DDoS Protection and Mitigation: A 2026 Guide to Defending Modern Networks
In the era of ever‑increasing online threats, safeguarding networks and applications from Distributed Denial of Service (DDoS) attacks is a core reliability practice. This article explains how DDoS protection works, outlines today’s attack landscape, and summarizes practical strategies for detection and mitigation. You’ll also find guidance on the four stages of DDoS response and where network intelligence adds the most value.
What is DDoS Protection?
DDoS protection is the set of monitoring, routing, and filtering controls that prevent malicious traffic from overwhelming network or application resources. Effective programs detect anomalies quickly, classify the attack, and apply surgical mitigations—such as BGP FlowSpec, remotely triggered black hole (RTBH) routing, or diversion to scrubbing providers—while preserving legitimate traffic and meeting availability SLOs. As attacks evolve in volume and speed, a robust, automated approach is essential.
Where Kentik fits in a modern DDoS protection stack
Kentik is best thought of as the network security intelligence and decision layer for DDoS. It helps detect attacks early, classify what’s happening with network context, and orchestrate mitigations across your existing controls. For large volumetric attacks, most organizations still rely on dedicated mitigation capacity (scrubbing, anycast edge, cloud protections), while Kentik provides the visibility, correlation, and automation to respond faster and verify results.
What is a DDoS Attack?
A DDoS attack is a coordinated attempt to disrupt a system, service, or network by flooding it with traffic from many sources (for example, botnets or abused reflectors). The goal is to exhaust bandwidth, CPU, memory, or application thread pools so legitimate requests fail. Consequences include degraded user experience, SLA violations, and financial loss.
Understanding the DDoS Threat Landscape in 2026
DDoS attacks continue to be characterized by short, high‑intensity bursts. In Q1 2025, Cloudflare reported blocking 20.5 million DDoS attacks, representing 96% of its total for all of 2024, illustrating both the scale and acceleration of DDoS attacks. In Q2 2025, Cloudflare detailed the largest reported DDoS attack peak to date at 7.3 Tbps, delivering ~37.4 TB of malicious traffic in ~45 seconds—a reminder that seconds‑level response matters.
In terms of the business impact of DDoS attacks:
