Kentik Blog
























Limited visibility into network performance across multi-clouds frustrates even the best teams. That’s why we’re thrilled to announce enhanced AWS and GCP support for Kentik Cloud, enabling network, cloud, and infrastructure teams to rapidly troubleshoot and understand multi-cloud traffic.
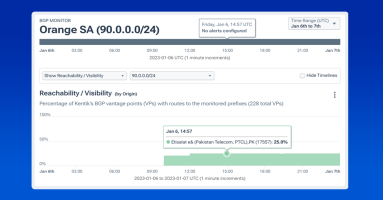
Stretching back to the AS7007 leak of 1997, this comprehensive blog post covers the most notable and significant BGP incidents in the history of the internet, from traffic-disrupting BGP leaks to crypto-stealing BGP hijacks.
Cloud network reliability has become a catch-all for four related concerns: availability, resiliency, durability, and security. In this post, we’ll discuss why NetOps plays an integral role in delivering on the promise of reliability.
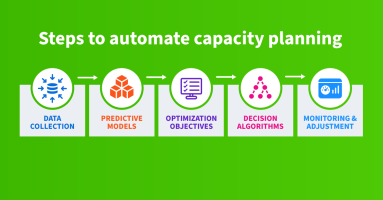
By automating capacity planning for IP networks, we can achieve cost reduction, enhanced accuracy, and better scalability. This process requires us to collect data, build predictive models, define optimization objectives, design decision algorithms, and carry out consistent monitoring and adjustment. However, the initial investment is large and the result will still require human oversight.
As organizations continue to shift their operations to cloud networks, maintaining the performance and security of these systems becomes increasingly important. Read on to learn about incident management and the tools and strategies organizations can use to reduce MTTR and incident response times in their networks.
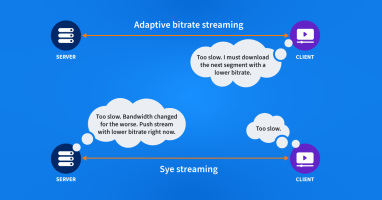
Live sports have moved to the internet and are now streaming instead of being broadcast. Traditional streaming protocols have a built-in delay that challenges the experience of a live game. Amazon Prime has found a solution by combining a new protocol with a very distributed CDN.
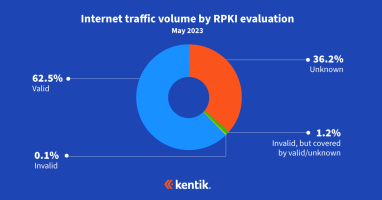
In this blog post, BGP experts Doug Madory of Kentik and Job Snijders of Fastly update their RPKI ROV analysis from last year while discussing its impact on internet routing security.
Peering evaluations are now so much easier. PeeringDB, the database of networks and the go-to location for interconnection data, is now integrated into Kentik and available to all Kentik customers at no additional cost.
We access most of the applications we use today over the internet, which means securing global routing matters to all of us. Surprisingly, the most common method is through trust relationships. MANRS, or the Mutually Agreed Norms for Routing Security, is an initiative to secure internet routing through a community of network practitioners to facilitate open communication, accountability, and the sharing of information.
Didn’t have time to watch our two recent webinars on the top trends network operators need to know about to be successful in 2023? We’ve got you covered. Let’s look at the biggest takeaways and break down some key concepts.