Automated, Accurate, Flexible DDoS Detection and Mitigation
Summary
From a threat actor’s side, launching a DDoS attack is both easy and cheap. For a business, it’s costly, disruptive and comes with big hurdles for effective detection and mitigation. Kentik Protect can help.
Gaming, finance, hosting, you name it: many digital businesses today are under DDoS attack. Why? From the threat actor’s side, launching one of these attacks is both easy and cheap. On the Dark Web, DDoS-as-a-service can be purchased for as little as $10 per hour and requires almost no technical sophistication to deploy. Not to mention, the reward (usually in the form of a service disruption) can quickly be reaped.
On the other hand, it can be quite a costly experience for a business. One study suggests the loss is anywhere from $20,000 – $40,000 per hour as a business’ sites and services are taken down. That hardly scratches the surface when you add in the toll taken on reputation. So, what can be done?
Challenges with Current DDoS Mitigation Approaches
DDoS attacks are hardly new, and there are many different approaches to mitigation. Traditionally, enterprises “scrub” DDoS traffic, but that requires investment in dedicated, costly appliances and specialized knowledge in attack mitigation, so it has become less common.
Instead, many companies choose to outsource the entire mitigation process. While this approach eliminates the need for on-premises hardware, there are two major drawbacks:
-
Limited flexibility: When DDoS protection is outsourced to a single vendor, organizations cannot benefit from integrations with solutions that are better suited for specific attacks and mitigation needs.
-
Poor analytics: The outsourced service focuses on identifying and triggering DDoS mitigation. That means you’ll have little visibility into the nature of the attack (e.g., type, origin, volume, parallel threats… was it really an attack?). Without analytics, little can be learned from the attack to understand its impact and prevent future or persistent ones.
Without the ability to dig deeper into the incident, you won’t be able to assess your detection and mitigation strategy, know if it was actually an attack and not caused by something like a misconfiguration, make changes and/or deploy new techniques.
Using Kentik to Detect and Mitigate DDoS Attacks
Kentik Protect is the automated, flexible and insights-driven solution for DDoS attacks. We built this solution for enterprises and service providers to effectively monitor infrastructure and reliably detect and mitigate DDoS attacks at their outset. Just a few of the benefits include:
-
Accuracy: The ability to accurately differentiate actual attacks from benign traffic is a key advantage of Kentik Protect. Simplistic DDoS detection policies based on static thresholds will not maintain accuracy over time, while behavioral-based approaches suffer from false positives. Kentik Protect uses fine-grained policies, ML-based detection and timely updates of new threats to deliver higher accuracy and effectiveness in the detection of attacks.
-
Automation: Once an attack is identified, Kentik Protect supports either automated or manually triggered traffic redirection to scrubbing infrastructure, or it can signal upstream infrastructure to drop traffic completely.
-
Informed decision making: Context-rich detection also enables better decisions on the type of mitigation applied. For example, a high-volume attack should be directed to a mitigation service that can handle it, while other lower-volume attacks might be handled locally.
-
User-experience understanding: When combined with our synthetic testing solution, Kentik Synthetics, Kentik Protect allows you to evaluate the actual application user experience worldwide both during the attack and as mitigation actions are implemented.
How Does Kentik Protect Work?
Kentik Protect uses standards-based protocols (RFC-3882 RTBH or RFC-5575 Flowspec) and ubiquitous network services (e.g. NetFlow, IPFIX, BGP) to integrate with a wide variety of DDoS mitigation solutions and capabilities. Crucially, it also provides detailed traffic analytics to understand the attack and the effects of mitigation tactics in real time.
DDoS mitigation using Kentik Protect is a straightforward process, as shown below. Kentik Protect supports the policy management, traffic flow data analysis and DDoS detection, and relies on scrubbing or network infrastructure to execute the mitigation policy:
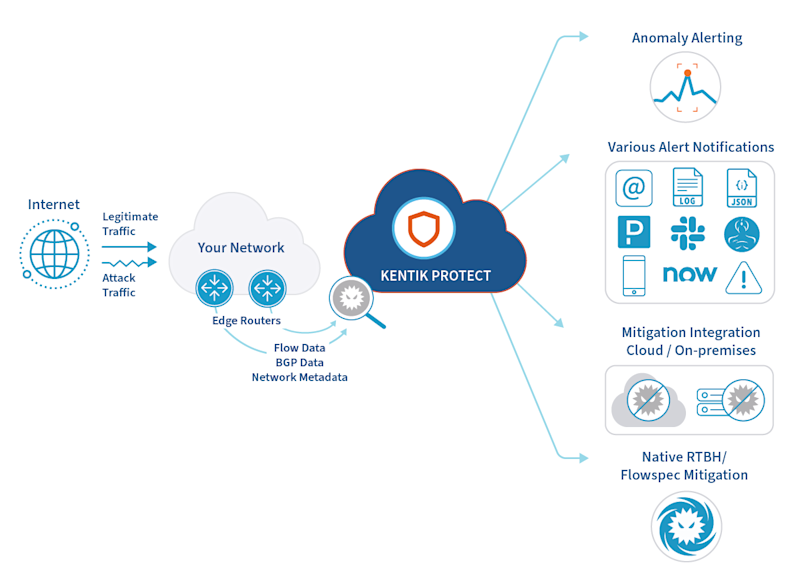
Kentik Protect is simple, efficient and effective. The solution delivers quick time-to-value. It neutralizes attacks at the infrastructure edge and provides visibility of network flows, trends and capacity bottlenecks. DDoS policies can be automated or manual depending on the operational model of the organization.
Unlike virtually all alternatives, Kentik Protect also enables the discovery of “sneak attacks” that may be using DDoS to hide, and doesn’t produce false-positives based on inaccurate behavioral analysis. And as a SaaS solution, deployment, threat updates and ongoing management of the solution itself is extremely simple.
Sleep better at night. Check out Kentik Protect for yourself with this free trial or get a demo with a Kentik expert.



