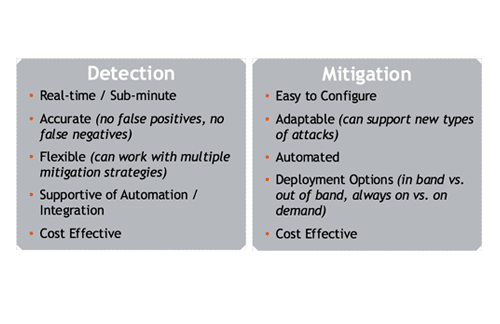
Summary
Attackers are using memcached to launch DDoS attacks. Multiple Kentik customers have reported experiencing the attack activity. It started over the weekend, with several external sources and mailing lists reporting increased spikes on Tuesday. In this blog post, we look at what our platform reveals about these attacks.
Using Kentik Detect to analyze and respond to memcached attacks
Attackers are using an open source software package called memcached to launch DDoS attacks, and multiple Kentik Detect® customers have reported experiencing the attack activity. It started over the weekend, with several external sources and mailing lists reporting increased spikes on Tuesday.
Memcached? What is that?
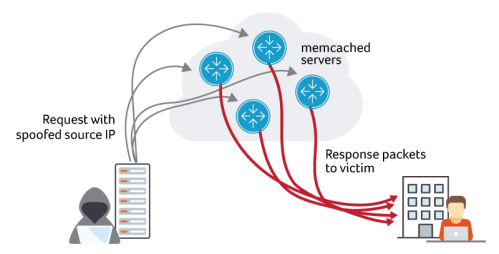
For background, memcached is an open source software package that provides an in-memory caching layer often deployed as a component of web application stacks to reduce load on traditional databases for frequently-accessed objects. In a typical deployment, memcached would be accessed only by internal application components, however, it appears that thousands of memcached instances are exposed to the Internet at large. The memcached service exhibits several qualities that make it a perfect target for DDoS reflection and amplification abuse: by default it listens on UDP and binds to every interface, and can generate large responses in reply to small requests. In this way, it’s very much like DNS and NTP services that have been abused this way in the past. Attackers send a small request packet to well-connected hosts with memcached running. The request packets have a spoofed source IP of the intended victim. The memcached server then generates a flood of reply traffic toward the spoofed victim IP.
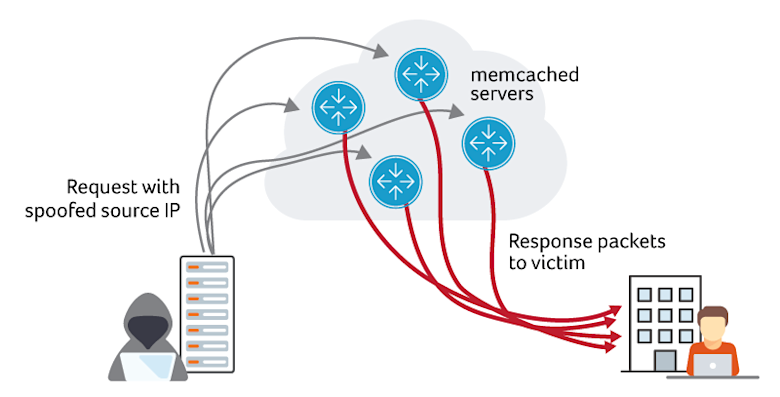
The main difference between memcached attacks and DNS and NTP attacks of the past is the Bandwidth Amplification Factor (BAF). The US-CERT is reporting BAFs of 10,000 to 51,000 for memcached versus 28-54 for DNS and 556 for NTP. That makes for massive attack potential.
