What Is Adaptive Flowspec and Does It Solve the DDoS Problem?


Summary
Managing modern networks means taking on the complexity of downtime, config errors, and vulnerabilities that hackers can exploit. Learn how BGP Flow Specification (Flowspec) can help to mitigate DDoS attacks through disseminating traffic flow specification rules throughout a network.
Network administrators need to make sure your users have secure and efficient connectivity to their applications and data. With that in mind, our networks have also become increasingly complex. This is partly due to the pure volume of data needed to run everyday business plus our growing reliance on the public internet. Add in technologies like cloud and SaaS, AI, big data, and the continuous addition of users and devices, and you can see that the subsequent threat landscape is always changing.
It can be incredibly difficult to manage any modern network with this sort of complexity, and that difficulty is compounded when the risk of downtime, configuration errors, security loopholes, and vulnerabilities that hackers can exploit grows with that complexity.
One specific threat to our network security is the distributed denial of service (DDoS) attack. From a high level, a DDoS attack floods a website or a system with fake requests making the system unavailable for legitimate users. There are several different variations of DDoS attacks, but regardless of the form, DDoS attacks are more of an issue today than they’ve ever been because of our reliance on the public internet and internet-based services.
About Kentik: Kentik supports DDoS defense workflows by baselining traffic with high-scale telemetry and surfacing anomalies quickly. Teams can use flow, BGP, and device metrics to classify attacks, understand blast radius, and validate mitigation outcomes, so response decisions are driven by evidence instead of guesswork.
Learn how to protect your network before an attack causes damage to your customers or reputation.

DDoS attacks — they are everywhere
There are several notable examples of DDoS attacks in the news in recent years. For example:
- During the Winter Olympic Games in February 2018, the official website of the Olympic Organizing Committee was forced to shut down due to a DDoS attack.
- GitHub also fell victim to a DDoS attack in March 2018 after experiencing a maximum peak traffic of 1.7 TBPS.
- Amazon Web Services experienced a similar attack in October 2019, with an outage affecting many websites for several hours.
And this is just the tip of the iceberg — many other significant examples have been reported, with the number growing yearly.
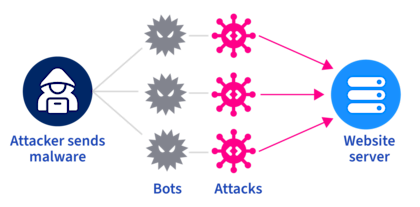
These attacks are often carried out by a network of devices, either computers or IoT devices, which hackers infected with malware. These infected devices, known as bots, form a network called a botnet. In a volumetric type of DDoS attack, these bots, or “zombies,” simultaneously send requests to the target IP address, overwhelming the system and leading to a service degradation or even a shard down scenario.
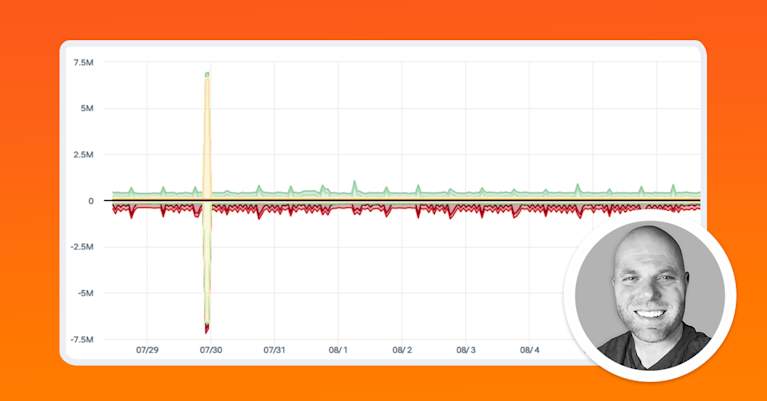
As noted in one research source, there were over 174,000 DDoS attacks just in the USA alone in 2021. These attacks result in downtime, transaction loss, reputational risk, and real dollar impact on your service or product sales.
In other words, the impact of a DDoS is both a financial and business risk.
Overview of Flowspec and Adaptive Flowspec
What is BGP Flowspec?
BGP Flow Specification (Flowspec) is a powerful technology to mitigate DDoS attacks. It’s an extension to the Border Gateway Protocol (BGP) that allows for disseminating traffic flow specification rules throughout a network.
BGP policies using Flowspec help mitigate DDoS attacks by rapidly filtering traffic across an entire network. In light of the ever-growing DDoS attack network administrators have been dealing with as we move to a cloud network model, the IETF RFC5575 proposed Flowspec explicitly as a DDoS mitigation protocol to work on top of BGP.
