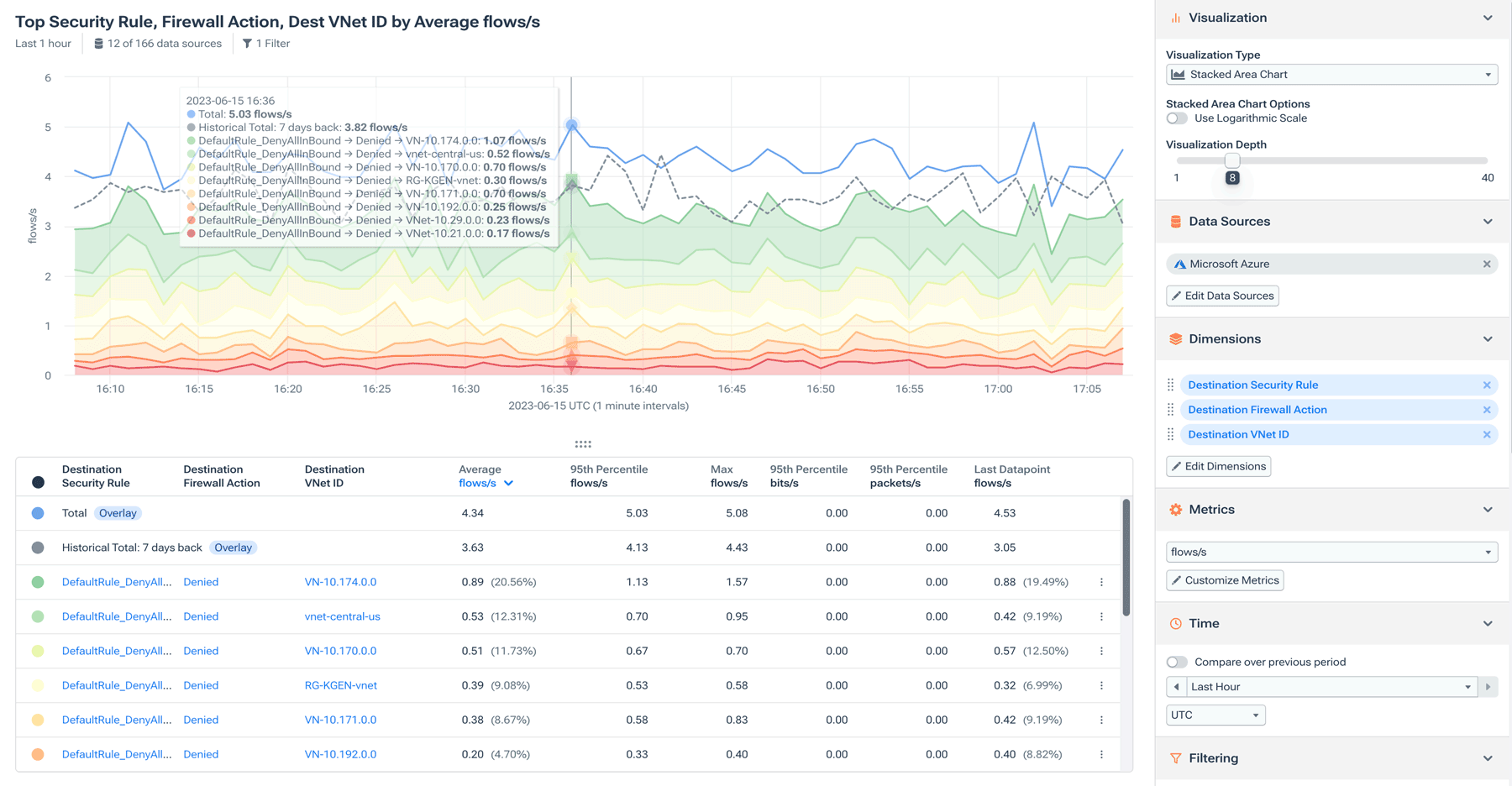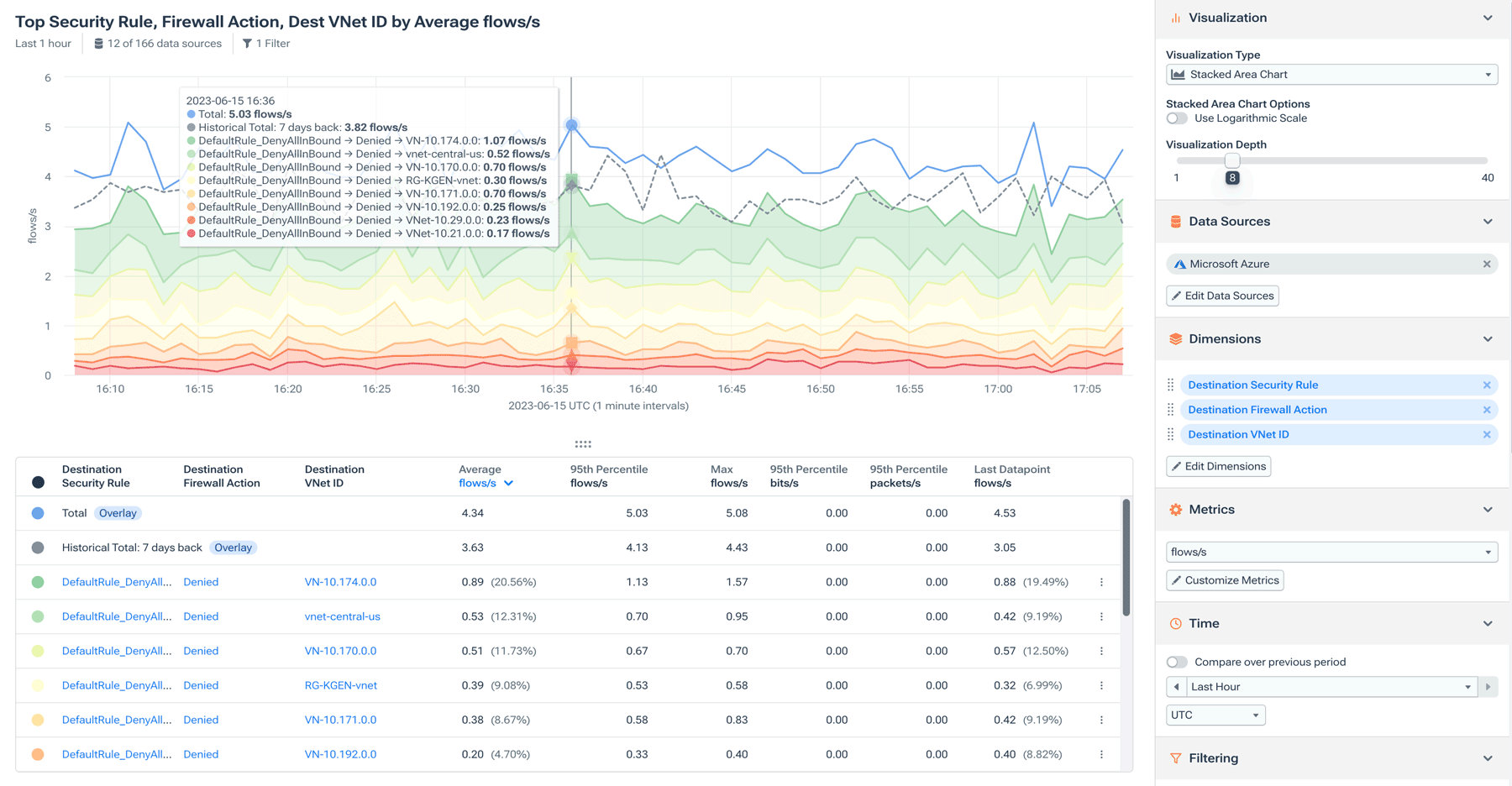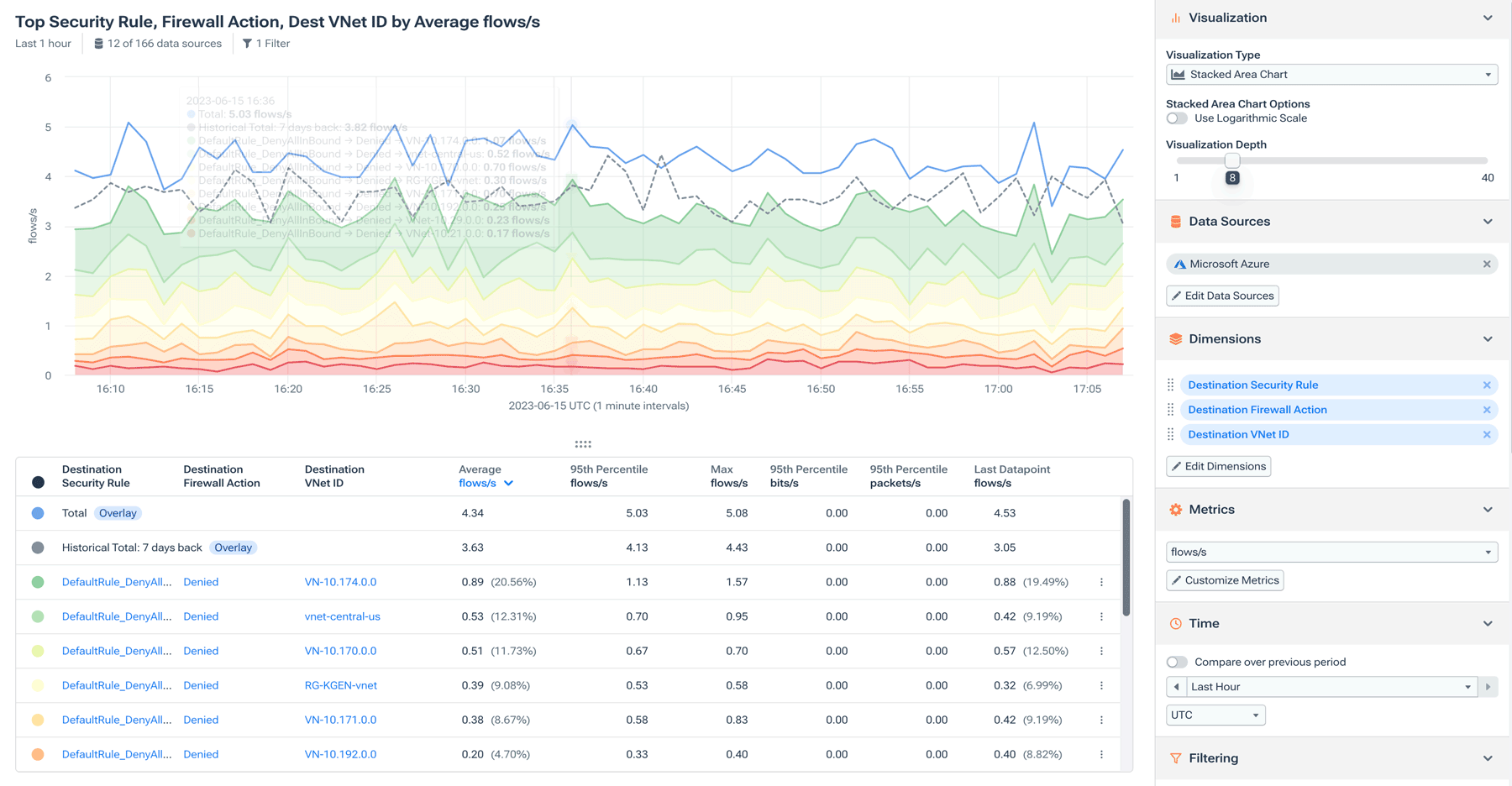
It’s recommended that you have an idea of what constitutes normal within your environment so that it’s easier to identify any deviations from the regular baseline.
Kentik also allows you to drill down using various criteria, such as focusing on a particular resource, time frame, or user. This enables you to get meaningful context on events and audit them.
You can also set up alerts for particular patterns or access attempts for proactive security monitoring and audits.
Auditing can change from a cumbersome, manual activity to a graphical, intuitive task with Kentik. Its interface helps you identify any activity that warrants further investigation and gives you detailed visibility and understanding of your environment.
Conclusion
The zero-trust framework marked a significant advancement in the evolution of network security principles. This framework incorporates the following fundamental principles:
- Users and devices on a network should not be trusted but verified.
- Every user should get only the necessary access to fulfill their purpose.
- Continuous monitoring of access logs is necessary to identify incorrect access patterns.
Zero trust is an evolving field within cloud security that requires the proper tooling to be appropriately implemented. Kentik helps users enforce zero-trust principles from a unified interface without drowning in technical complexities.
Zero trust in the cloud is no longer a luxury in the modern digital age but an absolute necessity. By using Kentik, you can enforce zero trust with complete confidence and strike that magic balance between security and usability within the cloud.