Securing Your Network Against Attacks: Prevent, Detect, and Mitigate Cyberthreats

Summary
As networks become distributed and virtualized, the points at which they can be made vulnerable, or their threat surface, expands dramatically. Learn best practices for preventing, detecting, and mitigating the impact of cyberthreats.
As networks become distributed and virtualized, the points at which they can be made vulnerable, or their threat surface, expands dramatically. Multi- and hybrid cloud infrastructures add further complexity to securing threat surfaces, adding even more variability to permissions, configuration points for human error to enter the scene, and network boundaries to exploit.
This is compounded by recent trends of remote work, where network operators need to wrestle with the fact that employees often access the network via work sites with far less governance. Cyberthreat strategies have evolved in step with modern cloud networks, often using cheap, virtualized cloud resources to exploit the threat surface topology I briefly described above. As these attacks become more subtle and sophisticated, having real-time, largely automated responses from NetOps and SecOps becomes critical.
This article will examine what defines a network attack, the most common types of network attacks, and how network observability can protect your network against such threats.
What is a network attack?
A network attack is any attempt to gain access to or otherwise compromise the integrity or availability of a network. Network attacks come in many forms. Some are highly automated, machine-based attacks, while others are more subtle, relying on human vulnerability.
Guaranteeing network security and performance in the face of these attacks, whatever form they take, is one of the principal responsibilities of network operators today.
What are the most common types of network attacks?
Here are several of the most common attacks against enterprise networks:
- Distributed denial of service
- Man in the middle
- Privilege escalation
- Unauthorized access
- Insider threats
- Code and SQL injection
Let’s take a closer look at each of these types of network attacks.
Distributed denial of service (DDoS)
DDoS attacks are cyber attacks that most often have the purpose of causing application downtime. This downtime can itself be the ultimate goal for the attacker. Still, it can also be used to weaken security systems, cover tracks, or act as a red herring for investigators. At the same time, a more significant vulnerability is exploited elsewhere in a network. These attacks can involve coordinating thousands of virtual or otherwise devices to overwhelm the target server’s resources.
There are three main types of DDoS attacks:
- Volume-based. These attacks aim to overwhelm a service’s bandwidth capabilities with prohibitively high traffic volumes. Common volume-based DDoS attacks are ICMP and UDP floods.
- Protocol-based. These attacks overwhelm network infrastructure resources, targeting layer 3 and layer 4 communication protocols. Common protocol-based attacks are Ping of Death, Smurf DDoS, and SYN floods.
- Application layer. These attacks typically seek out web server vulnerabilities with malformed or high-volume requests in layer 7 services. Common application layer attacks include HTTP floods and slowloris.
Man in the middle (MITM)
MITM attacks use false or redirected interfaces to exploit vulnerabilities in both human and machine-based protocols.
For a little more detail, here are some of the main MITM attacks levied against networks:
- Spoofing. A hallmark MITM strategy, wherein a malicious agent intercepts and redirects traffic with false credentials. The attacker can spoof IP addresses, DNS, HTTPS headers, and more to deceive users into interacting with compromised applications.
- Hijacking. This type of attack involves compromising a network component and intercepting incoming traffic. BGP hijacking has increasingly become a concern, as they cause changes to the routing of the internet’s autonomous systems and can cause severe disruption to a web application’s internet traffic.
Unauthorized access and privilege escalation
For access or privilege-based attacks, attackers rely on various techniques to gain the initial set of network credentials, including social engineering ploys like phishing, dark web data purchases, malware, password breaking, and many others. A surprisingly common exploit is default passwords on hardware that were never reconfigured upon installation.
Privilege escalation is a type of network attack that exploits poorly defined roles and security boundaries. Once unauthorized access has been achieved, malicious agents seek access to additional accounts/privileges to infiltrate the network further. Broadly speaking, there are two types of privilege escalation: horizontal and vertical.
In horizontal escalation, bad actors seek to “hop” laterally across similarly privileged accounts to find the data they are looking for. For example, gaining access to a sales rep’s account but using it to compromise the director of sales’s account to access customer account data. Vertical privilege escalation, on the other hand, seeks to move up the privilege scale. For example, moving from a sales rep’s account (basic user privileges) into a sysadmin’s account (admin privileges).
Insider threats
True to their name, insider threats can come from anyone with access to facilities, hardware, interfaces, or operational knowledge. Depending on their privileges, and the use of techniques like privilege escalation, these insiders are capable of causing actual harm to networks. Insider threats can be unintentional or malicious, but they present a very significant vulnerability for network and security specialists.
Most insider threat attacks can be grouped into one of two categories: espionage and sabotage. Espionage involves using network access to steal other network users’ personal, system, or IP data. Sabotage is less interested in preserving secrets and far more intent on destroying or disrupting data or network availability.
Injection
An injection attack is any vector that exploits input vulnerabilities in an application or network. Injection attacks focus heavily on exploiting bad programming practices that provide input opportunities where, when, or to whom there should be none.
File uploads, form fields, and a poorly designed API can all create injection opportunities.
