Summary
IoT represents a massive threat to network infrastructure, as seen in widely publicized IoT-based DDoS attacks like Mirai. So what needs to happen to safeguard our devices and networks from participating in these botnet attacks? And how can IoT device originated attacks get quickly identified and stopped by network operators? In this post, we discuss scalable IoT DDoS protection.

At the end of September 2016, the authors of Mirai released the source code for their botnet. This set the stage for other copycat attacks. Some Mirai botnets grew quite large and were used to launch devastating attacks, including one on October 21st, 2016 that waged an attack against Domain Name Service (DNS) firm Dyn that disrupted Twitter, Netflix, Reddit and a host of other major sites. Another Mirai botnet variant was used in extortion attacks against a number of banks and Internet service providers in the United Kingdom and Germany. Justice was ultimately served with the Mirai co-creators pleading guilty to charges of using their botnet to conduct click fraud—a form of online advertising fraud that cost Internet advertisers more than $16 billion. Based on an annual report from the Spamhaus Project, there has been a 32% increase in botnet controllers in 2017. So what needs to happen to safeguard our devices and networks from participating in these botnet attacks? And how can IoT device originated attacks get quickly identified and stopped by network operators?
Consumer IoT Vulnerabilities Still Widespread Industrial IoT deployments have their vulnerabilities but not to the extent that consumer-driven IoT usage does. In industrial IoT deployments, secure methods and procedures deployed by dedicated network operations staff attempt to ensure that these devices are not compromised. This is not to say that industrial IoT deployments are always secure but consider the typical lack of discipline used to set up consumer IoT devices such as video cameras, thermostats, lighting, switches, smart speakers and TVs in our homes that are potentially vulnerable to compromise and use for DDoS attacks.
I currently have 30 or so IP addresses in my home associated with consumer IoT devices and a Comcast connection that is just over 100 Mbps downstream and 12 Mbps upstream. If I fail to implement my firewall correctly and leave my network open with no password or weak password protection for a bad actor to get into some of my IoT devices, I am vulnerable to unwillingly be part of a botnet based attack. My upstream speed and IoT device count alone may not be high enough to stage a high volume DDoS attack but we have 1,100 doors in my housing development with the potential for the same vulnerabilities in place. With consumer IoT device popularity on the rise and residential broadband providers like Comcast, Charter, AT&T, Google Fiber and others offering 1 Gigabit Internet access to 10s of millions of homes, the next Mirai style attack could be massive in volume. And full duplex DOCSIS 3.1 cable network technology offers the ability to offer 500 Mbps upstream services (on a 1 Gbps service) that in aggregate across millions of homes would dwarf the bandwidth of the original Mirai botnet’s attack.
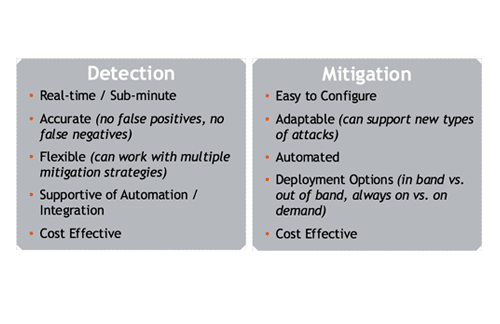
Kentik’s Scalable IoT DDoS Protection Kentik’s adoption of a big data architecture is at the core of their network monitoring and DDoS protection platform, Kentik Detect®. This brings some real advantages for IoT DDoS protection–including detection and mitigation–because big data is not only about handling large volumes of data, but also letting network operations staff make sense of that data very quickly and take action without human intervention if necessary. Key advantages include:
- Threat Feeds – In an integration with one of the industry’s leading independent threat intelligence providers, the Spamhaus Project, Kentik Detect uses comprehensive IP reputation data to tag traffic associated with suspected malicious sources or destinations. Hosts are identified that may be infected with malware, participating in botnets, or engaged in other undesirable activity, and can be flagged for customer notification, clean-up, removal from the network, or other security enforcement.
- Scalable, accurate DDoS protection – A10 Networks and Kentik together provide a highly scalable DDoS protection and analytics solution using Kentik Detect’s real-time, automated triggering of A10 Thunder TPS mitigation, to stop hard to detect multi-vector DDoS attacks. Also, Kentik Detect can use Radware’s DefensePro platform to provide attack mitigation at network throughputs up to 300 Gbps with up to a 230M PPS attack prevention rate. Kentik Detect can also automatically invoke mitigation methods using Radware’s Cloud DDoS Protection Services that support over 2 Tbps of mitigation capacity.
- Full data retention, deep IoT analytics – Kentik’s big data solution doesn’t create summaries or roll-ups and discard network traffic details. Instead, raw data is retained unsummarized, and exploratory analytics enable DDoS traffic patterns to be recognized that might go unnoticed as IoT infrastructure is built out.
- Adaptive baselining and anomaly detection – Big data enables automated tracking of dozens of traffic dimensions to determine which should be baselined and measured for anomalies. This enables far more accurate detection and notification by making the system responsive to the organic changes in IoT network infrastructure and traffic patterns. This makes it easier for IoT-based DDoS threats to be readily detected versus normal traffic.
- Custom Dashboards – Kentik Detect’s Custom Dashboard feature enables users to quickly make sense of the large volumes of data generated by IoT devices. By creating custom panels that visualize the data in the way that makes the most sense to the user, better insight can be gained into IoT network traffic patterns that may represent a security threat.
To see how Kentik can help your organization analyze, monitor, and react to IoT DDoS threats, request a demo or sign up for a free trial today.