Understanding MTTR Networking: How to Improve Incident Response Time

Summary
As organizations continue to shift their operations to cloud networks, maintaining the performance and security of these systems becomes increasingly important. Read on to learn about incident management and the tools and strategies organizations can use to reduce MTTR and incident response times in their networks.
As organizations continue to shift their operations to cloud networks, maintaining the performance and security of these systems becomes increasingly important. Responding to incidents promptly and efficiently is vital to minimizing damage, reducing downtime, and safeguarding critical data and infrastructure. One metric that plays a crucial role in incident response is mean time to repair (MTTR), which measures the average time it takes to fix a network issue once it has been detected.
Focusing on reducing MTTR can help organizations improve their incident response capabilities. This involves streamlining processes, having the right tools to identify real-time issues, determining bottlenecks, and implementing automation where possible. By reducing the time it takes to identify and resolve incidents, organizations can ensure that their systems are up and running again as quickly as possible, minimizing the impact on user experience and system performance.
This article will cover incident management and the tools and strategies organizations can use to reduce MTTR and incident response times in their networks. To close, we will see how network observability helps NetOps teams adopt a proactive approach to incident response that reduces MTTR and incident-related costs while enhancing their networks’ security and performance.
Stages of incident management
Incident management refers to the processes, procedures, and tools used to identify and resolve performance issues and disruptions in a computer network.
The “lifecycle” of incident management can be thought of in five steps:
- Prepare
- Detect
- Isolate
- Resolve
- Optimize
Let’s take a closer look at each of these stages of incident management.
Prepare
This stage involves developing and implementing incident response plans, policies, and tools and training employees to respond to incidents.
Detect
This stage involves identifying and detecting signs of performance issues or disruptions in a networking environment. This can be done through the use of monitoring and observability tools that provide visibility into the health and performance of network infrastructure and services.
Isolate
Once an issue is detected, the next step is to isolate the affected systems or resources if an immediate fix isn’t apparent to prevent further performance degradation or disruption. This could involve diverting traffic to alternate resources or scaling resources up or down based on demand.
Resolve
This stage involves identifying the root cause of the performance issue and developing and executing a plan to resolve it. This could include updating resource utilization, upgrading hardware or software, or reconfiguring the environment to better align with application requirements.
Optimize
Once the incident has been resolved, it’s essential to maintain ongoing monitoring and analysis to ensure that the network remains performant and resilient. Post-mortems provide excellent data points for optimizations, which could involve updating monitoring and alerting systems, incident management preparations, new security or traffic management policies, or other measures such as re-visiting infrastructure design or hardware choices.
Metrics for incident management
Assessing incident response in enterprise networks can be accomplished with a wide variety of metrics. Here are some of the most foundational incident management metrics:
-
Mean time to detect (MTTD): Closely aligned with Mean time to innocence (MTTI), this metric measures the time to detect an incident from the moment it occurs. It includes the time it takes to identify the incident, investigate it, and confirm its existence.
-
Mean time to repair (MTTR): This metric measures the time to resolve an incident and restore services to normal. It includes the time it takes to identify the problem, diagnose it, plan and execute a solution, and verify that it has worked.
-
First call resolution (FCR): This metric measures the percentage of incidents that are resolved in a single interaction between the customer and the support team. A high FCR rate is indicative of efficient and effective incident management.
-
Incident response time: This metric measures the time the support team takes to respond to an incident once it has been reported. A fast response time can help prevent an incident from escalating and minimize its impact.
-
Incident severity: This metric categorizes incidents based on their severity level, which helps prioritize incident management efforts. The impact on services may determine a severity level, the number of users affected, the urgency of the situation, or a more service-specific metric.
-
Incident backlog: This metric measures the number of unresolved incidents at any given time. A large backlog can indicate that the support team is overwhelmed and may require additional resources to manage incidents effectively.
By tracking and analyzing these metrics, network operators and engineers can better understand their incident management performance and identify areas for improvement.
What is MTTR?
MTTR most often stands for mean time to repair. It refers to the average amount of time it takes to resolve an incident, from the moment it is detected to the point where the system or service is fully operational again.
