Network Anomaly Detection: A Comprehensive Guide
Network anomaly detection is a technique used to monitor, analyze, and identify unusual patterns or activities within a computer network. These anomalies are deviations from normal behavior which could indicate potential security threats, such as cyberattacks or unauthorized access. Detecting anomalies early is crucial—by spotting abnormal network behavior in real time, organizations can respond quickly to mitigate risks and protect their network resources. Real-time anomaly detection has become an essential component of network operations (NetOps) and security strategies, helping teams catch issues as they happen rather than after any potential damage is done.
In this article, we explore what network anomaly detection is, why it matters, and how it works. We’ll look at the role of AI and machine learning in modern anomaly detection systems, and how these technologies enable real-time anomaly detection and more accurate alerts. We also discuss specific use cases like DDoS detection and how anomaly detection supports incident response and digital forensics. We also compare Kentik’s capabilities to other network anomaly detection solutions in the market.
What Is Network Anomaly Detection?
Network anomaly detection is the process of identifying irregular or atypical patterns in network traffic that deviate from normal behavior. At its core, network anomaly detection involves continuously collecting network telemetry data—such as flow records, packets, or logs—and comparing it against a baseline of normal network behavior. The baseline is established using historical data and statistical analysis of what “normal” traffic looks like in terms of volume, protocols, IP addresses, user access patterns, etc. When current traffic patterns significantly deviate from that baseline, the system flags a network anomaly.
These anomalies can manifest in various ways. For example, as a sudden surge in traffic to a server, an unusual drop in network activity, unexpected traffic from a foreign IP range, or a host machine making connections it has never made before. Such anomalies are often early indicators of underlying issues or threats. They might signal a cyberattack in progress, a misconfigured device, a network failure, or unauthorized usage. Network anomaly detection acts as a safeguard, alerting NetOps and security teams to “something out of the ordinary” happening in their networks so they can investigate further.
Anomaly detection hinges on establishing what “normal” looks like for your network — and knowing when something deviates. Kentik continuously stores flow and telemetry data, letting you build a baseline of normal traffic patterns. Deviations from that baseline such as unusual destinations, volumes or protocols can then be flagged via queries or alerts as anomalies that need investigation. Additionally, Kentik’s flow-based network visibility lets you find unexpected destinations, protocols, geographies or services in your traffic, making it easier to identify unapproved SaaS use, rogue servers or other shadow IT activity that shows up in network telemetry even if it is not centrally managed.

Kentik in brief: Kentik supports network anomaly detection by baselining normal traffic, performance, and routing behavior from flows, metrics, and internet telemetry, then alerting on meaningful deviations. With fast querying and AI-guided investigations, teams can quickly explain whether an anomaly is growth, misconfiguration, routing change, or a security incident.
Learn how to protect your network before an attack causes damage to your customers or reputation.

Why is Network Anomaly Detection Important?
Catching anomalies quickly can mean the difference between a minor network hiccup and a major security breach. An anomaly could be the first sign of a distributed denial-of-service (DDoS) attack, a malware infection spreading laterally, or data being exfiltrated from an organization’s systems. By identifying these events as they occur, organizations have a chance to contain threats or fix problems before they cause significant damage.
Network anomaly detection is essential for maintaining network security and performance, helping to identify potential threats before they cause harm, and ensuring the smooth operation of network systems.
The Need for Real-Time Anomaly Detection
In modern network operations, speed is everything. Threats like DDoS attacks or fast-moving malware can cripple services within minutes. Traditional network monitoring tools often fall short because they might detect issues after a delay or only once a threshold has been violated for some time. By then, the damage may already be done. This is why real-time anomaly detection is so important: the moment an unusual pattern is observed, an alert should be raised so that teams can respond immediately.
Legacy monitoring solutions often can’t see changes in traffic patterns as they happen. As Kentik has noted, with old-school tools, you might miss sudden shifts or only catch them after the fact. In contrast, modern anomaly detection systems analyze incoming network data continuously and immediately flag deviations.
Real-time detection is particularly critical for mitigating DDoS attacks and other rapid-onset threats. According to Kentik’s DDoS experts, two key criteria for effective DDoS defense are speed of detection and accuracy of detection. Speed of detection means recognizing the anomaly (the attack traffic) instantaneously or within seconds, allowing automated mitigations to kick in or for operators to take action. Any delay in detection—measured in minutes or even seconds—can result in extended downtime or damage. In fact, industry research shows that many organizations still take an hour or more to detect a DDoS attack, which is far too slow. Real-time anomaly detection aims to shrink that detection window to near-zero.
Accuracy of detection is equally critical. The system must reliably distinguish true anomalies (i.e., a real attack or incident) from benign fluctuations. Advanced anomaly detection platforms address this by using intelligent baselining and machine learning (which we’ll cover shortly) to reduce false positives and false negatives.