Injection vectors include:
- SQL. Injection attacks that use SQL inputs to alter or otherwise corrupt servers. A common scenario is a poorly validated user login that accepts SQL statements.
- Code. Code injection attacks also make use of poorly validated inputs. But, instead of using the vulnerability to inject SQL commands, the attackers use application code to retrieve or alter data.
Using network observability to keep your network secure
NetOps and SecOps must work closely to ensure proper threat surface coverage for complex networks. While it is impossible to eradicate the possibility of an attack entirely, the tools and strategies of observability offer network specialists exciting new capabilities.
Prevention
The best-case scenario for an attack is that it is completely prevented. Security philosophies like zero trust help IT structure privileges, authentication, and device control around the idea that every user and entry point to the network should be vigilantly verified. In some cases, multi-factor authentication (MFA) has been shown to prevent up to 99.9% of automated password attacks.
From a networking perspective, a lot of valuable prevention data is available to engineers who know how to use it. Here are some of the top network data sources for attack prevention:
- Global IP reputation assessments. Prevent risky IP addresses from interacting with your network.
- BGP route leak detection. Find misconfigurations and bad code that expose your network’s Border Gateway Protocol routes to vulnerability.
- RPKI status checks. Know if any route containing your address space is being evaluated as RPKI-invalid. This would include accidental leaks, intentional hijacks, or a misconfigured Route Origin Authorization (ROA) that are causing your authorized route to be rejected.
- Previous attacks. Post-mortems provide valuable insights for strengthening network policies, updating hardware and software, and further optimizing security strategy.
Network observability solutions unify this data in a single pane of glass and provide the highly scalable data infrastructure necessary to collect, analyze, and adapt this information to highly automated attack prevention strategies.
Detection
Try as we might, attacks will still happen. This means early detection is the name of the game in network security, where minutes or even seconds of compromised security can have disastrous implications for an organization’s brand equity (and bottom line). A 2020 Neustar report on cyber threats and trends found that even though DDoS detection and mitigation needs to happen within a minute, as of November 2020, only 25% of DDoS mitigations are initiated soon enough.
Capable network observability solutions will automatically detect and alert on early signs of attacks, such as traffic spikes, excessive latency, traffic from unexpected regions, or other anomalous traffic behavior by analyzing your real-time and historical NetFlow data. This traffic flow data is constantly compared against benchmarks to catch anomalous traffic patterns. It gives network and security engineers what they need most: the awareness and the time to mitigate the attack and protect their network before it can cause damage.
Mitigation
Once an attack has been identified, it is essential to limit the impact. Mitigation strategies vary greatly depending on the nature of an attack. For traffic-based attacks like DDoS, strategies like remote-triggered black holes (RTBH) offer a way to re-route traffic toward harmless infrastructure. Service providers like Cloudflare and A10 are leaders in this space and integrate with Kentik Protect.
Whatever the mitigation strategy being deployed, effective network observability will feature integrations with leading cybersecurity tools to help foster seamless, automated mitigation of attacks.
Secure your network against attacks with Kentik
Kentik ingests and unifies, in real-time, massive volumes of NetFlow, sFlow, IPFIX, and BGP data, network performance metrics, and SNMP device and interface data. These rich telemetry sets power dynamic network maps and traffic visualizations and enable robust flow analysis to automate prevention efforts like botnet detection.
Once a threat has been identified, Kentik automates hybrid mitigation via standards-based BGP Flowspec and remote-triggered black hole (RTBH) and integrations with mitigation solutions from leading vendors, including Cloudflare, A10, Juniper, and Radware. Kentik’s integration with these services provides detailed monitoring that lets operators know for certain whether or not a mitigation effort was partial or complete.
The “ask anything” ethos of Kentik’s network observability enhances the ability to investigate and understand attacks with deep ad-hoc traffic analysis:
- Where did the attack come from?
- What paths were used?
- What protocols were leveraged?
- What customers were affected?
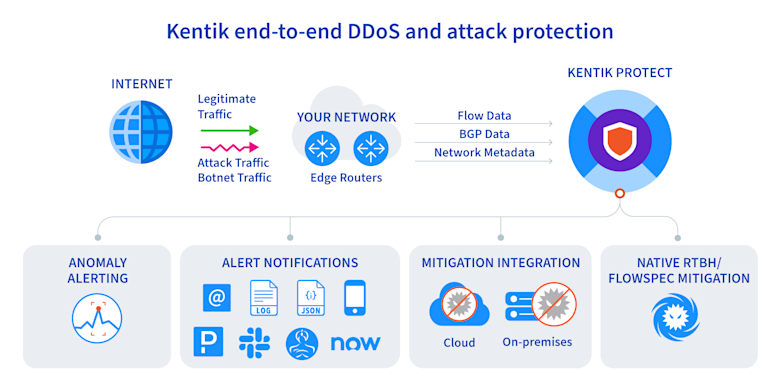
With its early detection, customizable dashboarding, and powerful automation capabilities, Kentik Protect is the most comprehensive tool for securing your networks.