MTTR is an important metric because it helps teams measure their efficiency and effectiveness in responding to incidents. A low MTTR indicates that the system or team or both can quickly detect and resolve incidents, minimizing downtime and reducing the impact on users. On the other hand, a high MTTR may indicate inefficiencies in the incident response process, leading to longer downtime and increased costs.
By tracking MTTR over time, teams can identify trends and improve their incident response process to reduce downtime and improve service reliability. It may also be an appropriate metric to share with customers to set expectations.
Other MTTRs
Besides mean time to repair, MTTR can refer to one of several related metrics for network operators and incident response teams.
- Mean time to respond: This MTTR measures the average time it takes for an incident response team to acknowledge and respond to an incident. It includes the time it takes to detect and identify the issue and the time it takes to initiate a response. This can be considered a sub-metric for mean time to repair.
- Mean time to recovery: This metric picks up where mean time to respond leaves off and takes into account the time it takes to restore systems and services to full functionality and the time it takes to verify that the systems and services are working as expected. This can also be considered a sub-metric for mean time to repair.
- Mean time to restore: Synonymous with mean time to repair.
- Mean time to resolution: Synonymous with mean time to repair.
Factors that affect MTTR in cloud networks
Here are five factors that can impact MTTR for network operators:
- Complexity of the network: The complexity of the network can lead to longer resolution times, as it becomes more challenging to identify and troubleshoot issues. Are public and private resources being utilized? Are containers in the mix?
- Lack of visibility: Lack of visibility into the network infrastructure and its components can make it challenging to pinpoint the root cause of an incident. This problem can be exacerbated by visibility into traffic flows within public clouds.
- Inefficient incident management processes: Inefficient incident management processes, such as a lack of documentation or communication, can delay resolution times and lead to more extended downtimes.
- Human error: Human error can also contribute to longer MTTR, mainly if mistakes are made during incident response or if staff lack the necessary skills and experience.
- Lack of data analytics: Poor analytics can impede incident resolution as teams may struggle to identify patterns or trends that could aid in troubleshooting and incident response, especially prevention.
Strategies for improving MTTR
Despite the complexity of modern networks, NetOps have more tools and strategies than ever to help reduce their mean time to repair.
Let’s examine some of them here.
Processes and tools
Establishing an effective incident management process is essential for reducing MTTR in cloud networking. This process involves several steps, including incident identification, triage, investigation, resolution, and post-incident review. Implementing a centralized incident tracking system that integrates with IT service management (ITSM) tools can help streamline incident resolution and reduce response times.
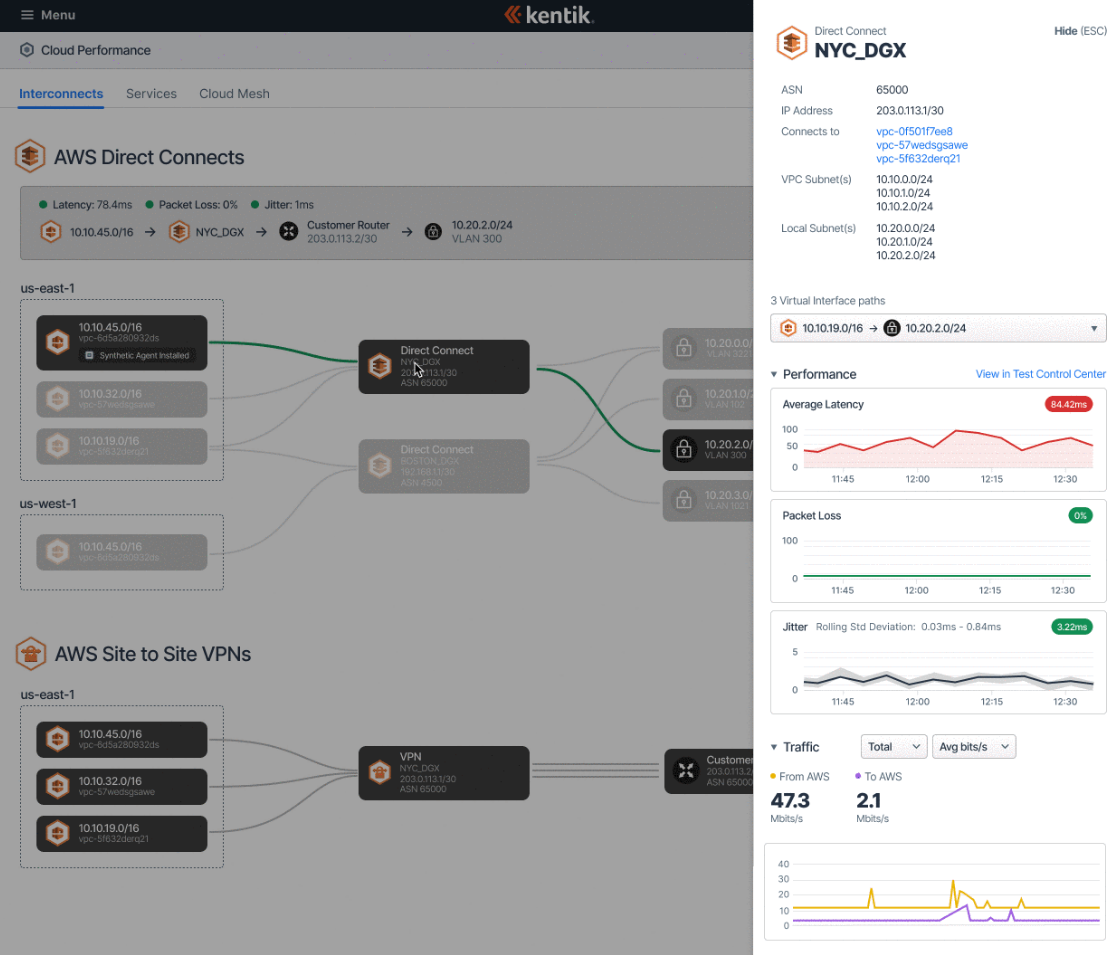
