Kentik Blog
























Traditional monitoring tools for managing application performance in private networks are not well-suited to ensuring the performance, reliability and security of SaaS applications. In this post, ACG analyst Stephen Collins makes the case for why enterprise IT managers need to employ a new generation of network visibility and big data analytics tools designed for the vast scale of the Internet.
College, university and K-12 networking and IT teams who manage and monitor campus networks are faced with big challenges today. In this post, we take a deeper look at the challenges and provide requirements for a cost-effective network monitoring solution.
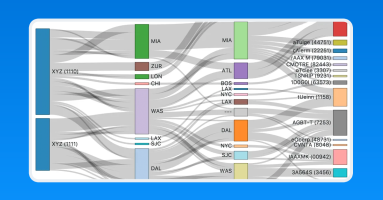
Sankey diagrams were first invented by Captain Matthew Sankey in 1898. Since then they have been adopted in a number of industries such as energy and manufacturing. In this post, we will take a look at how they can be used to represent the relationships within network data.
The adoption of hyperscale principles presents data center operators with massive scale visibility challenges. Yet it’s inevitable. In this post, ACG analyst Stephen Collins discusses why operators need to prepare for the inevitable by acquiring and mastering the new tools needed to assure the performance, reliability and security of these applications.
Industry 4.0 is the next phase in the digitization of the manufacturing sector. In this post, ACG Research’s Principal Analyst Stephen Collins looks at the major implications that Industry 4.0 will create for enterprise IT systems, software and network infrastructure, and how to model, monitor and control it all.
Kentik Detect now incorporates IP reputation data from Spamhaus, enabling users to identify infected or compromised hosts. In this post we look at the types of threat feed information we use from Spamhaus, and then dive into how to use that information to reveal problem hosts on an ad hoc basis, to generate scheduled reports about infections, and to set up alerting when your network is found to have carried compromised traffic.
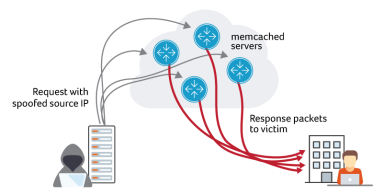
Attackers are using memcached to launch DDoS attacks. Multiple Kentik customers have reported experiencing the attack activity. It started over the weekend, with several external sources and mailing lists reporting increased spikes on Tuesday. In this blog post, we look at what our platform reveals about these attacks.
While defining digital transformation strategies is a valuable exercise for C-level executives, CIOs and IT managers also need to adopt a pragmatic and more tactical approach to “going digital.” That starts with acquiring tools and building the new skills needed to ensure business success and profitability in the face of digital disruption. In this post, ACG Principal Analyst Stephen Collins looks at how to manage it all.
IoT represents a massive threat to network infrastructure, as seen in widely publicized IoT-based DDoS attacks like Mirai. So what needs to happen to safeguard our devices and networks from participating in these botnet attacks? And how can IoT device originated attacks get quickly identified and stopped by network operators? In this post, we discuss scalable IoT DDoS protection.