Using BGP Flowspec, we have granular control to match a particular flow with a source and destination, and also match parameters such as packet packet length, fragment, and so on. With Flowspec, we can dynamically perform three different actions:
- Drop the traffic
- Inject it in a different VRF (virtual routing and forwarding) for analysis
- Allow it, but throttle it at a defined rate
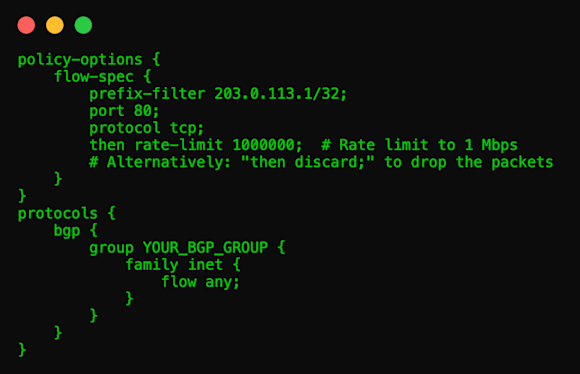
BGP directs a specific flow format to border routers, prompting them to generate access control lists (ACLs) which can be used to manage packet forwarding from external sources. In this way, filtering policies can be pushed to edge devices to mitigate a DDoS attack. As traffic matches a rule pushed by BGP Flowspec, routers take the prescribed action.
Does BGP Flowspec prevent all DDoS attacks?
While BGP Flowspec offers volumetric DDoS attack mitigation, it struggles against some advanced forms attacks. In volumetric DDoS attacks, clients apply Flowspec rules at border routers, then inform the service provider to block specific traffic types targeting the affected IP addresses and ports for filtering.
However, for other types of DDoS attacks, such as amplification DDoS attacks, clients must understand the ISP’s network to effectively mitigate the attack which means much more coordination between the client and the ISP.
What is Adaptive Flowspec?
Adaptive Flowspec improves upon Flowspec by dynamically adjusting or modifying flow specification parameters based on changing network conditions or requirements, or in other words, the “adaptive” part of Adaptive Flowspec. This adaptability allows for more flexible and efficient traffic management in response to varying network conditions, ensuring optimal performance and resource utilization.
The dynamic nature of Adaptive Flowspec is its power, and this ability to update rules based on changing network conditions, or in the case of this discussion, DDoS attack traits, can be completely automated relying on a programmatic workflow and real-time network and traffic analysis.
With traditional Flowspec, a subscriber to a distributed filtering service can request filtering for detected DDoS flows. However, while filtering DDoS traffic based on protocol, TCP flags, and destination is straightforward, source-based filtering is more complex.
Remember the Flowspec policy actions mentioned before:
- Discard all traffic from an IP prefix.
- Discard all traffic from a specific IP.
- Discard traffic from an IP with a particular source port.
Adaptive filtering lets subscribers switch between these granularities as required. This enhances the dynamic nature of responding to what are likely adaptive attacks.
For an IP prefix producing DDoS traffic, if its legitimate traffic is minimal, filtering the entire IP prefix might be suitable, especially during intense attacks. Otherwise, evaluate each subprefix, create rules for subprefixes sending DDoS traffic, ignore those mainly sending legitimate traffic, and recursively apply this strategy to subprefixes with mixed traffic.
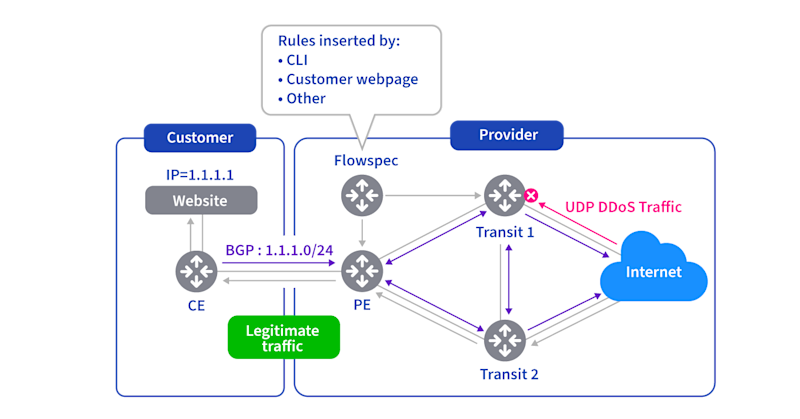
Adaptive Flowspec uses distributed filtering across network nodes. This model works at various scales: internet-wide, within ISPs, or with DDoS-scrubbing services. DDoS traffic filters at different autonomous systems (ASes) across the internet (Figure 1), inside ISP routers or programmable switches (Figure 2), or within DDoS-scrubbing service data centers (Figure 3).