Real-time anomaly detection gives NetOps and security teams a fighting chance to react to issues at the earliest possible moment. In response to a detected anomaly, they may reroute traffic, block an offending IP, or spin up additional resources to handle a traffic surge. Real-time capabilities are not a luxury, but an essential component of any robust network monitoring and security strategy.
How Does Network Anomaly Detection Work?
Network anomaly detection can be implemented using a variety of techniques and approaches. What these approaches have in common is (1) establishing what “normal” looks like for a given network, and (2) measuring new events against that norm. Some of the primary methods of anomaly detection are described below.
Statistical Methods
Statistical anomaly detection uses mathematical models to define normal network behavior and then identifies any statistical outliers. Administrators might set static thresholds (e.g., an alert if traffic exceeds 500 Mbps) or use dynamic thresholds based on standard deviation from average traffic. Techniques like mean, standard deviation, variance, and clustering can help model what metrics are considered typical. If current measurements fall outside an acceptable range—for example, a traffic spike 5 standard deviations beyond the mean—it’s flagged as an anomaly.
Machine Learning-Based Detection
Machine learning (ML) algorithms can analyze vast amounts of network data to learn patterns and detect anomalies. ML-based systems often establish baselines through training data. There are supervised ML approaches (where the model is trained on labeled examples of “normal” vs “anomalous” traffic) and unsupervised approaches (where the system automatically clusters or learns what is normal without explicit labels).
Unsupervised anomaly detection is common in networks because you often don’t have labels for new types of attacks. Techniques like neural networks, clustering algorithms, and probabilistic models fall in this category. The advantage of machine learning is the ability to consider multiple features at once (e.g., traffic volume, source, destination, protocol, time of day, etc.) to detect complex or subtle anomalies that simple thresholds might miss.
Signature-Based Detection
This approach isn’t anomaly detection in the strictest sense, but many network security systems use it in tandem with anomaly detection. Signature-based detection relies on known patterns (“signatures”) of malicious activity. For example, a known malware’s byte sequence or a known attack traffic pattern. If network traffic matches a known bad signature, an alert is triggered. Signature detection is very effective for known threats (with low false positives for those specific patterns), but it cannot catch novel attacks or deviations that don’t match any known signature. That’s where anomaly detection complements the system by aiming to catch the unknown or unexpected issues.
Behavioral Analysis
Behavioral anomaly detection focuses on the behavior of users and devices on the network over time. It establishes profiles for typical behavior. For example, a user usually logs in from San Francisco and accesses certain servers, or a host typically communicates on certain ports. If a user account suddenly starts querying a database server it never accessed before, or a device begins sending data to an unusual external host, these behavioral deviations are flagged as anomalies. This method is especially useful for catching insider threats or compromised accounts, where malicious actions might otherwise blend in as normal network traffic.
Many modern network anomaly detection solutions incorporate a combination of the above methods to increase effectiveness. A system might use ML to baseline network flows, statistical thresholds for certain metrics, and also check known threat signatures simultaneously. The goal is to improve coverage of detection while minimizing noise.
It’s also common to integrate anomaly detection with other security tools—such as Intrusion Detection Systems (IDS), firewalls, and Security Information and Event Management (SIEM) systems—to form a multi-layered defense. The anomaly detector might flag unusual traffic and send an alert to a SIEM or trigger a firewall rule. In practice, alerts generated by anomaly detection are typically reviewed by security analysts or NetOps engineers to determine if they represent real incidents or false alarms. Over time, tuning the system (or retraining models) is important so that the baseline adapts as the network evolves, ensuring that the detection remains accurate.
Types of Network Anomalies
Network anomalies can emerge in a variety of ways, each representing a different type of risk or performance concern within a network environment. One of the most common is the volume-based anomaly, where the total amount of network traffic spikes or plummets compared to an established baseline. Imagine a sharp surge in inbound connections overwhelming a web server—often an early indicator of a Distributed Denial-of-Service (DDoS) attack—or, conversely, a sudden drop in traffic that might hint at a routing misconfiguration or an outage blocking normal data flows.
Another common type involves protocol or port anomalies, where traffic appears on unexpected protocols or ports. For example, operators might notice that a server that typically relies on standard HTTP or HTTPS suddenly starts sending data over an obscure port, or a spike in ICMP requests that doesn’t match normal operational patterns. Such irregularities might signal the start of unauthorized activity or the misuse of a specific protocol for malicious purposes.
Source and destination anomalies occur when a network host communicates with IP addresses, domains, or geographic regions outside its usual scope. Perhaps a host previously restricted to internal IPs starts interacting with a suspicious foreign IP range. Or maybe there’s an unusual burst of traffic to a previously unseen domain. These deviations are often prime indicators of data exfiltration attempts, exploratory scans, or other malicious activities.