What Kentik Sees
We pulled some interesting stats based on anonymized traffic aggregates from Kentik Detect customers who have opted into our data sharing program. First, a timeline of total memcached traffic volume over the last week:
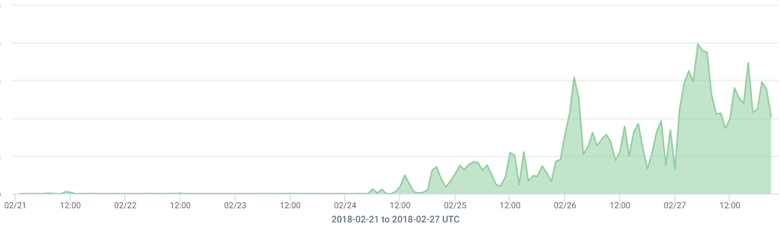
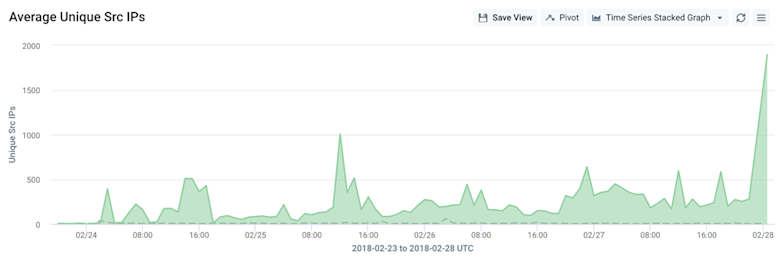
There are small blips extending back into the prior week, but attack activity really started in earnest around noon UTC on Feb 24th. We believe that’s attributed to the new attack vector becoming commoditized and available within the for-pay DDoS attack black market. The graph scale above is intentionally omitted, but multiple Kentik customers saw 100+ Gbps peaks of memcached traffic. We also looked at unique sources, starting from Feb 24th. We can see that a relatively small number of sources are generating a lot of traffic, indicating that the attackers are likely leveraging well-connected servers with 10G connectivity.
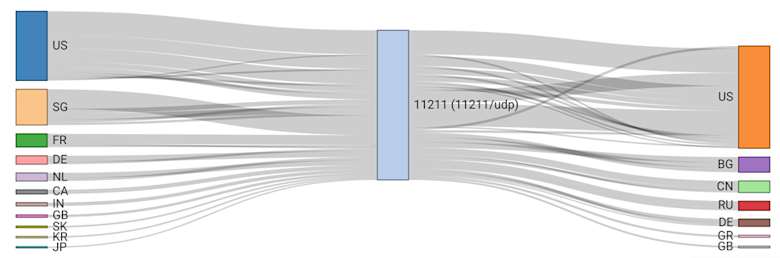
And lastly, a Sankey flow diagram indicating relative memcached traffic volume for source and destination countries over the last few days:
Two Key Takeaways
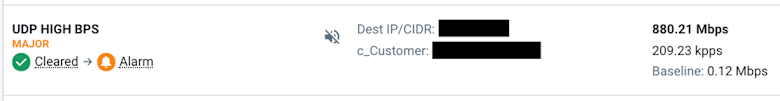
- Most Kentik customers already had policies configured and enabled to detect these attacks. The “VERY HIGH PPS” and “UDP HIGH BPS” policies in the Alert Policy Library both work well for detecting these attacks out of the box. The example below shows an alarm from a memcached reflection attack Tuesday:
- As of ~4 pm PST Tuesday, Kentik updated our global “UDP BADPORTS” saved filter to include UDP/11211. Any customer alert policies, saved views, or dashboards that reference this filter will now automatically include memcached traffic. That includes the “UDP BADPORTS ATTACK” policy in the alert library, which can also be used for more targeted detection of these attacks. This will provide our customers with a faster, easier way to see the traffic associated with this type of attack.
Summary
These types of UDP amplification attacks are increasing in frequency and volume. They can be very costly to a business in terms of lost revenue and high Service Level Agreement (SLA) payouts. To see whether the memcached attacks are affecting your network, schedule a demo or sign up today for a free trial.
To learn more about how Kentik can help improve network security and protect against DDoS attacks, read our Kentik DDoS Detection and Defense solution brief.