Kentik Blog
























SD-WAN promises to boost agility, security, performance, and management and operations. However, without effective network visibility, the path to a successful deployment is difficult to achieve. In this post, we provide considerations for solving SD-WAN visibility challenges.
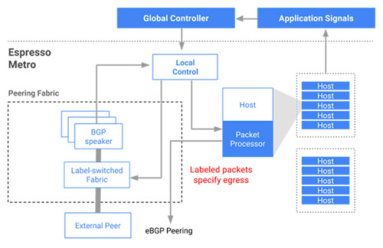
Google is investing and innovating in SD-WAN. In this post, Kentik CTO Jonah Kowall highlights what Google has been up to and how Google’s SD-WAN work can apply to the typical organization.
Kentik recently hosted a virtual panel with network leaders from Dropbox, Equinix, Netflix and Zoom and discussed how they are scaling to accommodate the unprecedented growth in network traffic during COVID-19. In this post, we highlight takeaways from the event.
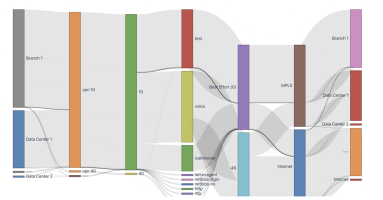
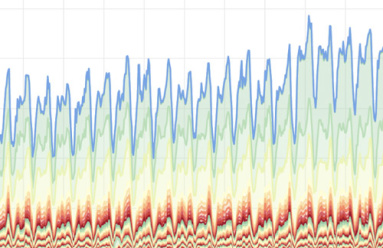
At Kentik, we’re always interested in monitoring trends in network traffic. This helps to inform our community and customers globally about potential opportunities and threats to network operations. In this ongoing blog post, we’ll provide updates to trends in traffic in correlation with COVID-19.
When more of the workforce shifts to working remotely, it puts new and different strains on the infrastructure across different parts of the network. In this post, we discuss strategies for managing surges in network traffic coming from remote employees and share information on how Kentik can help.
The most complex point of today’s networks is the edge, where there are more protocols, diverse traffic, and security exposure. The network edge is also a place where Kentik provides high value. In this post, we discuss how to implement Kentik in your data center.
Today we announced an evolutionary leap forward for NetOps, solving for today’s biggest network challenge: effectively managing hybrid complexity and scale, at speed. In this post, Kentik CTO Jonah Kowall discusses what’s new with the latest release of the Kentik Platform.
What is the difference between SNMP and flow technologies? Who uses the data sets? And what benefits do these technologies bring to network professionals? In this post, we explain how and why to use both.
Most DevOps teams use Grafana for reporting and data analysis for operational use cases spanning many monitoring systems. Grafana is a place these teams go to get answers to many questions. In this post, Kentik CTO Jonah Kowall discusses how Grafana became so popular and how the Kentik plugin for Grafana has new enhancements and features to help teams across the IT organization.