Kentik Blog
























A new EMA report on network analytics is full of interesting takeaways, from reasons for deployment to use cases after analytics are up and running. In this post, we look specifically at the findings around adoption to see why and how organizations are leveraging network analytics.
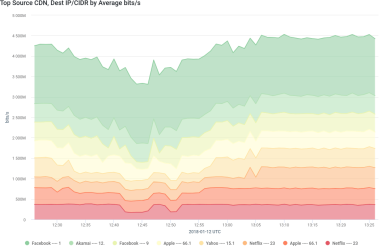
CDNs have been around for years, but they’ve gained new importance with the rise of video streaming services like Netflix and Hulu. As traffic from those sites soars, CDNs introduce new challenges for network operations teams at both service providers and enterprises. Kentik Detect’s new CDN Attribution makes identifying and tracking CDN traffic a whole lot easier. In this blog, we provide examples of how companies can implement this functionality.
If you’ve spent any amount of time with Kentik Co-founder and CEO Avi Freedman, you know he’s a networking nerd at heart. You may have also heard of his past (and sometimes current pastime) as a high-stakes poker player. Now, in merging two of Avi’s passions together, we’ve launched Kentik Poker!
This week Verizon invested in an Open Network Automation Platform membership. Oil company Shell talked about the success of its predictive analytics. The Chicago Bears said they’re all in on hyperconverged infrastructure. And a Google Cast protocol bug caused temporary Wi-Fi outages. More stories after the jump…
As IoT adoption continues, enterprises are finding a massive increase in the number of devices and the data volumes generated by these devices on their networks. Here’s how enterprises can use network monitoring tools for enhanced visibility into complex networks.
From telcos, to financial services, to tech companies, we asked 30 of our peers one question: What are your 2018 networking predictions? Yes, it’s a broad question. But respondents (hailing from network, data center, and security operations teams) surfaced five main predictions for the year ahead.
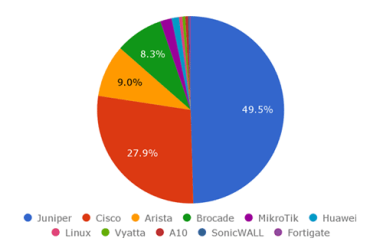
What brands of network devices are Kentik customers using? Where does their international traffic come from and go to? What’s the current norm for packet sizes and internet traffic protocols? Drawing on Kentik Detect’s ability to see and analyze network traffic, this post shares some intriguing factoids, and it sheds light on some of the insights about your own network traffic that await you as a Kentik customer.
Advances in open source software packages for big data have made Do-It-Yourself (DIY) approaches to Network Flow Analyzers attractive. However, careful analysis of all the pros and cons needs to be completed before jumping in. In this post, we look at the hidden pitfalls and costs of the DIY approach.
Cisco will acquire cloud-cost comparison tool Cmpute.io. Juniper Networks may also be moving on cloud-focused M&A, specifically in the multi-cloud cybersecurity sector. Beyond cloud, the hype of AI continues. Elon Musk’s Tesla team is working on an AI project that could be “the best in the world,” he said this week. More news after the jump…
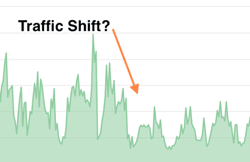
Media reports tell us that Cyber Monday marked a single-day record for revenue from online shopping. We can assume that those sales correlated with a general spike in network utilization, but from a management and planning perspective we might want to go deeper, exploring the when and where of traffic patterns to specific sites. In this post we use Kentik Detect to see what can be learned from a deeper dive into holiday traffic.