Kentik Blog
























Cisco Chairman John Chambers announced this week that he will not seek re-election. The networking giant also announced a partnership with Viacom. Meanwhile, Cisco researchers found that the CCleaner malware was targeting at least 18 tech companies. More after the jump…
As the east coast prepares for Hurricane Irma, those with data centers in the storm’s path are also making efforts to avoid interruptions. DDoS attackers took a gamble this week, making a hit on popular online poker site America’s Cardroom. And a debate has up on how CenturyLink’s plans to acquire Level 3 Communications could affect broadband in rural areas. More after the jump…
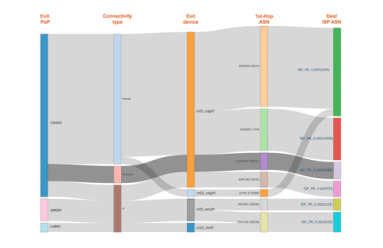
In our latest post on Interface Classification, we look beyond what it is and how it works to why it’s useful, illustrated with a few use cases that demonstrate its practical value. By segmenting traffic based on interface characteristics (Connectivity Type and Network Boundary), you’ll be able to easily see and export valuable intelligence related to the cost and ROI of carrying a given customer’s traffic.
Apple announced two new data centers in Iowa. Cisco made another acquisition. VMware reported a strong quarter. DDoS attacks spiked. Google sped up TCP/IP. And Wired put together an interactive map to show where internet trolls live. More headlines after the jump…
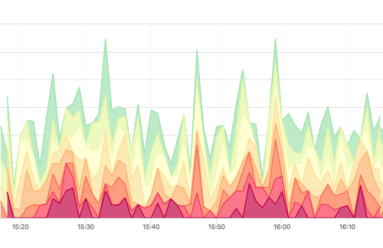
With much of the country looking skyward during the solar eclipse, you might wonder how much of an effect there was on network traffic. Was there a drastic drop as millions of watchers were briefly uncoupled from their screens? Or was that offset by a massive jump in live streaming and photo uploads? In this post we report on what we found using forensic analytics in Kentik Detect to slice traffic based on how and where usage patterns changed during the event.
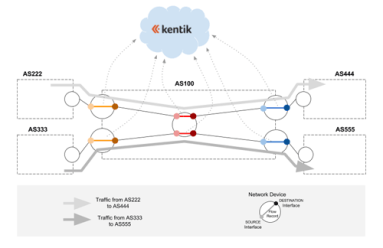
Domain Name Server (DNS) is often overlooked, but it’s one of the most critical pieces of Internet infrastructure. As driven home by last October’s crippling DDoS attack against Dyn, the web can’t function unless DNS resolves hostnames to their underlying IP addresses. In this post we look at how combining Kentik’s software host agent with Dashboards in Kentik gives you the tools you need to ensure DNS availability and performance.
Web companies put the brakes on hate group Daily Stormer using their services. The EFF responded with a warning. A new DDoS attack known as “pulse wave” was uncovered. DDoS attacks hit a bunch of Blizzard Entertainment games. And the biggest shipping company said a single attack cost it nearly $300 million.
Kentik addresses the day-to-day challenges of network operations, but our unique big network data platform also generates valuable business insights. A great example of this duality is our new Interface Classification feature, which streamlines an otherwise-tedious technical task while also giving sales teams a real competitive advantage. In this post we look at what it can do, how we’ve implemented it, and how to get started.
Docker’s $1.3 billion valuation. Disney $1.6 billion acquisition for streaming services. And international internet speed tests and U.S. home internet data caps. Those stories and more after the jump.
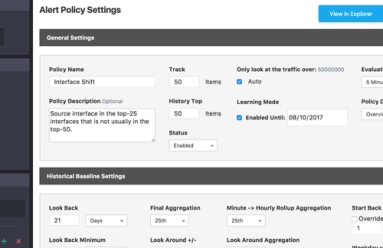
Major cyber-security incidents keep on coming, the latest being the theft from HBO of 1.5 terabytes of private data. We often frame Kentik Detect’s advanced anomaly detection and alerting system in terms of defense against DDoS attacks, but large-scale transfer of data from private servers to unfamiliar destinations also creates anomalous traffic. In this post we look at several ways to configure our alerting system to see breaches like the attack on HBO.