Cloud Security Policy Management: Definitions, Benefits, and Challenges
Cloud Security Policy Management is critical for ensuring the protection of cloud environments by establishing and enforcing security measures. As organizations increasingly adopt cloud solutions, maintaining a secure framework can be a complex challenge due to the distributed nature of cloud resources. Cloud security policies aim to mitigate risks—including unauthorized access, data breaches, and compliance failures—by implementing frameworks that manage access control, encryption, and incident response. A variety of frameworks such as CSA, CIS, and OWASP offer guidelines that can help organizations align their cloud operations with best practices, ensure compliance, and provide robust security even across multicloud environments.
Security policy management is no longer limited to static, on-prem environments. In the cloud, security policies must account for dynamic scaling, real-time traffic, and a constant need for visibility into security posture. Effective management requires a mix of automation, real-time observability, and deep integration with regulatory frameworks.
What is Cloud Security Policy Management?
Cloud Security Policy Management is a structured approach to defining, implementing, and managing security policies in cloud environments. It involves setting rules and guidelines that govern the use, access, and protection of data and services that reside in the cloud. These policies cover areas such as identity management, data encryption, access controls, and adherence to compliance standards like the Cloud Security Alliance’s Cloud Controls Matrix (CSA CCM) or CIS Benchmarks. The goal is to provide a consistent security framework that can adapt to the elastic and multi-tenant nature of cloud environments.
Kentik in brief: The Kentik Network Intelligence Platform supports cloud security policy management by showing how security policies behave in practice, using enriched flow logs and cloud metadata. See allowed and denied traffic, audit security groups and ACLs against real application dependencies, and alert on unusual access patterns so teams can enforce least-privilege without breaking connectivity.
Learn how AI-powered insights help you predict issues, optimize performance, reduce costs, and enhance security.


Central Elements of a Cloud Network Security Policy
At its core, cloud security policy management ensures that all cloud activities are controlled, tracked, and compliant with both internal and external standards. Key elements include:
- Identity and Access Management (IAM): Enforcing role-based access to sensitive data.
- Data Encryption Policies: Ensuring that data at rest and in transit is encrypted using strong encryption algorithms.
- Incident Response Plans: Preparing automated responses to security breaches or policy violations.
Without a structured policy management framework, organizations face increased risks of data leaks, unauthorized access, and failed compliance audits. Adopting comprehensive cloud security policies allows enterprises to confidently manage cloud resources while remaining secure and compliant.
Differences Between Managing On-Premises and Cloud Security Policy
The shift from traditional on-premises security methods to cloud security policy management represents a fundamental change in approach and complexity. Historically, on-premises security relied heavily on physical controls, perimeter defenses like firewalls, and fixed network infrastructure. Security policies were often static, designed to secure a finite number of endpoints and users within the enterprise’s boundaries. On-premise methods focused on locking down devices, data centers, and tightly controlled networks using tools like intrusion detection systems (IDS), virtual private networks (VPNs), and identity and access management (IAM) frameworks primarily designed for internal users.
While cloud environments bring flexibility, they also introduce new challenges. Data is no longer housed in a single, protected environment. It’s now distributed across multiple cloud service providers (CSPs), often spanning different regions and jurisdictions. Additionally, workloads can move dynamically between clouds and on-premises environments (in hybrid or multicloud setups), requiring security policies that can handle this fluidity.
One key distinction is that traditional security policies often emphasized defense-in-depth strategies within a defined perimeter, focusing on securing internal endpoints and servers. In contrast, cloud security policies are perimeter-less. The attack surface is broader, extending to cloud infrastructure, APIs, and external services, necessitating more advanced, continuous policy enforcement mechanisms that traditional systems were not designed to manage.
Another difference lies in visibility and control. On-premise security teams had full control over their environments, making visibility straightforward. In contrast, cloud infrastructures introduce shared responsibility models, where CSPs manage the underlying hardware, and customers manage the data and applications. Security teams now need comprehensive policies to ensure compliance and security across these multiple layers of ownership.
Traditional security frameworks were often reactive, relying on manual processes like audits, firewall adjustments, and patch management. Cloud security, however, requires proactive automation—policies must adjust in real-time as new services are spun up or down. Policies around network segmentation, encryption, and access controls need to be automatically enforced across diverse cloud resources. This shift in mindset—from static, reactive approaches to dynamic, automated, and real-time policy enforcement—has redefined how security is managed.