-
A report from Help Net Security found that the average DDoS attack now lasts 45 minutes—an 18% increase from 2023—and costs unprotected organizations approximately $270,000 per attack at an average rate of $6,000 per minute (roughly $360,000 per hour).
-
Broader cybercrime losses reached $16.6B in 2024, according to the FBI’s IC3 (Internet Crime Complaint Center).
The implications for network operators are clear. Fast detection and mitigation of DDoS attacks—reducing MTTD (mean-time-to-detection) and MTTM (mean-time-to-mitigation)—reduces both outage impact and risk.
Common DDoS Attack Categories Today
1. Volume‑based (L3/L4) DDoS attacks
Volumetric floods strive to saturate links or overwhelm forwarding and CPU resources. They include UDP floods, ICMP floods, and reflection/amplification via DNS, NTP, CLDAP, and Memcached. Modern campaigns often employ carpet bombing—distributing moderate traffic across many IPs or ports to evade per‑destination thresholds while achieving very large aggregate volume. (See: A brief retrospective of network-layer DDoS attacks in 2024)
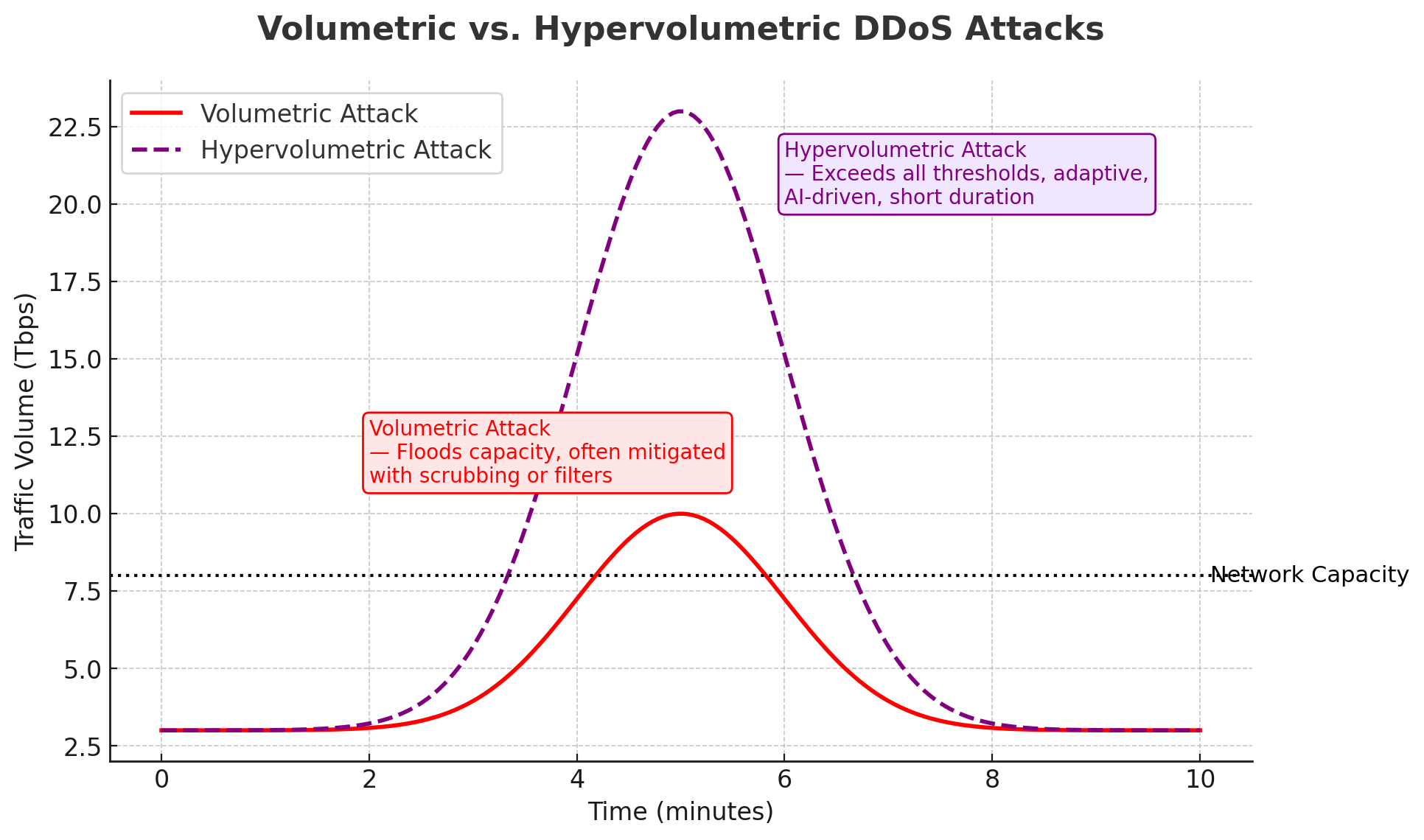
2. Hyper‑volumetric bursts
“Hyper‑volumetric” DDoS events are extremely large, short‑duration floods. Recent examples include Cloudflare’s 7.3 Tbps / 37.4 TB in ~45s incident. Media reports have since noted even higher, sub‑minute peaks (e.g., 11.5–22.2 Tbps) pending full vendor analyses. Responding to these types of attacks demands pre‑approved, automated actions rather than relying on manual tickets.
3. Protocol/state‑exhaustion attacks
These DDoS attacks target network stacks and control planes—using SYN/ACK floods, TCP option abuse, and related techniques—to consume connection tables or CPU without necessarily requiring massive bandwidth.
One notable vector is TCP middlebox reflection, which abuses filtering middleboxes to reflect and amplify TCP traffic to victims. Scanning has identified large numbers of vulnerable devices in the wild. (See: TCP Middlebox Reflection: Coming to a DDoS Near You)
4 Application‑layer (L7) attacks
L7 DDoS campaigns stress request handling rather than raw bandwidth. A prominent example is HTTP/2 Rapid Reset (CVE‑2023‑44487), which drives extremely high requests per second (RPS) by opening and rapidly resetting streams. Recommended measures to protect against L7 DDoS attacks include patching, connection‑level controls, request budgets, and anycast capacity at the edge.
