Summary
Today almost every type of organization must be prepared to mitigate DDoS attacks and proactively defend their networks. In this post, we discuss our newly added BGP Flowspec support in Kentik Detect. This enables our customers to have the granularity needed to detect attack traffic in real time and mitigate attacks faster.
Introducing Kentik’s New BGP Flowspec Support

Distributed denial-of-service (DDoS) attacks have been a continuous threat since the advent of the commercial Internet. Today, they are becoming increasingly prevalent and cause major financial damage to all types of organizations. In addition to ever larger traffic volumes, attackers are also increasing their target diversity, with attack traffic simultaneously spanning data, applications, and infrastructure to increase the chances of success. With many attacks stemming from totally unpredictable events like political dissent, employee misconduct, or actions of third parties, every type of organization needs to be prepared to mitigate DDoS attacks and proactively defend their networks to ensure business continuity.
Existing methods of DDoS mitigation present a number of challenges:
-
A high degree of coordination is required between customers and service providers. For example, during an attack, service provider network engineers need to be skilled at finding attacks, choosing an appropriate mitigation strategy, and have proper access to the infrastructure to apply it.
-
A common DDoS mitigation technique is Remotely-Triggered Black Hole (RTBH), which requires extensive pre-configuration of discard routes and/or uRPF on all edge routers. Any misconfiguration can lead to downtime or ineffective mitigation with business impact.
-
For destination-based RTBH, the victim’s destination IP address becomes completely unreachable. While this minimizes collateral damage to adjacent customers and infrastructure, the victim is still down. The mitigation actually “completes the attack.” The victim can update DNS to point at a different IP address in an attempt to get their application back up. However, if the attack is targeting the DNS hostname and not the IP address, the attack will just switch over to the new IP address.
-
Source-based RTBH only works for a small number of sources. It can’t scale to a large network perimeter or when the source of the attack is distributed across thousands of sources.
What is BGP Flow Specification (Flowspec)
Defined in RFC 5575, BGP Flow Specification (Flowspec) is a DDoS mitigation solution that allows you to rapidly deploy and propagate filtering and policing across a large number of BGP peers.
The basic elements of Flowspec are:
- Flowspec match:
A key concept from BGP is NLRI, Network Layer Reachability Information, which describes the network/prefix that the given BGP route matches. There are 12 NLRI attributes defined in BGP Flowspec. These attributes are added to the NLRI field within the BGP Update Message that’s advertised to peers and define the particular traffic that the Flowspec route will match.
| Type-1 | Destination Prefix |
| Type-2 | Source Prefix |
| Type-3 | IP Protocol |
| Type-4 | Port |
| Type-5 | Destination port |
| Type-6 | Source port |
| Type-7 | ICMP type |
| Type-8 | ICMP code |
| Type-9 | TCP flags |
| Type-10 | Packet length |
| Type-11 | DSCP |
| Type-12 | Fragment |
As you can see, these NLRI types go beyond what’s available in a traditional BGP NLRI, which contains a destination IP / prefix match only. With Flowspec you can match attack traffic much more granularly. You can even distinguish conversations flowing between individual pairs of IPs. This improved granularity can dramatically improve the kind of over-blocking that occurs with traditional RTBH.
- Flowspec action:
Flowspec uses BGP Extended Communities to define actions that routers will take for traffic matching the NLRI attributes from above.
| Action Type | Examples |
|---|---|
| traffic-rate | set to 0 to drop all traffic |
| traffic-action | sampling |
| redirect to VRF | Change Route Target (RT) |
| traffic-marking | DSCP value |
Why Flowspec is Better
Here are three key reasons why Flowspec is better:
- Flowspec has the same granularity compared to access control lists (ACLs), as it’s based on n-tuple matching.
- Flowspec has the same automation capability compared to Remotely-Triggered Black Hole (RTBH) routes. It’s now much easier to propagate filters to all edge routers in large networks.
- Flowspec leverages BGP best practices and policy controls. Familiar best practices used for RTBH can also be applied to BGP Flowspec.
Which Network Vendors Support Flowspec?
Flowspec has been around for a few years, so at this point, most of the major routing stacks that support BGP also support Flowspec. This includes open source routing daemons and commercial software from various networking vendors such as Cisco, Juniper, and Nokia (former Alcatel-Lucent).
Kentik Flowspec Support
To strengthen Kentik’s Security and DDoS solution, we have now added Flowspec as a mitigation method. In the first phase, Kentik supports:
- Manual Flowspec mitigation:
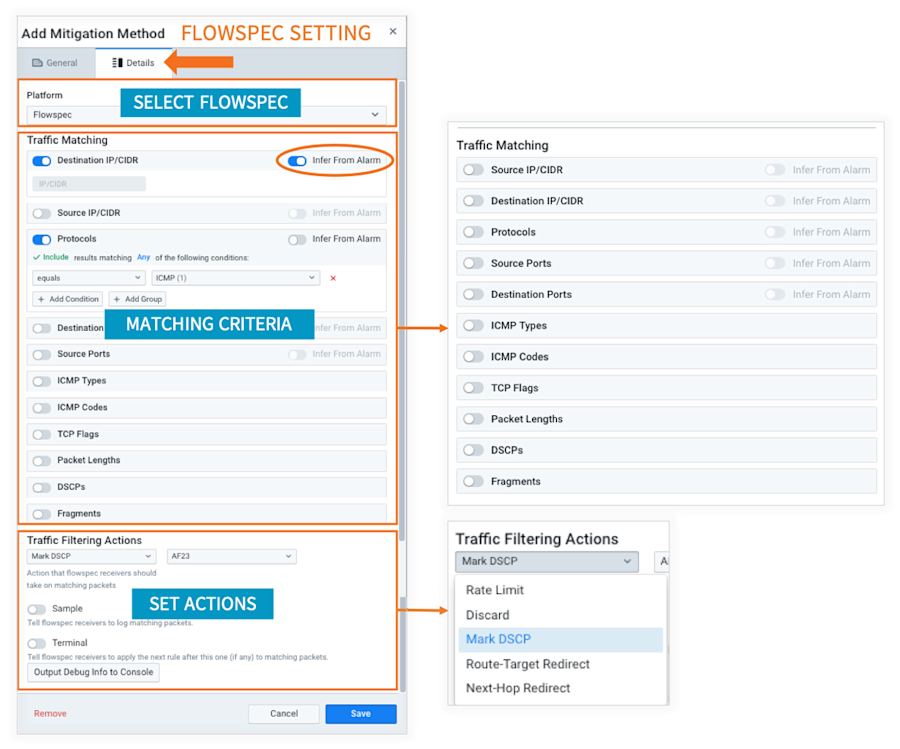

- Or, you can configure Flowspec as an automated mitigation method to associate with a particular alerting policy:

- You can also populate the Flowspec match criteria from the traffic details of the alarm that triggered the mitigation. This allows for dynamic, granular, fully-automated DDoS mitigation:

Stay tuned for more Flowspec functionality with additional auto-matching intelligence and automation options. For additional technical details, check out our Flowspec Mitigation topic in the Kentik Knowledge Base. Of note, Flowspec support is not turned on by default, so if you are interested in using this feature, please don’t hesitate to contact the Kentik Customer Success team at support@kentik.com.