Anomalies might also be associated with user and device habits, rather than with the network itself. Behavioral anomalies include unusual login attempts, unfamiliar network connections, or newly accessed resources that might represent red flags. For example, a user account that suddenly connects from two distant geographic locations within an impossibly short timeframe. Or a device that has never used SSH might begin initiating frequent SSH connections—often a sign of compromised credentials or a rogue application.
Beyond security-specific anomalies, changes in performance can be just as telling. Performance anomalies refer to noticeable deviations in metrics like latency, packet loss, or jitter. These metrics can quickly reveal latent issues that degrade user experience, such as a sudden latency surge on a critical application server or a spike in packet drops on a wide-area network link that normally carries traffic smoothly.
At a more granular level, application-layer anomalies encompass unusual behavior in protocols and services like DNS, HTTP, and VoIP. Perhaps a DNS server suddenly begins answering external queries unrelated to your domain (suggesting it might be operating as an open resolver), or a web service encounters an unexpected burst of HTTP error responses. Such signs can point to misconfigurations, targeted attacks, or unintended exposure of critical services.
Finally, there are temporal anomalies, which are irregularities related to the timing of network events. Such deviations occur when traffic patterns break from their historic or expected schedules. For example, substantial data transfers happening late at night (when usage is typically low), or peaks in activity during weekends and holidays, when network demand is usually minimal.
By categorizing anomalies into these broad classes, NetOps and security teams can zero in on the root cause more quickly and determine the severity of the threat. Volume-based anomalies, for example, often imply DDoS attacks, while behavioral irregularities may point to a compromised account. Considering this sort of taxonomy can also be helpful in creating stronger alerting rules and developing mitigation procedures that align more closely with the nature of the event in question. The ultimate goal, of course, is to ensure quicker and more effective resolution of anomalous issues.
The Role of AI and Machine Learning in Anomaly Detection
Artificial intelligence and machine learning techniques play an important role in modern network anomaly detection. As networks grow in complexity and scale (with cloud infrastructure, IoT devices, remote work, etc.), the volume of data is far beyond what humans can manually analyze. Increasingly, business value comes not just from detecting anomalies, but from helping teams understand and act on them faster. AI and ML algorithms are essential for sifting through billions of data points in real time and pinpointing the “needle in the haystack” – those few events that truly indicate something is wrong.
Adaptive Baselining
One of the key contributions of machine learning is building adaptive baselines. Instead of using fixed thresholds, ML systems learn what normal network behavior is by examining historical data. They can account for patterns like daily peaks, weekly cycles, or seasonal variations. For example, an e-commerce site might see traffic spikes every day at 8 PM. An ML-based anomaly detector will learn this is expected and not flag it. However, if traffic at 8 PM is ten times higher than usual (and no sale or promotion is happening), it will recognize this as abnormal.
This adaptive approach reduces false positives because the system calibrates itself to the environment. Kentik Protect (Kentik’s DDoS protection and anomaly detection solution), for example, performs network-wide scanning with multi-dimensional criteria and adaptive baselining. Using machine learning, it can establish a nuanced understanding of normal versus abnormal network activity across many metrics simultaneously.
Advanced Pattern Recognition
AI/ML models can detect complex patterns that rule-based systems might miss. For example, a sophisticated attack might involve a combination of low-and-slow tactics (a small trickle of malicious packets to avoid detection) and multi-vector approaches. A machine learning model could correlate subtle changes across different telemetry data – maybe slight increases in DNS traffic coupled with unusual DNS query types and an uptick in failed logins – which collectively could indicate a coordinated attack underway. Unsupervised learning algorithms (like clustering or autoencoders) are particularly good at clustering “normal” behavior and spotting outliers that don’t fit any learned cluster.
Reduction of False Alarms and “Alert Fatigue” with AI-assisted Investigation
One challenge in anomaly detection is dealing with noise. Not every anomaly is a problem (some could be valid but rare events). Poorly-tuned systems can overwhelm teams with false alarms.
AI-based systems help close this gap by acting as an investigation accelerator. When an anomaly is detected, users can ask Kentik’s AI Advisor natural language questions—such as “What changed?”, “Is this related to BGP?”, or “Is this consistent with a DDoS pattern?”—to quickly determine severity and relevance. This reduces time spent chasing benign anomalies and allows teams to focus on issues that truly matter. The result is more reliable alerts. Advanced systems even employ ensemble methods (multiple models working together) and feedback mechanisms to continuously improve detection fidelity.
Real-time Analytics at Scale
With the help of AI, anomaly detection systems can ingest and analyze enormous volumes of data in real time. Consider that large enterprises and service providers might be monitoring traffic from thousands of routers, switches, cloud instances, etc., generating millions of flow records per minute. Machine learning algorithms, optimized and distributed, enable scanning of this deluge of data for anomalies without human intervention. This is how some platforms (like Kentik) are able to provide real-time insights by streaming telemetry into an AI-driven analysis pipeline.