Network observability involves tools and practices that enable real-time monitoring, analysis, and troubleshooting of network performance and health. Using highly contextual instrumentation and powerful data analytics helps IT teams proactively identify and resolve issues before they become significant incidents, understand system usage patterns, and test network-wide optimizations. Comprehensive network observability should include a combination of monitoring your actual traffic and test, or synthetic traffic, to give a complete picture of all threats and impacts to QoS.
Automation tools can reduce the time spent on manual tasks and improve overall efficiency. For example, implementing a chatbot that automatically creates incidents, categorizes them, and assigns them to the appropriate support team can significantly reduce MTTR. Incident management tools like PagerDuty and Opsgenie can help teams quickly identify and prioritize issues and send alerts to the right stakeholders for prompt resolution.
Support team training
Providing training for support teams is critical for improving MTTR. Teams must have the necessary skills, knowledge, and experience to troubleshoot and resolve complex issues effectively. Continuous training and development on new technologies like container orchestration platforms, cloud-native security solutions, and the latest features and updates to cloud networking platforms like AWS, Azure, and GCP.
Incident response drills
Regular incident response drills can help identify gaps in incident response plans and improve overall preparedness for handling complex issues. These drills can help teams practice responding to simulated incidents and improve their ability to resolve them quickly.
For instance, teams can simulate a DDoS attack on the network and practice isolating the affected resources and mitigating the attack. Regular drills can also help identify gaps in documentation, procedures, and tools, which can be addressed to improve response times during actual incidents.
How Kentik can help
Kentik’s network observability platform can help IT organizations reduce mean time to repair (MTTR) by providing unparalleled, real-time visibility into network infrastructure. By collecting and analyzing network telemetry from across the entire network, Kentik can identify performance issues and anomalies before the system experiences significant performance or security impacts. This proactive approach to network observability helps IT teams quickly identify and address issues, reducing the time it takes to resolve them.
Kentik monitors your actual traffic alongside test traffic – Kentik Synthetics. Synthetic tests can be a significant asset in reducing MTTR, especially in heading-off issues before they are customer-impacting. Synthetics also help you identify whether the problem is with your network infrastructure or a broader issue impacting internet apps or public cloud infrastructure.
Kentik’s platform provides detailed network performance metrics, allowing IT teams to quickly understand the root cause of network issues. With customizable alerts and dashboards, Kentik helps IT teams respond to network issues as they arise. Powerful workflows and third-party integrations help ensure prompt, automated, and highly actionable responses.
To see how Kentik can help reduce MTTR in your incident response, start your free 30-day trial.