Next-Generation Network Monitoring
You can’t buy time, but you can replace your antique NMS.
Unify your telemetry
- Onboard all your gear: Get vendor-agnostic network monitoring for any device out of the box.
- Future-proof monitoring: Ingest streaming telemetry and custom metrics with the same system that polls SNMP.
- Centralize, modernize: Monitor and interrogate on-prem devices alongside traffic analysis and metrics from hybrid and multi-cloud infrastructure.
Run your network like it’s 2026
- Today’s monitoring, finally: Equip experts with natural language query and troubleshooting assist to dig deep into complex networks.
- Poll faster, act faster: Use faster polling to know what’s broken faster, so the team can fix it faster.
- Unlock streaming telemetry: Reduce monitoring strain by leveraging event-based monitoring for your most important (and most expensive) gear.
Boost efficiency — not cost
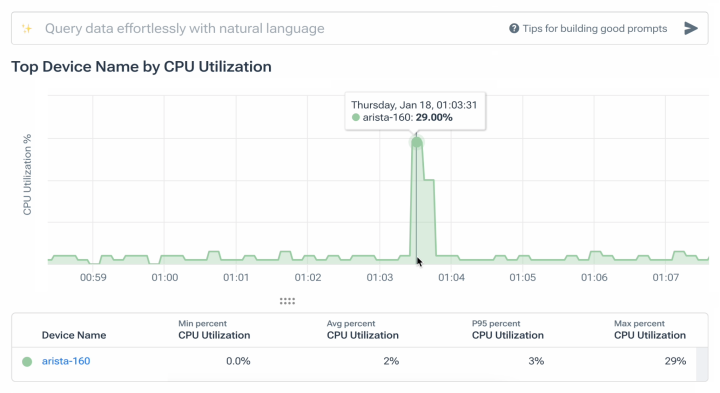
- Shrink MTTR: Identify root cause quickly with traffic pattern insights and a holistic view of device health.
- Optimize device lifecycle management: Plan, scale, and report on capacity and performance in one platform.
- Monitoring, covered: Get the alerts, device support, and integrations you need to be productive, minus the maintenance.
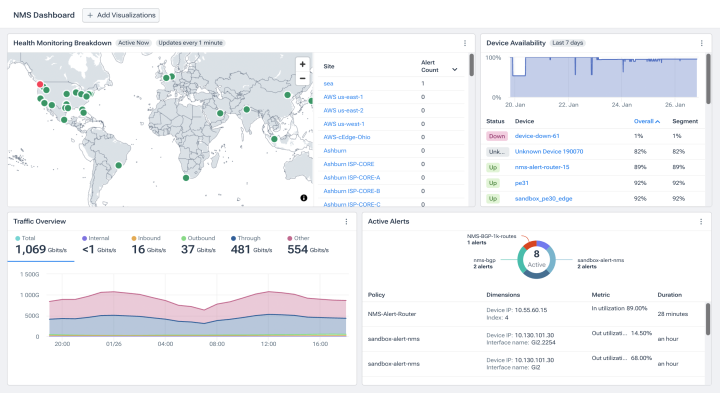
Connect the dots instantly
- Get real-time data: See metrics from all protocols and device flavors with fast polling that defaults to every minute.
- Consolidated tools, correlated telemetry: Map what’s happening on the box to real traffic anomalies and trends in one view.
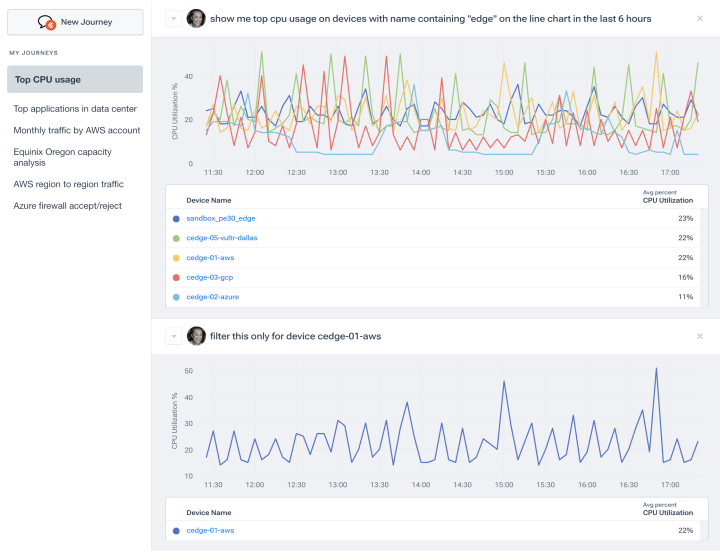
- Query with one fast engine: Explore streaming telemetry, SNMP, and custom metrics from any collector, with the option to ask in natural language.
Do more than keep the lights on
- Eliminate monitoring overhead: Detect faulty network devices with the continuous monitoring and alerts you need, delivered as SaaS.
- Answer any question about your network: Kentik AI makes it easy to rapidly troubleshoot complex issues.
- Deliver exceptional application experiences: Proactively address network issues before they impact users by combining metrics, traffic analysis, and synthetic testing.

“We are switching to Kentik NMS to support our many network devices. The nice, simple dashboard provides all the NMS metrics we need for troubleshooting. Kentik NMS’ extensibility makes it easy to integrate to our internal tools through APIs.”
Network Monitoring FAQs
What is a Network Monitoring System?
A Network Monitoring System (NMS) is a platform that continuously observes a network’s health and performance. It collects and analyzes data from devices like routers, switches, and servers to identify and troubleshoot issues. An NMS provides real-time insights, alerts for potential problems, and comprehensive reports to ensure optimal functionality. By monitoring traffic, detecting anomalies, and generating actionable insights, network monitoring systems help maintain network reliability and efficiency, which are crucial for business operations and security.
What devices and platforms does Kentik’s Network Monitoring System support?
Kentik’s Network Monitoring System supports a wide range of devices and platforms, including:
- Network devices: Cisco, Juniper, Palo Alto Networks, Fortinet
- Cloud platforms: Amazon Web Services, Google Cloud Platform, Microsoft Azure, Oracle Cloud Infrastructure
- Monitoring agents: Kentik Host Agent, ntop Host Agent
- SD-WAN solutions: VMware SD-WAN, Cisco SD-WAN, Silver Peak EdgeConnect
For more supported integrations, please visit Kentik’s Integrations page.
What makes Kentik NMS superior to legacy network monitoring tools?
Kentik NMS is unique in its unified telemetry, real-time data collection, and AI-assisted troubleshooting. Unlike legacy network monitoring solutions, it offers a zero-maintenance SaaS deployment with no hidden costs, integrating all network data into a single, user-friendly portal. This modern approach ensures faster, more efficient troubleshooting and scalability, making it ideal for today’s dynamic network environments.
What makes a Network Monitoring System one of the “best” options?
The best NMS platforms combine broad device coverage with modern telemetry (streaming telemetry), fast analytics, reliable alerting, and low operational overhead. For hybrid networks, it also helps when the NMS, like Kentik, can correlate device health with traffic and performance signals so teams can validate impact and troubleshoot faster.