Infrastructure considerations
Even when bandwidth headroom exists, packets‑per‑second (pps) limits, TCAM/ACL capacity, and control‑plane protection determine how routers, firewalls, and load balancers behave under stress. Planning for pps is as important as planning for bps.
AI and the DDoS ecosystem
Threat‑intelligence reporting in 2025 highlights adversaries using AI to scale phishing, write malware, and accelerate campaigns. Research groups have profiled actors such as FunkSec adopting AI‑assisted tooling. While truly “autonomous AI DDoS” may not exist yet, the barrier to entry for would-be malicous actors is lower and iteration is faster than ever before. These conditions are contributing to more frequent—and better‑orchestrated—attacks.
The Danger of Democratized Cyber Attacks
Examples of the ongoing “democratization” of DDoS and other forms of cyber-attacks incude:
- Attackers use AI to generate phishing emails and code for malware (IBM X-Force Threat Intelligence Index 2025).
- Ransomware groups like are applying AI to automate combined DDoS attacks plus extortion campaigns. (As just one example, Check Point Research, reported on the AI-powered FunkSec ransomware group.)
- AI-powered DDoS kits are being sold on cybercrime marketplaces, reducing the technical barrier for attackers. (IBM X-Force Threat Intelligence Index 2025)
- The FBI IC3 (Internet Crime Complaint Center) reported over $16.6 billion in cybercrime losses in 2024, with DDoS and ransomware among the most disruptive threats. (Federal Bureau of Investigation, IC3 Internet Crime Report 2024, p. 4–5)
- The IC3 report explains that AI is enabling adversaries to rapidly scale campaigns that previously required specialization.
Kentik in brief: Kentik is the network intelligence platform for modern infrastructure teams, providing unified visibility across data center, cloud, WAN, and the public internet. Kentik collects telemetry like flow data, internet routing, performance tests, and network metrics to help teams troubleshoot, optimize performance, control cost, and strengthen security.
Learn how to protect your network before an attack causes damage to your customers or reputation.

The Components of a Comprehensive DDoS Protection Strategy
Traffic monitoring and analysis
Continuous visibility across flow, SNMP, BGP, and synthetic tests helps teams establish baselines, spot anomalies, and correlate routing changes with traffic spikes. Effective systems distinguish between legitimate surges (e.g., promotions, deploys) and attack traffic by combining rate, entropy, and distribution signals.
Network filtering and rate limiting
Mitigation aims to be precise aiming to drop attack attributes while keeping good traffic moving. Examples include:
- BGP FlowSpec to propagate match/action filters in seconds (e.g., dst IP/port/protocol, packet length).
- RTBH (remotely triggered black hole): destination‑ or source‑based null routing under severe saturation.
- Targeted rate limits or geo/ASN constraints when appropriate.
Application‑level protection
At L7, WAF/CDN/edge controls help absorb or filter request floods (e.g., Rapid Reset variants) while upstream network mitigations handle volumetric components.
On‑premises and cloud‑based mitigation
Most DDoS protection programs use hybrid patterns:
- On‑premises FlowSpec/ACLs for fast, surgical blocks close to the network edge
- BGP diversion to scrubbing for very large mixed‑vector attacks
- Anycast WAF/CDN for application‑layer stress
Incident response planning
Define roles, thresholds, and pre‑approved actions ahead of time. For example, who can push FlowSpec or RTBH, when to divert to a scrubbing provider, how to open ISP tickets, and how to notify customers. Keep a short “during‑attack” communication template so actions happen in seconds, not minutes.
Tools for DDoS Protection and Mitigation (2026)
DDoS protection programs are usually built from multiple components: (1) visibility and decision layers that correlate telemetry and speed triage, (2) scrubbing/edge mitigation services that absorb or filter large attacks, and (3) cloud-native protections for workloads hosted in public clouds.
A practical shortlist includes:
-
Kentik Protect (visibility + orchestration): Kentik Protect unifies telemetry (flow, BGP, device metrics, synthetics) to detect and classify attacks and can automate mitigations like FlowSpec/RTBH while orchestrating with external mitigation partners.
-
Cloudflare DDoS Protection (edge mitigation): Cloudflare provides DDoS mitigation across layers 3, 4, and 7 using a global network that blocks attack traffic close to the source.