AI-assisted Analysis and Remediation
Beyond the real-time detection of anomalous events, artificial intelligence is playing a growing role in network monitoring and observability by assisting engineers in investigating and troubleshooting potential incidents. Features such as Kentik Journeys allow users to perform advanced queries, analyses, and visualizations using natural language questions. This enables even less experienced NetOps professionals to perform advanced investigations and root cause analysis.
By greatly reducing, or even eliminating, the need to know the complex terminology, jargon, and vendor-specific device syntax often involved in networking, solutions like Journeys democratize access to critical network information. AI is helping to simplify complex workflows, speed investigations and remediation, and enhance collaboration between NetOps and other IT teams.
For more examples of how LLM-assisted solutions like Kentik’s greatly simplify the analysis of complex network data, see our blog posts “Democratizing Access to Network Telemetry with Kentik Journeys” and “Using Kentik Journeys for Network Troubleshooting.”
AI and ML approaches improve network anomaly detection by making it smarter and more automated. These technologies allow the detection mechanism to learn and adapt as the network and threat landscape change. However, it’s worth noting that AI is not a silver bullet – it works best in combination with domain knowledge and expert tuning.
Use Cases and Applications of Network Anomaly Detection
Network anomaly detection has broad applications in both network security and network performance management. Some of the main use cases where anomaly detection is particularly valuable are described below.
DDoS Detection, Protection, and Mitigation
One of the classic applications of network anomaly detection is DDoS detection. A Distributed Denial of Service (DDoS) attack involves overwhelming a target with traffic from many sources, aiming to disrupt services. DDoS traffic often starts as an anomaly—a sudden flood of packets, far above normal volume, coming from unusual sources. Detecting a DDoS attack essentially means distinguishing this malicious flood from legitimate traffic as quickly as possible. An anomaly-based system monitors traffic baselines and can instantly alert when, say, inbound traffic to a web server jumps to 10× its typical rate or when a flood of packets with a specific signature (like SYN packets in a SYN flood) is observed.
Modern DDoS detection solutions rely on anomaly detection algorithms that focus on speed and accuracy, as noted earlier. Speedy detection is vital so that mitigation (like traffic scrubbing, rate limiting, or triggering upstream filters) can begin early in the attack lifecycle. Accuracy ensures that you don’t accidentally drop legitimate traffic by misidentifying an anomaly. Kentik’s platform, for example, provides robust DDoS detection capabilities that offer real-time visibility into traffic anomalies and can automatically initiate mitigation procedures to neutralize volumetric attacks.
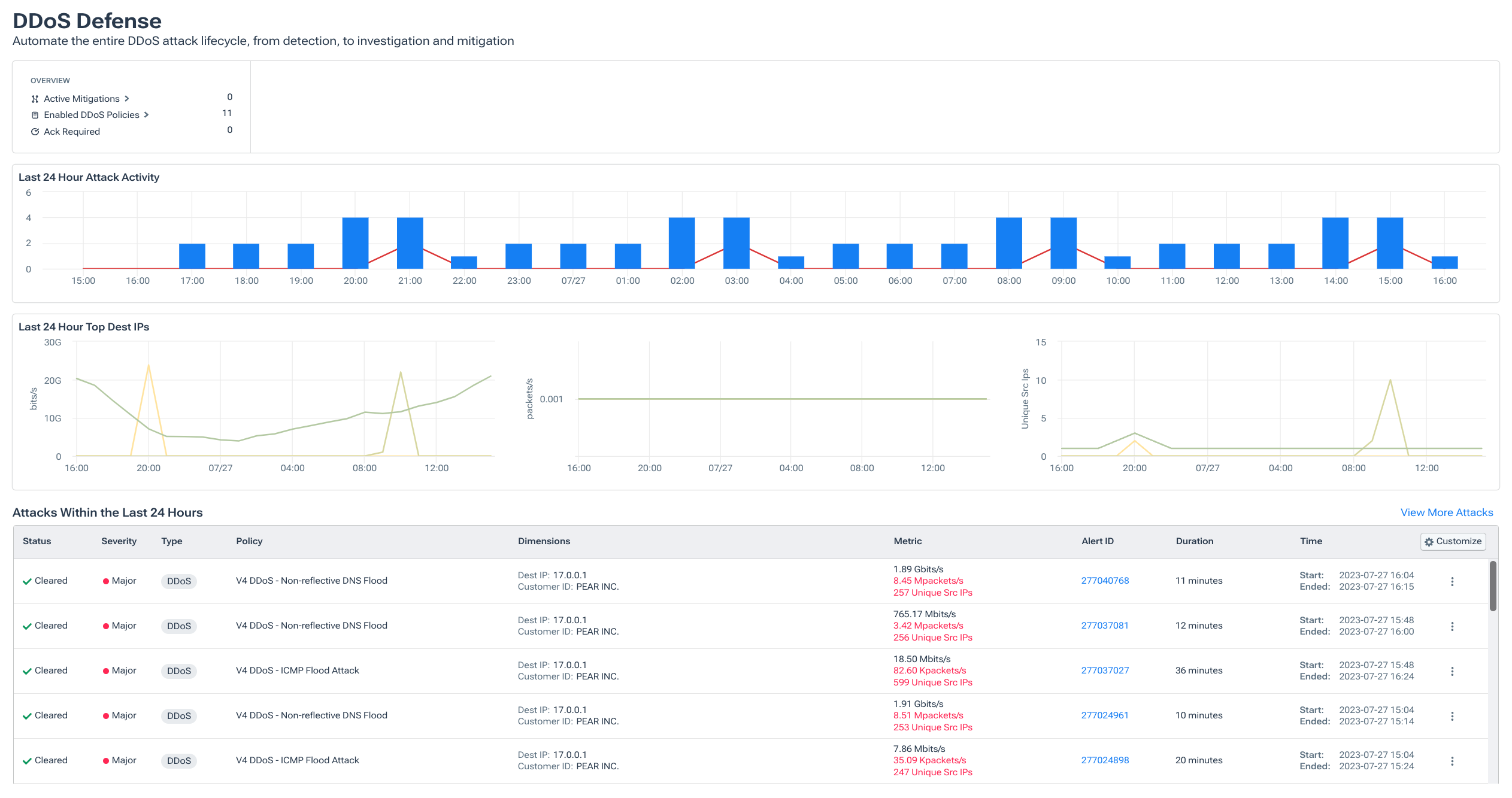
By using a combination of volume thresholds, trend analysis, and ML-baselining, it can quickly flag a developing DDoS event with high confidence. In practice, anomaly detection for DDoS might involve analyzing flow data (NetFlow/sFlow/IPFIX from routers) to see if incoming traffic exceeds learned normals for a particular interface or service. Many organizations set up automated alerts such that if traffic goes, say, 20% above the highest baseline peak, a DDoS alarm is triggered.
