Kentik Blog
























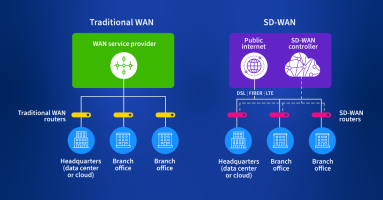
SD-WAN is a reliable, fast, and secure WAN network. In this guide, you’ll learn some best practices for planning, monitoring, analyzing, and managing modern SD-WANs.
Discover how Kentik’s network observability platform aids in troubleshooting SaaS performance problems, offering a detailed view of packet loss, latency, jitter, DNS resolution time, and more. Phil Gervasi explains how to use Kentik’s synthetic testing and State of the Internet service to monitor popular SaaS providers like Microsoft 365.
No matter how much prevention you have, serious security incidents will inevitably occur. Read the next article in our security series that covers how to understand cyberattacks as quickly as possible so that your organization can respond swiftly.
When your business is all about providing cloud services at the edge, optimizing the quality of your network connectivity is paramount to customer success. Learn how StackPath saved $3 million and optimized their network performance by using Kentik.
Organizations are under constant attack, and it’s critical to reduce the time it takes to detect attacks to minimize their cost. This first article in our new security series dives deep into how Kentik helps customers before, during, and after a cyberattack.
Kentik customers can now map traffic and performance of Microsoft Azure infrastructure with visibility into Azure Firewalls, Express Routes, Load Balancers, VWANs, and more in Kentik Cloud.
Today’s modern enterprise WAN is a mix of public internet, cloud provider networks, SD-WAN overlays, containers, and CASBs. This means that as we develop a network visibility strategy, we must go where no engineer has gone before to meet the needs of how applications are delivered today.
Streaming telemetry holds the promise of radically improving the reliability and performance of today’s complex network infrastructures, but it does come with caveats. In the first of a new series, Kentik CEO Avi Freedman covers streaming telemetry’s history and original development.
API monitoring is the process of keeping tabs on the performance of your REST APIs. Learn how Kentik’s API monitoring tools let you identify bottlenecks, spot performance drops, and maintain API availability. Learn more in this API monitoring how-to tutorial.