-
Akamai Prolexic (scrubbing service): Prolexic is a managed DDoS scrubbing platform designed to protect data center, cloud, and hybrid environments with always-on or routed options.
-
AWS Shield (cloud-native protection for AWS): AWS Shield is a managed DDoS protection service for applications running on AWS with Standard and Advanced tiers.
-
Azure DDoS Protection (cloud-native protection for Azure): Azure DDoS Protection provides monitoring and automatic mitigation for DDoS attacks targeting Azure resources.
-
Google Cloud Armor (cloud-native protection + WAF): Cloud Armor provides DDoS protection and WAF capabilities for Google Cloud workloads, including protections at Google scale.
-
NETSCOUT Arbor (Sightline/TMS/Cloud) (detection + mitigation ecosystem): Arbor provides DDoS detection and defense capabilities (including detection solutions like Sightline and mitigation options in the Arbor ecosystem).
The Four Stages of DDoS Mitigation
1. Detection
The detection stage involves continuously monitoring and analyzing network traffic to identify potential DDoS attacks. Monitor pps/bps and distribution shifts, BGP route changes, and RPS for L7 events. By observing traffic patterns and using flow analysis and anomaly detection techniques, organizations can quickly detect abnormal traffic patterns that may signify an ongoing DDoS attack. Early detection is crucial for initiating a timely response to minimize the impact on critical infrastructure. (Learn more about DDoS Detection)
2. Response
Once an attack has been detected, the response stage entails implementing appropriate countermeasures to mitigate the attack’s impact. Trigger the pre‑approved playbook. Typical steps include opening an incident, attaching traffic snapshots, pushing an initial FlowSpec rule set. If saturation persists, activate RTBH or scrubbing as appropriate. Automation shortens time‑to‑mitigation and reduces error.
3. Filtering
Filtering is the process of distinguishing and separating the attack traffic from legitimate traffic, ensuring that only genuine user requests reach the targeted systems. Techniques employed in filtering may involve rate limiting, IP blocking, or implementing network filtering rules. Filtering helps maintain the integrity of the network while mitigating the effects of the DDoS attack.
Iterate toward surgical rules: Match attack protocol/port/size, constrain by ASN or geography if applicable, and avoid prefix‑wide blackholes unless capacity is at risk. Verify that good traffic continues to flow.
4. Analysis
After the attack has been mitigated, the analysis phase involves examining the incident’s details to understand the attack’s origin, nature, and impact on the network. By collecting and analyzing data related to the attack, organizations can identify areas for improvement in their DDoS protection strategy and make necessary adjustments to prevent similar attacks in the future. This stage is essential for refining and optimizing an organization’s DDoS defense capabilities.
After the event, catalog vectors, top sources/ASNs, rules that worked, residual false positives/negatives, and headroom. Feed lessons learned into thresholds, allowlists, and runbooks. For Rapid Reset and related variants, confirm patch posture.
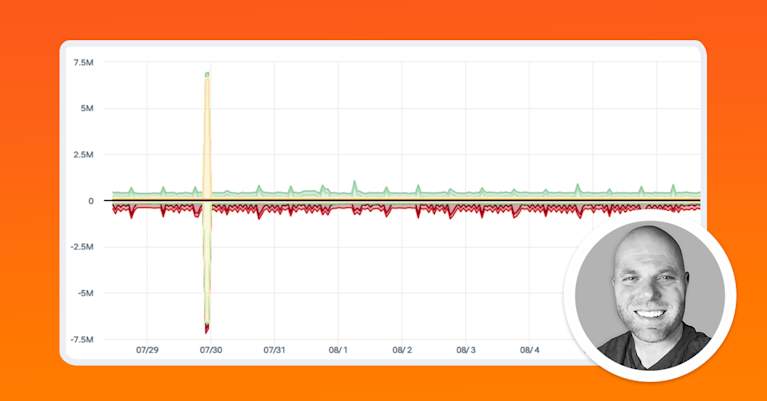
In this video, Doug Madory, Kentik director of internet analysis, and Phil Gervasi, director of tech evangelism, discuss the nuance of coordinating the mitigation of a DDoS attack and how we can use Kentik to see the propagation of BGP announcements on the public internet before, during, and after the DDoS attack mitigation:
Additional DDoS Protection Techniques & Best Practices
In addition to the methods discussed earlier, several other techniques can be employed to enhance your protection against DDoS attacks. By incorporating these additional measures into your DDoS protection plan, you can further strengthen your infrastructure’s resilience against potential attacks and maintain the availability of your services.
