How to Prevent DDoS Attacks
In a traditional DDoS prevention model, out-of-band appliances detect DDoS attacks based on NetFlow, sFlow, IPFIX, and BGP data. The appliance then signals the network, via network control plane or element management protocols, to either drop traffic at the network edge or redirect traffic to a cloud DDoS mitigation device.
Over time, only a fraction of total traffic will need to be mitigated. So dedicating one or more appliances to detection and selectively pushing traffic to mitigation maximizes the cost-efficiency of the total solution. The approach makes sense on paper, but the drawback inherent in all such appliance-based DDoS defense solutions is that they are fraught with poor detection accuracy.
Network Visibility and DDoS
Fortunately, cloud-scale big data systems make it possible to implement a far more intelligent solution to the problem of DDoS attacks by:
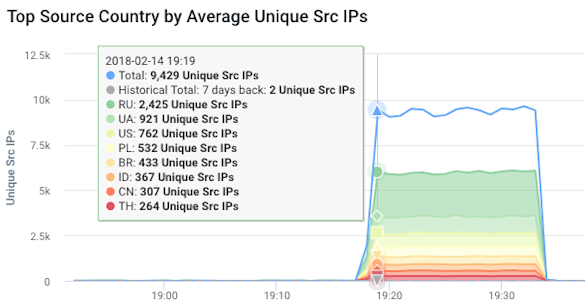
- Monitoring the network-wide traffic level of millions of individual IP addresses.
- Monitoring against multiple data dimensions. While in many cases it is sufficient to look for violations of simple traffic thresholds, for the vast majority of attacks it’s becoming necessary to go beyond a single dimension and recognize the relationships between multiple indicators of denial-of-service attacks.
- Automatically identifying and tracking “interesting” IP addresses by auto-learning and continuously updating a list of top-N traffic receivers. Then perform baselining and measurement to detect anomalies on any current member of that list.
Anomaly Detection
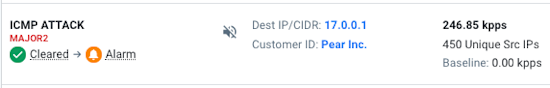
This scalable, adaptive big data approach to monitoring and anomaly detection has been field-proven as far more accurate than legacy approaches in real-world deployments where customers have used both kinds of DDoS defense solutions. Kentik’s big data approach delivers not only more accurate anomaly detection, but also makes it possible to store detailed raw flow records and related data to detect elusive low volume, multi-vector attacks. Volumetric attacks periodically cover up more intrusive, exploratory attacks.
DDoS Mitigation for Cloud
Cloud DDoS defense is the application of cloud computing scale to the process of detecting and mitigating DDoS attacks. By utilizing cloud-scale compute and storage resources, cloud DDoS makes it possible to collect and examine network flow data in highly granular fashion, supporting superior baselining intelligence. The combination of scale, granularity, and baselining ensures greater detection accuracy, saving network operators time and money.
Cloud-scale big data systems also make it possible to implement a far more intelligent approach to the problem making a new hybrid model possible, where DDoS detection is performed by Kentik’s best-of-breed, cloud service that automates the triggering of RTBH, and then mitigation can be handled by on-premises mitigation applicances or cloud-based DDoS mitigation solutions—such as Cloudflare Magic Transit.
Respond with Intelligence
As infrastructure, traffic, and threats evolve, you can use Kentik’s flexible analytics capabilities to provide the deeper intelligence that enables an agile DDoS defense. All alerts generated by Kentik are linked to dashboards, making it possible to access powerful visualizations and filtering to help you dig into the origin and nature of attacks, returning answers to multidimensional queries in seconds, across billions of unsummarized flow records correlated with BGP and GeoIP. By combining automated mitigation with exceptionally accurate detection, Kentik provides a modern approach to implementing cost-effective, fast-to-deploy, real-time protection against DDoS attacks.