Kentik Blog
























Encryption and cloud adoption are creating hurdles for network performance monitoring vendors. To survive, solutions must evolve or die.
In episode 2 of Network AF, Nina Bargisen joins Avi to discuss network interconnection and peering, her career in networking, and mentorship and diversity issues in network engineering.
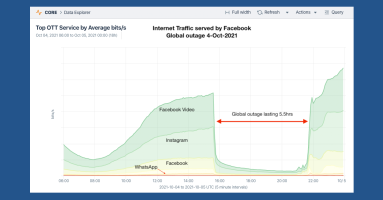
Facebook suffered a historic and nearly six-hour global outage on October 4. In this post, we look at Kentik’s view of the outage.
Today our Co-founder and CEO Avi Freedman launches Network AF, his new podcast. Come and listen to all-things networking, cloud, the internet and more. The first episode is out today!
Last Tuesday, September 14th was the second Tuesday of the month, and for anyone running a network or working in IT, you know what that means: another Microsoft Patch Tuesday. Doug Madory looks at how the resulting traffic surge can be analyzed using Kentik’s OTT Service Tracking.
Adding more bandwidth from the business to the cloud is like adding more cowbell to Grazing in the Grass. In many cases, it won’t improve the end-user experience when latency is the real problem.
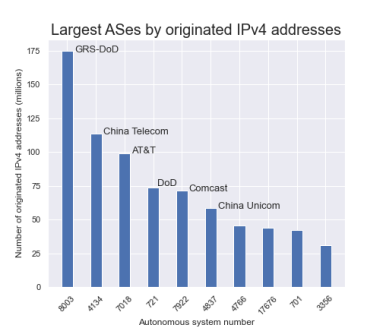
There has been a new development in The Mystery of AS8003.
As you may recall, this was the AS number registered to a defunct company in Florida that appeared earlier this year in the global routing table announcing over 175 million IPv4 addresses belonging to the US Department of Defense.
Well, that just changed.
A company with thousands of remote employees connecting to the same SaaS applications will randomly experience slowness. How can we troubleshoot this sluggishness?
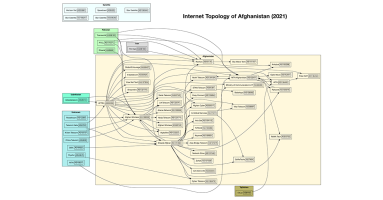
As the last US military aircraft depart Kabul, so closes a chapter of U.S. involvement in the country. Will it also end a period of growth of the domestic internet in Afghanistan?
If you haven’t heard of network observability, you soon will, and you’ll be hearing it a lot. Some say it is just marketing hype and that networks have always been observable. This post will explore why that’s not the case.