8 reasons why network observability is critical for DDoS detection and mitigation

Summary
Learn eight ways that network monitoring can be critical for DDoS detection and mitigation.
Distributed denial-of-service (DDoS) attacks have been a continuous threat since the advent of the commercial internet. The struggle between security experts and DDoS protection is an asymmetrical war where $30 attacks can jeopardize millions of dollars for companies in downtime and breaches of contract. They can also be a smokescreen for something worse, such as the infiltration of malware. In addition to ever-larger traffic volumes, attackers are also increasing their target diversity, with attack traffic simultaneously spanning data, applications, and infrastructure to increase the attack’s chances of success.
At Kentik, we see thousands of DDoS mitigations activated each week. DDoS attacks continue to increase in number, volume, and sophistication. A June 2022 blog post by our partner Cloudflare detailed one of the largest and most powerful DDoS attacks ever — the Mantis botnet was able to launch an attack that generated 26 million HTTPS requests per second!
The cost to undertake DDoS attacks is plummeting, while the tools for carrying them out are becoming more sophisticated.

Why launch a DDoS attack?
There are many motivations for initiating a DDoS attack. Many are political, some are motivated by competition, and others are out of spite — such as disgruntled/former employees. Perpetrators can bring a target’s infrastructure to its knees, leveraging the situation to extort money, information, or apply negotiation pressure.
DDoS attacks are also used as a smoke-screen for other more insidious attacks, such as the introduction of malware or a more overt crime, like theft.
DDoS protection with network observability
Early detection and mitigation are critical for businesses that want to protect themselves against a DDoS attack. Some DDoS attacks are sophisticated enough to successfully shut down large servers, and even completely disable a target’s network. This severe disruption to services and applications can result in direct revenue loss and damage to a brand’s reputation.
Network observability can help you detect and mitigate malicious or accidental cybersecurity threats at their onset.
Here are our top eight reasons why network observability is critical for defense against modern DDoS attacks:
1. Early detection
The importance of early detection and mitigation of a DDoS attack cannot be overstated. It will save you time, frustration, revenue, brand equity, and help you keep your infrastructure secure. Leading network observability solutions will understand your traffic by analyzing your real-time and historic NetFlow data, constantly comparing this traffic flow data against benchmarks to catch anomalous traffic patterns, giving network and security engineers what they need most: the awareness and time to mitigate the attack and protect their network before it does damage.
2. Detecting low-volume attacks
When most people think of DDoS attacks, they think of massive volumetric attacks that crash websites or networks. In reality, most DDoS attacks are small in size and duration, often less than 1 Gbps and only a few minutes long, making them difficult to detect. DDoS detection tools are often configured with detection thresholds that ignore or don’t see these attacks. These low-volume attacks are often used to mask security breaches. Hackers will use a DDoS attack to distract SecOps, while simultaneously launching a more rewarding security breach. The security breach could involve data being exfiltrated, networks being mapped for vulnerabilities or infiltration of ransomware.
Network observability solutions allow you to baseline against small traffic volumes, enabling network engineers to fine-tune thresholds and alerts accordingly.
3. Granular identification of traffic sources
Identifying where traffic originates and normal traffic flows from those sources is keystone data to a defense strategy. The context-rich telemetry that network observability solutions leverage includes critical network information like geolocation.
To protect your infrastructure, you need to be able to build policies based on certain geographies, such as an alert if the traffic is from an embargoed country. Being able to identify the source of the traffic can help tremendously in the detection of security breaches. Identifying traffic from an unusual traffic source may be the key to early mitigation.
4. Understanding the attack in context
SNMP data is not enough! Flow data gives you the ability to understand the attack in context. It gives details on where the attack is coming from, as well as what IP addresses, ports, or protocols make up the attack.
This context helps with mitigation by being able to understand the nature of the attack better, as well as apply more accurate filters against the traffic.
5. Determining the effectiveness of mitigations
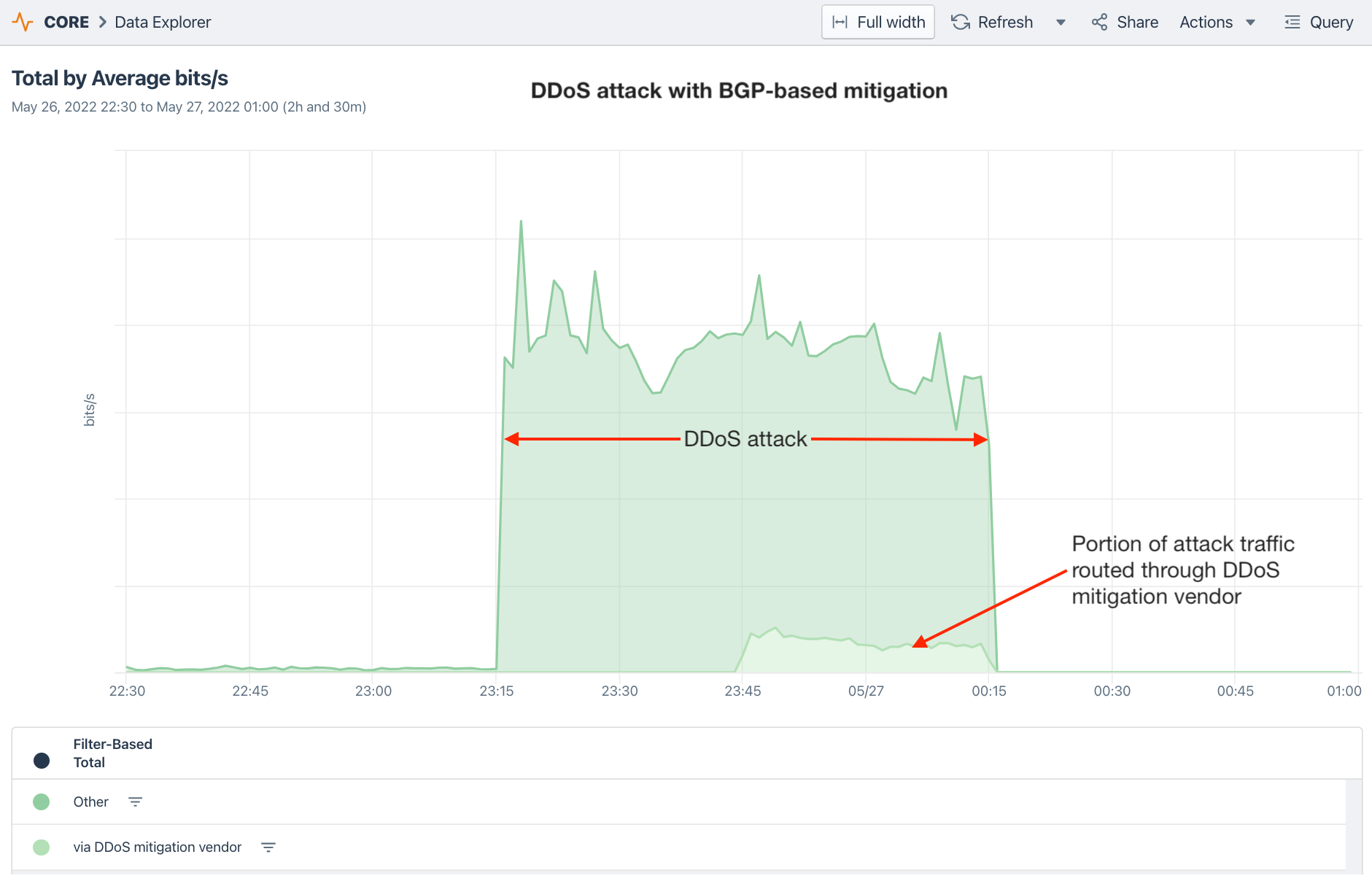
Mitigation services and technologies sometimes don’t achieve full coverage and attack traffic can circumvent the mitigation leaving you exposed. It’s important to be able to use NetFlow to analyze what DDoS traffic has been redirected for scrubbing and what traffic has been missed. And perhaps just as important, being able to monitor BGP from hundreds of vantage points can enable you to understand how quickly your mitigation service achieved full coverage if it did at all.
The BGP visualization below shows a DDoS mitigation vendor (purple) appearing upstream of the customer network but never achieving complete coverage of the customer network. Below that, we can see the result of this incomplete activation as only a portion of DDoS traffic is ultimately redirected to the DDoS mitigation vendor. An incomplete DDoS mitigation permits attack traffic to reach the target network, imperiling critical services.