- Minimize attack surface: Hide origin services behind anycast edges; use split‑horizon DNS and egress ACLs.
- Plan for packets: Budget router pps and TCAM/ACL capacity. Don’t rely only on bandwidth.
- Harden DNS: Implement DNSSEC where appropriate, limit recursion, and monitor resolver abuse.
- Use threat intelligence feeds: Enrich flows with IP reputation data to spot botnets and C2s early—for example, Spamhaus datasets integrated into network observability workflows.
The Role of Network Intelligence in DDoS Protection
Network intelligence correlates traffic, routing, and device signals so teams can see the attack, classify it accurately, mitigate with confidence, and verify results. In practice, this reduces MTTD/MTTM, lowers false positives, and produces better post‑incident reporting for leadership.
How Kentik Can Help with DDoS Protection and Mitigation
Kentik Protect combines big‑data network observability with automated, surgical mitigation of DDoS attacks with:
- Unified telemetry: Integrated network flow, BGP, SNMP, and synthetics for real‑time detection and triage.
- Automated mitigations in seconds: Adaptive FlowSpec, RTBH, and orchestration with third‑party scrubbing/mitigation partners. (Learn more in the Kentik Knowledgebase)
- Threat‑feed enrichment: Flow records can be enriched with Spamhaus IP reputation to identify botnet C2s, malware distribution points, phishing sites, and more.
- Outcome focus: Customers commonly report MTTR reductions of up to 50% and transit/egress savings of 10–30% when pairing observability with automated mitigation.
Customer Success Stories in DDoS Protection
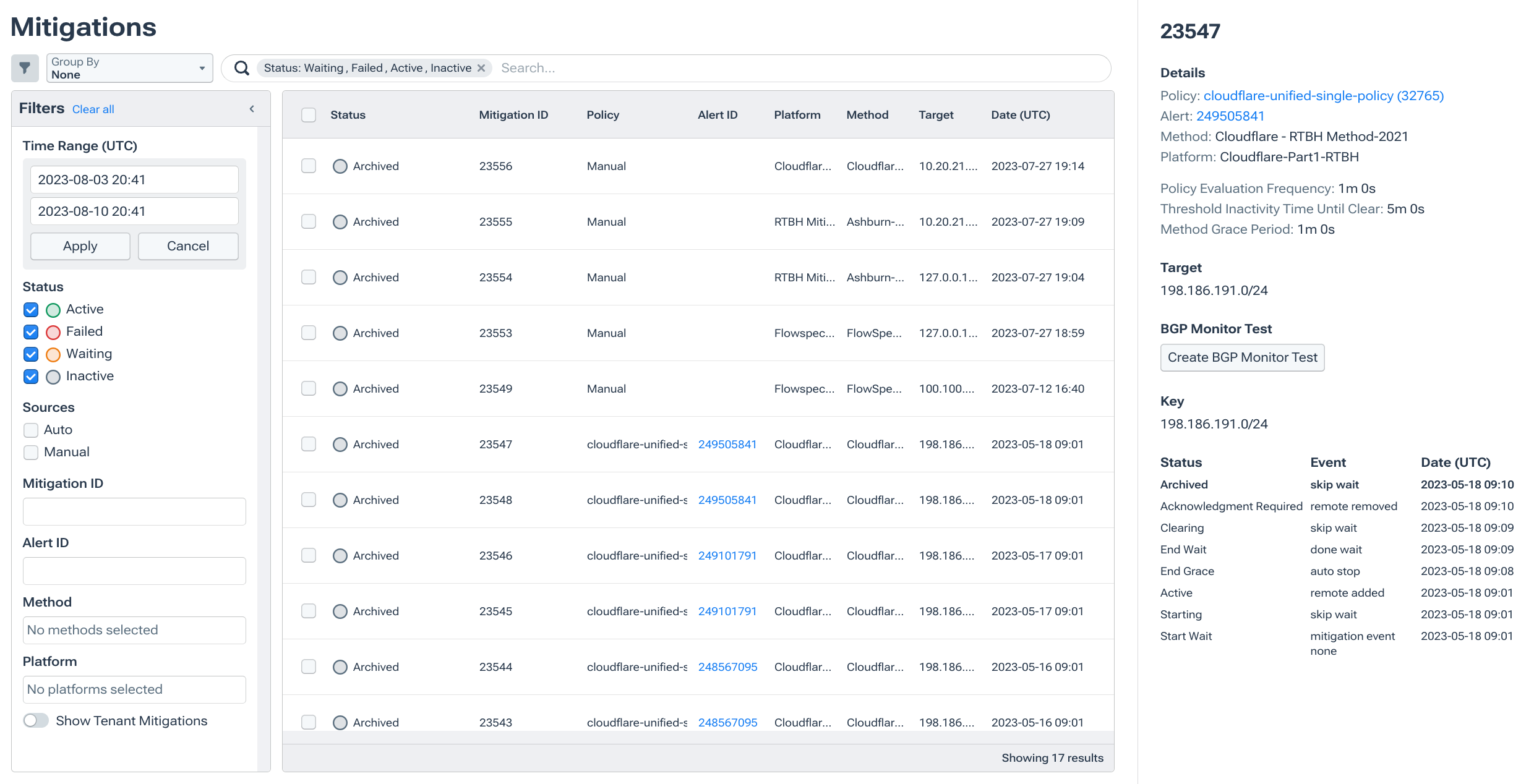
- Immedion (regional cloud/DC): Using automated detection and RTBH, Immedion handled 30��–40 Gbps attacks and saved 8–10 hours of weekly ops effort. (Case Study: Immedion)
- GoDaddy (global ISP): Standardizing on Kentik, time‑to‑insight moved from minutes to seconds and the enterprise consolidated legacy tools. (Case Study: GoDaddy)
- Square Enix (gaming): Uses Kentik Protect for real‑time detection and faster resolution across backbone and cloud networks. (Case Study: Square Enix)
Get Started with Kentik
Ready to improve your DDoS posture?