Though these traditional policies laid the groundwork, cloud security introduces the need for continuous visibility and adaptability, hinting at the critical role that real-time observability plays in maintaining an agile, secure cloud environment.
What are the Benefits of Cloud Security Policy Management?
Cloud Security Policy Management provides a multitude of benefits:
- Enhanced Scalability: Cloud policies can automatically scale with your infrastructure, ensuring protection for both small instances and large-scale deployments.
- Automated Compliance: Regular audits and compliance checks are embedded in the cloud environment, reducing the effort needed to meet standards like ISO 27001 or SOC 2.
- Centralized Management: Policies are managed from a central platform, enabling global visibility and control across different cloud environments and regions.
- Reduced Risk: By implementing consistent security policies, organizations can minimize the risk of misconfigurations, breaches, and non-compliance across their cloud resources.
- Cost Efficiency: Automated policy management reduces the need for manual oversight, cutting down on operational costs and enabling a faster response to threats or violations.
With the proper cloud security policy framework in place, businesses can maintain agility and innovation without compromising their security posture. Policy automation and integration with observability tools, such as Kentik, enhance real-time visibility, helping organizations stay ahead of potential threats.
The Role of Observability in Cloud Network Security Policy
Observability is a cornerstone of modern Cloud Security Policy Management, providing the necessary visibility to ensure that policies are both enforced and effective. In cloud infrastructure’s complex, dynamic environments, observability tools like Kentik serve a crucial role in ensuring security by offering insights into traffic patterns, potential threats, and policy violations in real-time.
Traditionally, network monitoring and logging were sufficient to oversee on-premises environments. However, in the cloud, the infrastructure is far more distributed and interconnected. Cloud observability extends beyond basic logging and monitoring to encompass metrics, traces, and logs in a more integrated, holistic manner. In this context, observability helps in three critical areas: ensuring policy compliance, detecting and responding to threats, and maintaining operational performance.
Ensuring Policy Compliance
Observability tools allow organizations to track the adherence of cloud resources to established security policies. Metrics like user access patterns, API activity, and data transfer volumes can be continuously monitored to ensure compliance. Policies that dictate encryption standards, IAM roles, or data storage practices are actively enforced by tracking how resources are used. Observability provides real-time reports on whether cloud resources conform to compliance standards such as the Cloud Controls Matrix (CCM) from the CSA or the CIS Benchmarks. If a resource deviates from established policies, alerts are generated, prompting immediate remediation.
Threat Detection and Response
One of the core features of observability in cloud security is its ability to detect anomalous behavior. Since cloud environments are highly dynamic, traditional security tools often fail to catch subtle changes that indicate a threat, such as lateral movement or unauthorized access attempts. Observability tools enable continuous data collection from various cloud layers (infrastructure, application, user activity) to detect these anomalies in real-time. For example, an unusual spike in outbound traffic from a particular instance could indicate a data exfiltration attempt, prompting security teams to act swiftly. Through machine learning models, observability tools like Kentik can learn normal operational patterns and detect deviations that might signal a security incident, such as unauthorized data access or misuse of administrative privileges.
Operational Performance and Policy Impact
Observability is not just about detecting threats. It also ensures that security policies are not negatively impacting system performance. For example, overzealous encryption standards or restrictive access control mechanisms might degrade application performance, especially in highly scalable environments. With observability tools, organizations can correlate security policy enforcement with operational performance metrics. This insight allows security and DevOps teams to fine-tune policies, ensuring optimal performance without sacrificing security.
Automated Policy Enforcement and Auditing
Observability tools enable the automation many of the manual tasks associated with policy enforcement. Instead of relying on periodic audits, organizations can perform continuous auditing of their cloud environments. Any deviation from security policies can trigger automatic remediation actions, such as adjusting IAM permissions or reconfiguring security groups. This level of automation reduces human error, ensures consistency, and speeds up incident response times.
Observability transforms cloud security policy management from a reactive process into a proactive and dynamic system. By ensuring policy compliance, detecting and mitigating threats, and optimizing operational performance, observability tools like Kentik empower organizations to secure their cloud environments effectively in real-time.
Challenges in Implementing Cloud Security Policy Management
Implementing cloud security policy management is not without its challenges:
- Complexity in Multi-Cloud Environments: Organizations using multiple cloud providers face difficulties ensuring consistent policy enforcement across platforms with different configurations.
- Evolving Threat Landscape: As cloud technologies evolve, so do the threats. Policies need constant updates to address new vulnerabilities, making continuous policy evaluation a necessity.