Once a DDoS anomaly is detected, the system can either automatically activate countermeasures (for instance, instructing border routers to black-hole traffic from certain source IPs, or signaling a cloud mitigation service) or alert operators to take action. The goal is to mitigate the attack before it significantly impacts users. Anomaly detection systems often integrate with DDoS protection tools. For example, Kentik’s solution can work with cloud mitigation providers like Cloudflare or Radware via integrations to stop the attack as soon as it’s identified.
Network anomaly detection is the frontline for DDoS defense. Without effective anomaly alerts, a DDoS attack might go unnoticed until services actually crash. With it, many attacks can be detected and defused proactively.
Intrusion Detection and Threat Hunting
Beyond DDoS, anomaly detection is a powerful mechanism for catching various network-based threats. Traditional intrusion detection systems (IDS) often use signature-based methods, but anomaly-based detection adds an extra layer that can catch novel or stealthy attacks. For example, if a normally quiet database server suddenly begins sending large volumes of data to an external IP at 3 AM, that’s a red flag — possibly indicating data exfiltration by an attacker. Similarly, if there’s a spike in DNS queries to rare domains or a surge of failed login attempts across many servers (potentially indicating a brute-force attack), these are anomalies worth investigating.
Network anomaly detection tools can uncover port scans, where an attacker systematically checks which ports are open on a host (this might appear as a host sending small amounts of traffic to a sequence of many different ports, deviating from normal behavior). They can also detect botnet activity. For example, if multiple internal hosts start beaconing out to an uncommon external address or periodically communicating in patterns typical of command-and-control, such anomalies can be highlighted.
Many security teams also use anomaly alerts as starting points for threat hunting–proactively looking for evidence of compromise. Rather than waiting for an alert, they might query their anomaly detection system for anything unusual in the last 24 hours or unusual patterns in network logs. Platforms like Kentik even enable exploratory analysis of traffic to discover attacks that weren’t anticipated by pre-set alerts.
By continuously monitoring and learning, an anomaly detection system can also help identify misconfigurations or policy violations. For example, if a firewall is misconfigured and suddenly backup data is flowing through an unexpected path, the anomaly engine may catch the unusual traffic route. In cloud networks, anomaly detection might flag if a normally isolated environment starts communicating with the internet (potentially due to a misconfigured security group). Thus, anomaly detection isn’t just about external attacks—it also helps maintain good network hygiene and compliance by spotting out-of-policy events.
Network Performance and Reliability
While security is a major focus, network anomalies can also indicate performance and reliability issues. NetOps professionals use anomaly detection to catch problems like sudden latency spikes, traffic blackholing, or outages. If a critical link in the network is experiencing packet loss or an unusual drop in throughput, an anomaly detection tool will notice the deviation from normal performance metrics. For example, if average latency on a WAN circuit jumps 5× higher than baseline, or application traffic volume drops to near-zero when it should be steady, these could point to network malfunctions, congestion, or outages that need attention.
