Kentik Blog
























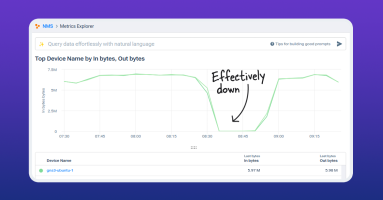
Kentik NMS collects valuable network data and then transforms it into usable information — information you can use to drive action.
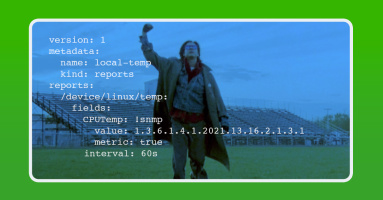
Out of the gate, NMS collects an impressive array of metrics and telemetry. But there will always be bits that need to be added. This brings me to the topic of today’s blog post: How to configure NMS to collect a custom SNMP metric.
While many wifi access points and SD-WAN controllers have a rich data set available via their APIs, most do not support exporting this data via SNMP or streaming telemetry. In this post, Justin Ryburn walks you through configuring Telegraf to feed API JSON data into Kentik NMS.
Streaming telemetry is the future of network monitoring. Kentik NMS is a modern network observability solution that supports streaming telemetry as a primary monitoring mechanism, but it also works for engineers running SNMP on legacy devices they just can’t get rid of. This hybrid approach is necessary for network engineers managing networks in the real world, and it makes it easy to migrate from SNMP to a modern monitoring strategy built on streaming telemetry.
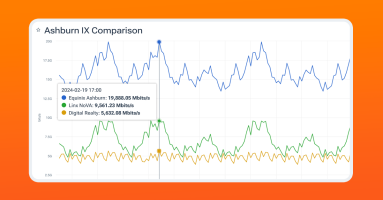
Kentik users can now correlate their traffic data with internet exchanges (IXes) and data centers worldwide, even ones they are not a member of – giving them instant answers for better informed peering decisions and interconnection strategies that reduce costs and improve performance.
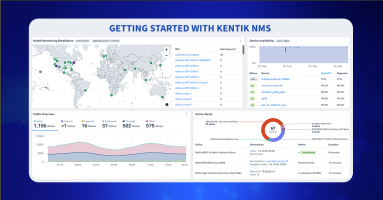
Kentik NMS is here to provide better network performance monitoring and observability. Read how to get started, from installation and configuration to a brief tour of what you can expect from Kentik’s new network monitoring solution.
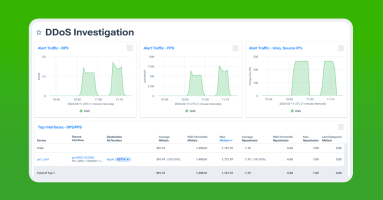
DDoS attacks disrupt services and damage reputations, with motivations ranging from political to personal. These attacks can also mask more severe security breaches, so early detection and mitigation are crucial. Learn how Kentik provides a solution by analyzing enriched NetFlow data to identify and mitigate DDoS threats.
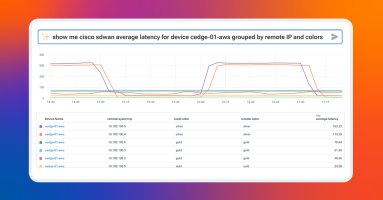
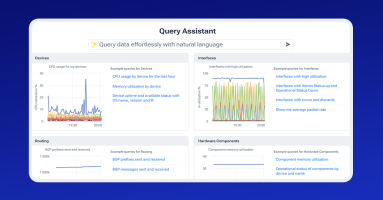
Kentik Journeys uses an AI-based, large language model to explore data from your network and troubleshoot problems in real time. Using natural language queries, Kentik Journeys is a huge step forward in leveraging AI to democratize data and make it simple for any engineer at any level to analyze network telemetry at scale.
Kentik NMS has launched and is setting sail in familiar waters. Monitoring with SNMP and streaming telemetry is only the first leg of the journey. In short order, we’ll unfurl additional options, increasing NMS’s velocity and maneuverability.
We’re bringing AI to network monitoring and observability. And adding new products to Kentik, including a modern NMS, to simplify troubleshooting complex networks.