- Compliance: Adhering to global compliance standards such as GDPR, HIPAA, and CCPA adds layers of complexity, especially when dealing with data that spans multiple geographic regions.
- Skills Shortage: Many organizations struggle to find skilled personnel capable of managing complex cloud security policies effectively.
Addressing these challenges requires a combination of automation, regular audits, and collaboration with cloud service providers to ensure security measures are integrated into the cloud infrastructure.
How Kentik Can Help with Cloud Security Policy Management
With Kentik’s network intelligence platform, you can monitor and enforce cloud security policies in real time, ensuring compliance with security frameworks like CSA and CIS. Kentik’s cloud infrastructure and traffic observability features enable continuous monitoring, automatically identifying policy violations, and providing insights into traffic patterns, access controls, and potential security threats.
Kentik Cloud collects, analyzes, and contextualizes traffic flow and performance data from all major public clouds –- from Microsoft Azure, Google Cloud, AWS and Oracle Cloud Infrastructure –- along with data from on-premises networks. Kentik enriches all this network telemetry with deep application, business, and security context to provide observability across all hybrid and multicloud environments.
Just a few of Kentik’s use cases in cloud network security are described below.
Auditing Cloud Security Groups and Firewall Policies
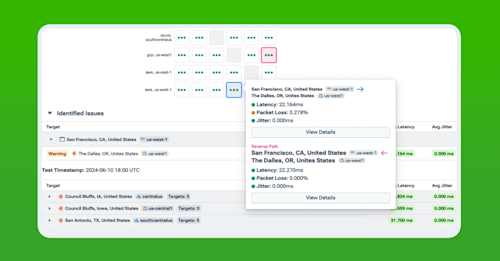
Kentik Cloud can be used to audit cloud security groups and firewall policies. NetOps teams use Kentik to review security policy at large scale so they can identify any areas where policies could be tightened. The goal is to enforce the “least privilege” principle.
For example, they can do a traffic study by running a reports to show all the traffic that has traversed a particular security group in the last 30, 60, 90 days and determine whether all of the traffic was legitimate (i.e., required by the app or inbound requests from users), or if there is any extraneous traffic. Based on the data, they can update the policy to block any traffic that was not needed (least privilege) or possibly malicious.
Kentik also plays a role in validating the impact of new policies on application performance. For example, Kentik correlates flow logs and cloud firewall or security group decisions (accept/reject) with application traffic so you can see when firewall policies are blocking or degrading application flows and adjust rules to restore performance.
Analyzing and Understanding Denied Traffic
On the flipside, Kentik can also be used on an ad-hoc basis to quickly investigate issues where security group or firewall policies are blocking legitimate traffic. These requests often come from DevOps or customer success teams. For example, “we can’t access this resource,” or “connectivity is being refused and this should be working.”
With Kentik, NetOps (or even DevOps or CS themselves) can see the traffic in question—and which security group, account, VPC, or other cloud component is involved—so they can go fix it in the cloud console.
In cloud environments even a tiny misconfiguration in security groups or routing tables can lead to significant traffic blockages. In this short demo, Phil Gervasi shows how Kentik can diagnose these issues and use enriched flow data and contextual analysis to find the root cause of traffic blockages:
Cloud Network Anomaly Detection
Beyond traffic studies, Kentik’s automated anomaly detection and alerting can highlight areas where security policy needs to be tightened.
By integrating Kentik’s observability tools, your organization can enhance cloud network automation, reduce risks, and ensure your cloud environments are protected at scale.
Start a free trial or request a personalized demo today to learn how Kentik’s observability tools can help your organization improve cloud network automation, reduce risks, and ensure your cloud environments are protected at scale.
Related Cloud Monitoring Articles
- Network Forensics and the Role of Flow Data in Network Security
- Enterprise Cloud Monitoring: 5 Best Practices, Challenges, and Solutions
- How to Use Kentik to Perform a Forensic Analysis After a Security Breach
- Cloud-Native Network Functions (CNF)
FAQs about Cloud Security Policy
How can I monitor firewall policy impact on application performance?
Kentik ingests cloud flow logs (including accept/reject flags) and correlates them with security groups and firewall policies. That lets you see exactly which firewall or NSG rules are blocking or shaping application traffic, and whether those policies are increasing latency or causing failures. By combining flow, application-level metrics, and policy metadata, Kentik shows how firewall decisions affect real application performance rather than just listing rules in a vacuum.