Real-time anomaly alerts for performance metrics reduce the mean time to detect (MTTD) issues, which also enables faster resolution. Instead of finding out about an outage from end-user complaints, NetOps can be proactively alerted that “traffic to Data Center X is abnormally low compared to baseline” or that “error rates on interface Y spiked above normal levels,” allowing them to investigate link failures, routing issues, or device problems.
In this sense, anomaly detection contributes to network reliability by ensuring that deviations in performance (not just security incidents) are caught. Some advanced systems unify both performance monitoring and security anomaly detection into one platform, since the underlying telemetry (network flow data, SNMP device data, etc.) can serve both purposes. Kentik, as a network observability platform, is designed to detect both performance anomalies and security threats in real time, so NetOps teams get a holistic view of network health.
Anomalies can signal performance or security issues alike. For example, Kentik’s DNS monitoring and synthetic DNS tests track which IPs are returned by resolvers, response codes and resolution behavior from multiple vantage points. Unexpected changes or anomalies in DNS responses or resolver behavior, especially when correlated with routing and traffic data, can indicate hijacking or cache-poisoning activity.
Digital Forensics and Incident Response
When a security incident does occur, having a record of anomalies is extremely valuable for digital forensics. Network forensics is a branch of digital forensics that deals with capturing and analyzing network traffic to understand cyber incidents. An anomaly detection system often logs all the unusual events and patterns it has seen. These logs, combined with full network flow records, become a treasure trove for investigators trying to piece together what happened during a breach.
For example, imagine your organization discovers that a server was compromised last week. By turning to your network anomaly detection logs and data, you might find that three days before the breach was detected, there was an anomaly: that server started communicating with an external IP it never contacted before, and transferring large amounts of data (which was flagged as unusual). That is a crucial clue. Investigators can follow that lead to see if data was exfiltrated, what information might have been stolen, and how the communication took place. Additionally, anomaly records might show if the compromised server scanned other internal systems (indicating lateral movement) or if there were anomalous login attempts on it leading up to the incident. All this helps paint a timeline of the attack.
Platforms that specialize in anomaly detection and network observability often retain full-fidelity network data for a period of time, specifically to facilitate such forensic analysis. They don’t just keep summary statistics, but the detailed flow logs of communications. For example, Kentik’s platform captures and stores complete flow records and enriched data, so that every communication involving a host can be reviewed during an investigation. This comprehensive visibility is critical for forensic analysis because it provides a complete picture of network activity around the time of an incident. Investigators can ask questions like: When did the attacker first appear? Which systems did they talk to? Was there any command-and-control traffic? Was data sent out, and to where? With full network logs and anomaly annotations, these questions can be answered by analyzing the recorded evidence.
To illustrate how Kentik can be leveraged in a forensic analysis scenario, let’s consider a hypothetical security incident explained by Phil Gervasi in his video “How to perform a forensic analysis after a security breach”:
Digital forensics also benefits from anomaly detection by focusing investigators’ attention on the most suspicious events. Rather than combing through millions of log lines blindly, analysts can start with the timestamps and connections that were flagged as anomalous and often find the smoking gun. For example, an anomaly might have been flagged for “unusual SSH connection from a new IP” on a critical server. Upon examining that event, the team may uncover the point of entry of an attacker. Without anomaly detection, such subtle clues might be overlooked in the noise.
Network anomaly detection systems not only detect and alert in real time, but they also generate a historical trail of bread crumbs for any future incident response. They support digital forensics by ensuring that when an incident needs investigation, all the relevant network data (especially the abnormal activities) are readily available and highlighted. Organizations leveraging these tools can significantly enhance their incident response and forensic capabilities, ultimately reducing the mean time to understand and contain breaches.
Kentik’s Capabilities vs. Other Network Anomaly Detection Solutions
Kentik is a leader in the network anomaly detection space, and its approach brings together large-scale data analytics, real-time intelligence, and ease-of-use in a way that distinguishes it from many competitors. Let’s compare some of Kentik’s key capabilities with other solutions in the market.
SaaS & Big Data Scalability
Kentik’s platform is built on a scalable big data backend that can ingest massive volumes of telemetry in real time—including NetFlow, sFlow, IPFIX, BGP routing data, SNMP, streaming network telemetry, and more. This means it can monitor traffic across very large networks (service provider-scale or large enterprise) without issues. Many traditional network monitoring tools, by contrast, struggle at scale or only sample a fraction of traffic. Some competitor solutions might require expensive proprietary hardware to handle high throughput, whereas Kentik’s SaaS platform leverages cloud-scale processing to dynamically handle load. The result is that Kentik can provide a more comprehensive view of network activity, analyzing every interface, every flow, and every prefix, which is crucial for thorough anomaly detection.