To learn more about how network intelligence and observability can improve your organization’s DDoS protection, check out the blog post “8 reasons why network observability is critical for DDoS detection and mitigation”, watch the Superloop video, and read our guide, “The NetOps guide to network security”.
Ready to get started with superior cloud-based DDoS protection? Start a free trial of Kentik or request a demo of our DDoS Protection solution.
Glossary of DDoS Mitigation Terms
- BGP FlowSpec: Extension to BGP for distributing granular match/action filters (e.g., dst IP/port/proto, size) to routers for rapid, precise mitigation. (See also: BGP Flowspec Doesn’t Suck. We’re Just Using it Wrong)
- RTBH (Remotely Triggered Black Hole): Routing technique that discards traffic for a destination or from a source by advertising a route to a null interface; useful under severe saturation. (See also: Automate RTBH DDoS Proection in Under an Hour)
- Carpet bombing: Distributing attack traffic across many IPs or ports to evade per‑target thresholds while achieving large aggregate volume. (See also: A brief retrospective of network-layer DDoS attacks in 2024)
- HTTP/2 Rapid Reset (CVE‑2023‑44487): L7 technique using rapid stream resets to drive extreme RPS. Mitigations include patching and connection/request controls. (See also: CISA Alert: HTTP/2 Rapid Reset Vulnerability)
FAQs about DDoS Protection and DDoS Mitigation
How can I detect and mitigate volumetric DDoS without false positives?
Kentik leverages big-data flow telemetry, BGP, and interface metrics — combined with machine-learning-driven traffic profiling — to distinguish DDoS attack traffic from legitimate traffic, avoiding false positives. When volumetric DDoS is detected, Kentik can trigger automated mitigation (via RTBH, FlowSpec, upstream scrubbing), helping to prevent or mitigate the attack before it impacts users.
What telemetry should a DDoS protection program monitor continuously?
Continuous visibility across flow, SNMP, BGP, and synthetic tests helps establish baselines, spot anomalies, and correlate routing changes with traffic spikes. Effective programs distinguish DDoS attacks from legitimate surges by combining rate, entropy, and distribution signals.
What are the key components of a comprehensive DDoS protection strategy?
A complete strategy typically includes: traffic monitoring/analysis, network filtering/rate limiting, application-layer protection, on-prem and cloud mitigation, and incident response planning.
