Kentik Blog
























In the rapidly evolving telecom sector, the concept of “cloudification” is not just a trend but a transformative shift, reshaping how services are delivered and managed. This change is underpinned by modern software architectures featuring modularity, microservices, and cloud-native designs. As we embrace this new era, marked by the rise of “netcos” and “servcos,” we must also navigate the complexities it brings.
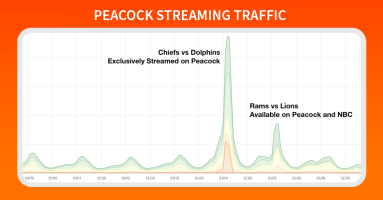
NFL playoffs are here, and Doug Madory tells us how Saturday’s first-ever exclusively live-streamed NFL playoff game was delivered without making any references to pop superstar Taylor Swift or her sizzling romance with nine-time Pro Bowler Travis Kelce.
Is SNMP on life support, or is it as relevant today as ever? The answer is more complicated than a simple yes or no. SNMP is reliable, customizable, and very widely supported. However, SNMP has some serious limitations, especially for modern network monitoring — limitations that streaming telemetry solves. In this post, learn about the advantages and drawbacks of SNMP and streaming telemetry and why they should both be a part of a network visibility strategy.
In this post, we share the joys and benefits of having pets while working from home. We discuss the scientific benefits of having pets around, including improved mental health and job performance and offer practical tips for working with pets. From providing moral support during meetings to adding fun to our workdays, our furry companions play a vital role in our daily routines at Kentik.
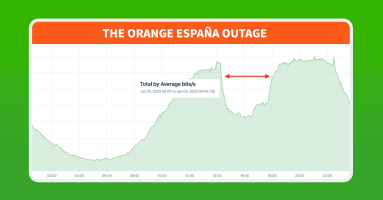
Orange España, Spain’s second largest mobile operator, suffered a major outage on January 3, 2024. The outage was unprecedented due to the use of RPKI, a mechanism designed to protect internet routing security, as a tool for denial of service. In this post, we dig into the outage and the unique manipulation of RPKI.
Kentik is excited to launch the Kentik Cares Giving Program, a year-round initiative that empowers employees to support the causes they care about. Starting in January 2024, Kentik will match employee donations up to $200 annually, fostering a culture of generosity and community engagement. This program reflects our ongoing commitment to making a meaningful impact and giving back to the communities we serve.
The year might be ending, but the Kentik news never stops. We’re back with our bite-sized roundup of everything you might have missed at Kentik in December 2023.
In this post, Doug Madory reviews the highlights of his wide-ranging internet analysis from the past year, which included covering the state of BGP (both routing leaks and progress in RPKI), submarine cables (both cuts and another historic activation), major outages, and how geopolitics has shaped the internet in 2023.
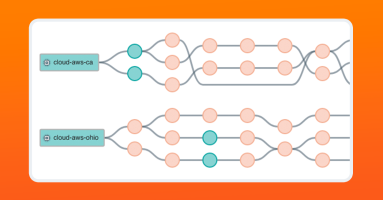
Modern networking relies on the public internet, which heavily uses flow-based load balancing to optimize network traffic. However, the most common network tracing tool known to engineers, traceroute, can’t accurately map load-balanced topologies. Paris traceroute was developed to solve the problem of inferring a load-balanced topology, especially over the public internet, and help engineers troubleshoot network activity over complex networks we don’t own or manage.
Despite the siren song of AI in the keynotes, visitors were far more focused on solving real-world problems. These are the issues that have plagued IT practitioners for years, if not decades: troubleshooting and validating performance and availability of their applications, services, and infrastructure.