Adaptive Baselining and Fewer False Positives
One of the foundational contributions of machine learning is adaptive baselining, or, learning what “normal” looks like for a given network over time. Instead of relying on static thresholds, ML models account for daily cycles, weekly patterns, and long-term growth trends, dramatically reducing false positives.
Kentik’s anomaly detection engine combines adaptive baselining with AI Advisor–driven context, allowing teams to quickly understand why something was flagged. For example, when traffic exceeds expected baselines, AI Advisor can help explain whether the anomaly aligns with historical growth, a routing change, or a potential security event without requiring operators to manually correlate multiple data sources.
Real-Time Alerting and Speed of Detection
Kentik is designed for real-time, always-on analysis. The moment an anomaly is detected, it can trigger alerts via multiple channels (email, Slack, PagerDuty, etc.) or even trigger automated mitigations. Some other solutions might operate on batch data or with delayed processing intervals. A traditional flow analyzer might update graphs every 5 minutes, which could delay detection of a fast attack. Kentik’s streaming analytics catch issues in seconds, giving it an edge, especially for time-sensitive threats like DDoS attacks.
While Cisco’s Secure Network Analytics (Stealthwatch) and other NDR (Network Detection and Response) tools also emphasize real-time detection, Kentik’s cloud-native architecture often means quicker deployment and updates (e.g., no appliances to rack or software to install on-prem). In practice, users have noted that Kentik enables them to detect and respond to anomalies faster and with less manual tweaking compared to some legacy competitors.
Integrated DDoS Detection and Mitigation
Many network anomaly detection solutions can identify DDoS attacks, but Kentik goes a step further by tightly integrating detection with mitigation options. Kentik Protect is an automated DDoS detection and defense system that not only detects attacks with high accuracy, but can also automatically trigger mitigations via BGP Flowspec or signaling to scrubbing centers and cloud mitigation providers. This end-to-end handling of DDoS incidents (from detection to stopping the traffic) often requires multiple products in other vendor ecosystems. For example, a competitor might detect the attack in a network monitoring tool, but you’d need a separate DDoS appliance or service to handle mitigation, and manual coordination between them. Kentik provides a more seamless solution in one platform.
Additionally, Kentik’s anomaly detection for DDoS benefits from field-proven algorithms. It boasts one of the industry’s most accurate DDoS detection engines, with about 30% better attack recognition accuracy over legacy systems. This is a significant differentiator when every minute and every false decision (blocking legit traffic or missing an attack) counts.
Full-Fidelity Data and Forensics
A major advantage of Kentik is that it retains full-resolution network data, rather than summarizing it too heavily. This ties back to digital forensics: Kentik stores details of traffic flows and anomalies for a longer period, so you can go back in time and deeply investigate incidents. Many competitors, especially older NetFlow analyzers, aggregate or roll up data after a short window due to storage limits. They might keep only 5-minute summaries after 24 hours, as an example.
Kentik’s efficient cloud storage and big data technology means you can often query very granular data from days or weeks in the past. One direct benefit is the ability to “double-click” on an anomaly alert and drill down to see the raw details (source IPs, destinations, protocols, etc.) involved. Legacy solutions often cannot do this because they simply don’t store the detail. They might tell you an anomaly happened, but not allow you to zoom into specifics because the data was averaged. Kentik users have the ability to investigate anomalies in depth, pivoting on different dimensions to understand exactly what happened. In effect, Kentik combines the roles of anomaly detector and forensic analysis tool, whereas competitors might require exporting data to a separate tool or might not have the data at all.
Ease of Use and Deployment
Kentik, being a cloud-based SaaS platform, means deployment is generally quick and straightforward—just point your network data (flows, etc.) to Kentik’s ingestion and you get up and running swiftly. Some competing solutions (like certain on-premises NDR appliances or open-source tools) can require complex installation, tuning, and maintenance. Kentik offers a modern web application interface with intuitive dashboards and query tools (Kentik’s Data Explorer, Kentik Journeys) to visualize anomalies, whereas others might have less user-friendly interfaces or require writing queries manually. Additionally, Kentik’s solution is built with both NetOps and SecOps in mind, providing value for network performance monitoring and security use cases in one product. Kentik’s broad approach can potentially replace multiple disparate tools, simplifying an organization’s tooling stack.
Best Network Anomaly Detection Tools: The Competitive Landscape
Leading network anomaly detection tools include Kentik, Cisco Secure Network Analytics (Stealthwatch), Arbor Networks (for DDoS protection), Darktrace (which uses AI for anomaly detection), ExtraHop, and cloud-focused monitoring tools like Datadog or New Relic (which have anomaly detection features for network/application metrics).
Each has its strengths. For example, Darktrace is known for its AI algorithms, and Arbor for its DDoS expertise. But Kentik often differentiates by offering a more complete and user-friendly package for network observability. Unlike single-purpose tools, Kentik covers a wide range of needs (traffic analysis, DDoS, performance, cloud visibility, etc.) with anomaly detection woven throughout.