What is BGP FlowSpec and when is it useful?
FlowSpec propagates match/action filters in seconds (for example by destination IP, port, protocol, or packet length) to enable rapid, precise DDoS mitigation close to the network edge.
What is RTBH and when should it be used?
RTBH (remotely triggered black hole) null-routes traffic for a destination or source and is typically used under severe saturation when you need immediate relief for a DDoS attack.
When should network traffic be diverted to a scrubbing provider?
Many DDoS mitigation programs use hybrid patterns: apply on-prem FlowSpec/ACLs for fast, surgical blocks, and divert traffic to scrubbing providers for very large mixed-vector attacks, while anycast WAF/CDN controls handle application-layer floods.
What are the four stages of DDoS mitigation?
A practical DDoS mitigation lifecycle includes: Detection, Response, Filtering, and Analysis. Detection monitors pps/bps and distribution shifts (plus BGP changes and L7 RPS). Response executes a pre-approved playbook. Filtering separates attack traffic from legitimate traffic. Analysis reviews the incident to improve future defense.
How do you filter DDoS attack traffic without causing collateral damage?
Iterate toward surgical rules: match protocol/port/size, constrain by ASN/geo when appropriate, avoid prefix-wide blackholes unless capacity is at risk, and verify that good traffic continues to flow.
How do I detect and mitigate DDoS attacks across on-prem and cloud environments?
Use a hybrid DDoS workflow with three layers: (1) detection + decision, (2) on-network filtering, and (3) upstream/edge scrubbing + cloud-native protections. With Kentik Protect / DDoS Defense, you can baseline and detect attacks early using unified telemetry (flow, BGP, device/interface metrics, and more), then classify the attack using built-in visualizations and ML-based traffic profiling. For mitigation, Kentik can trigger BGP FlowSpec or RTBH, and it can also orchestrate third-party mitigation services like Cloudflare Magic Transit when you need large-scale scrubbing or edge capacity. After mitigations fire, use Kentik to verify that attack traffic drops and legitimate traffic recovers, and to capture evidence for post-incident tuning of alert policies and playbooks.
Learn more: Detect and Mitigate DDoS (Kentik Solutions), Mitigations Overview (KB), Kentik + Cloudflare Magic Transit
What should be in a DDoS incident response plan?
Define roles, thresholds, and pre-approved actions in advance (who can push FlowSpec/RTBH, when to divert to scrubbing, how to open ISP tickets, and how to notify customers). Keep a short “during-attack” communication template so actions happen in seconds, not minutes.
What best practices strengthen DDoS resilience?
Common practices include minimizing attack surface (hide origins behind anycast edges), planning for packet rates and ACL capacity, hardening DNS, and using threat intelligence feeds to enrich flow records.
How does network intelligence improve DDoS protection outcomes?
Correlating traffic, routing, and device signals helps teams classify attacks accurately, mitigate with confidence, verify results, reduce MTTD/MTTM, lower false positives, and improve post-incident reporting.
How can Kentik help with DDoS protection and mitigation?
Kentik Protect combines unified telemetry (flow, BGP, SNMP, synthetics), automated mitigations (FlowSpec/RTBH and orchestration with third-party mitigation/scrubbing partners), and threat-feed enrichment (e.g., Spamhaus IP reputation) for faster detection, triage, and response.
How do I detect and mitigate reflection and amplification attacks?
Detect reflection/amplification attacks by alerting on sudden, protocol-specific volumetric spikes and confirming characteristics like many sources and UDP service abuse. Kentik’s DDoS Defense workflow includes preset DDoS policies and ML-based profiling to speed detection, plus automated and manual mitigations such as RTBH and BGP FlowSpec and integrations with external mitigation services.
What’s the best way to validate that DDoS mitigation is working in real time?
Validate mitigation by confirming that attack traffic rates drop while legitimate traffic and reachability remain stable, and by watching whether congestion symptoms (loss, latency, saturation) improve immediately after mitigation actions. Kentik supports this by using flow-based visibility to track traffic shifts during mitigation and help teams verify that the response reduced impact without blocking good users. See also: DDoS Detection, Detect and Mitigate DDoS “Learn more about Kentik solutions to detect and mitigate DDoS attacks.”).