6. Performing attack forensics
Many DDoS attacks fit a pattern. Many of the same bad actors perpetuate them and their fingerprints aren’t always obvious. A good network observability solution will allow you to look back in time to understand, have we seen this attack before? Are there patterns? How can this be prevented altogether?
7. Eliminating false positives
Without a network observability platform that gives you granular traffic analysis, automated mitigations can cause you to filter traffic that is needed by your end users. This can result in you causing an outage for your users in an attempt to block an attack.
False positives can be a big distraction for your SOC team. Alerts that, upon investigation, are revealed to be normal traffic result in alert fatigue. Eventually, your security experts will stop paying attention to the noise, leaving you open to malicious attacks.
8. Controlling costs
DDoS traffic can cause havoc in 95/5 pricing models and always-on mitigation services can be expensive. True network observability will give you the ability to detect attacks at their onset, decreasing the chances of exceeding traffic limits, protecting your infrastructure, and giving you the ability to engage a mitigation service before the attack takes hold.
Takeaways
Network observability provides an unmatched solution for detecting and mitigating DDoS attacks, and, for these eight key reasons, is critical for DDoS defense in the modern network:
- Early detection
- Detecting low-volume attacks
- Granular identification of traffic sources
- Understanding the attacks in context
- Determining the effectiveness of mitigations
- Performing attack forensics
- Eliminating false positives
- Controlling costs
Watch this short video to learn how Kentik can help you defend your network:
Also, check out the Kentik Protect solution brief.
You can find all of our latest resources about DDoS attacks, BGP hijacking, and other network security threats in our DDoS protection and network security package.