This comprehensive approach means Kentik can often replace or augment legacy systems with one unified platform. Additionally, Kentik’s focus on Internet-scale data (including BGP routing analysis, peering analytics, etc.) goes beyond what many basic anomaly detectors provide. For an organization looking to not only detect anomalies but also understand network behaviors in a broader sense (e.g., capacity planning, cost optimization, peering decisions), Kentik can be an extremely attractive option.
When comparing Kentik to other network anomaly detection solutions, Kentik excels in scalability, accuracy, integration, and depth of insight. It leverages artificial intelligence, machine learning, and SaaS technologies in a way that many older tools do not, providing real-time anomaly detection with rich context. While other tools might catch some anomalies, Kentik’s aim is to ensure you see everything across your network and have the tools to act on it quickly. As a result, Kentik has become a go-to platform for NetOps professionals who need both powerful anomaly detection and comprehensive network intelligence in their day-to-day operations.
Learn More About Kentik for Network Anomaly Detection
Network anomaly detection has become an indispensable practice for any organization that values the reliability, performance, and security of its network. By continuously monitoring for abnormal patterns and unusual events, NetOps and SecOps teams can stay one step ahead of outages and cyber threats.
Kentik’s network observability platform offers industry-leading anomaly detection capabilities. It ingests diverse telemetry, applies adaptive baselines, and enables deep forensic analysis. With Kentik, you can detect threats faster, troubleshoot issues more efficiently, and make informed decisions to keep your network running smoothly. To see how Kentik can bring the benefits of network observability to your organization, request a demo or sign up for a free trial today.
FAQs about Network Anomaly Detection
How can I baseline normal network behavior and detect anomalies?
Kentik continuously stores flow and telemetry data, letting you build a baseline of normal traffic patterns. Deviations from that baseline such as unusual destinations, volumes or protocols can then be flagged via queries or alerts as anomalies that need investigation. Kentik’s anomaly detection engine combines adaptive baselining with AI Advisor–driven context, allowing teams to quickly understand why something was flagged. For example, when traffic exceeds expected baselines, AI Advisor can help explain whether the anomaly aligns with historical growth, a routing change, or a potential security event without requiring operators to manually correlate multiple data sources.
What techniques help identify shadow IT or rogue services from network telemetry?
By continuously ingesting flow, BGP, and telemetry data, Kentik lets you filter and query traffic by IP, AS, geo, port, and service — making it possible to surface unexpected traffic patterns, unusual external connections, or traffic to forbidden countries. These anomalies can flag shadow-IT services or rogue traffic so you can investigate further.
How can I detect asymmetric routing and its impact on network performance?
Because Kentik correlates flow traffic with routing/BGP metadata and interface telemetry, you can compare inbound vs outbound paths, detect mismatched AS-paths or next-hop asymmetry, and spot when asymmetric routing correlates with latency, packet-loss or throughput issues. This gives clear insight into routing-driven performance problems.
How can I detect DNS hijacking or cache poisoning via anomaly detection?
Kentik can surface suspicious DNS-related traffic patterns — such as unusual spike in DNS queries, unexpected source/destination IPs, or anomalous routing to unknown DNS resolvers — by analyzing flow metadata and AS/BGP data.
What’s the fastest way to find root cause of elevated latency?
The fastest way to track down elevated latency in Kentik is to pair automated measurement with AI-assisted analysis. Kentik Synthetics continuously measures latency and jitter across your critical paths, while the platform correlates those metrics with flows, BGP routes, and interface health. When latency spikes, Kentik AI Advisor and Cause Analysis let you ask natural-language questions against all that telemetry, quickly surfacing which path, provider, device, or policy change lines up with the problem—shortening time-to-root-cause compared to manual CLI and ad-hoc graph hunting.
How do I detect traffic spikes that may indicate botnets or scrapers?
Detect suspicious spikes by baselining normal traffic and alerting on sudden surges, then drilling into who/where/what. Kentik lets you investigate spikes with flow analytics and Network Classification (inside/outside), and it can enrich flow records with Spamhaus reputation data so you can filter/group by Threat List Host and Botnet C&C to quickly identify known malicious activity.
How do I detect shadow IT SaaS usage in network traffic?
Detect shadow IT by identifying unexpected destinations and services in your telemetry, especially new SaaS domains, unfamiliar ASNs, and unusual outbound flows that bypass approved paths and controls. Kentik supports this by letting teams analyze traffic by IP, AS, geography, port, and service and surface anomalous external connections that indicate unapproved SaaS usage.
What tools help reduce false positives in network anomaly detection?
Tools reduce false positives by learning adaptive baselines for your environment, using multi-dimensional signals instead of static thresholds, and adding investigation context so operators can quickly see whether a deviation is benign growth or a real incident. Kentik supports this with adaptive baselining plus investigation context so teams can understand why something was flagged and whether it aligns with historical patterns or meaningful change.