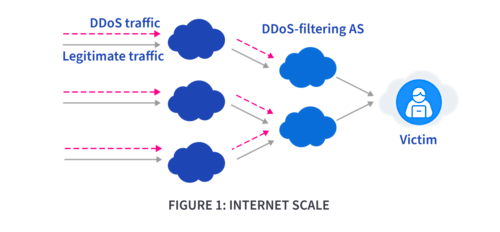
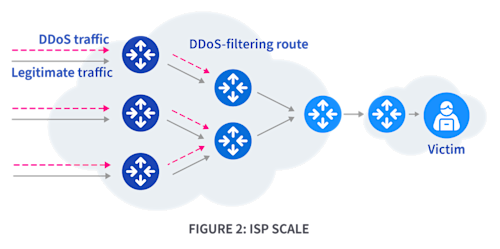
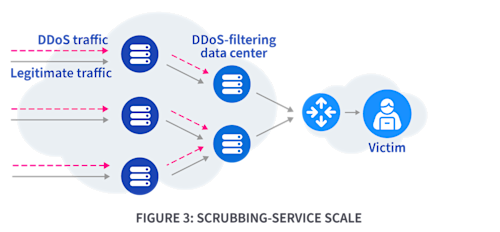
Adaptive Flowspec employs feedback loops to refine its filtering policies. However, one issue that can arise is that while aiming to filter DDoS traffic, it sometimes blocks legitimate traffic. Thus, it uses feedback loops to better distinguish and target only malicious traffic.
Mitigating DDoS attacks using Adaptive Flowspec
Once a DDoS attack is detected, reactive DDoS mitigation strategies are employed. Ultimately, the DDoS attack has already begun, so these strategies are about minimizing the damage caused by the attack. Common mitigations include rate limiting and traffic scrubbing both of which focus on mitigating a DDoS attack in real time.
Adaptive Flowspec adaptively generates rules at a more granular level so the mitigation is more precise with less unintended traffic blocking. It deploys rules at the most appropriate filtering nodes on the path of the actual DDoS traffic, which implies a great deal of network visibility is required to understand where the malicious traffic is flowing.
Because traffic classification can be done on a granular basis, or in other words, flow-by-flow, it’s essential to run adaptive filtering on top of DDoS classification. Network administrators can then fine tune traffic rules based on actual real-time traffic information and threat detection.
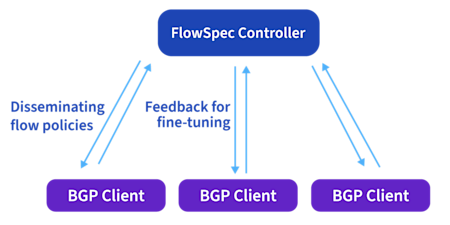
This BGP-based strategy is used because BGP is so customizable and ubiquitous in modern networking. It’s an excellent tool to easily propagate and apply traffic rules in normal operations and in the event of malicious network activity.
Challenges and considerations
Thousands of DDoS flows can stem from only a few IP prefixes, millions from a group of IP addresses, and even more from combined IP and port numbers. Monitoring and determining filtering rules for each very granular scenario can be costly in terms of the time and resources it takes to figure out what’s going on and how to mitigate the attack properly. There’s also the risk of collateral damage if and when good traffic is inadvertently dropped, and managing an inordinate number of classification and mitigation rules.
Nodes on the DDoS traffic path must distinguish and filter DDoS from legitimate traffic to avoid real source traffic loss; however, Adaptive Flowspec addresses these challenges by counter DDoS attacks proactively and dynamically.
Is Adaptive Flowspec the optimal DDoS mitigation tool?
The BGP Flow Specification (Flowspec) and its adaptive counterpart, Adaptive Flowspec, present formidable tools against DDoS threats. Flowspec disseminates traffic rules across a network, providing a method for traffic control, rapid deployment, and dynamic responses to DDoS attack variations.
Meanwhile, Adaptive Flowspec can dynamically recalibrate these rules based on evolving network conditions and attack characteristics, providing a proactive, adaptive mitigation method. And of course, both solutions therefore require deep and broad network visibility to monitor, identify, and filter traffic during an attack.