Network Device Monitoring: Analyzing the Status, Health, and Performance of Network Devices
Network device monitoring is a crucial aspect of network management, ensuring optimal performance, availability, and security of various network devices such as routers, switches, firewalls, and servers. This article explores the intricacies of network device monitoring, discussing its importance, key performance metrics, diverse monitoring techniques, and best practices. We also compare network device monitoring (sometimes known as network status monitoring) to network performance monitoring (NPM).
What is Network Device Monitoring?
Network device monitoring is the process of continuously observing and analyzing the performance and status of network devices. This practice helps proactively identify potential issues, ensure optimal performance, and maintain a network’s overall health. The term “network device monitoring” often encompasses tracking key metrics and performance data related to device health, such as up/down status, availability, CPU utilization, memory usage, and disk space.
Network device monitoring can be carried out in several ways, each with unique advantages and use cases:
Active Monitoring
This approach periodically sends requests or pings to network devices to gauge their status and response time. Active monitoring can provide real-time or near-real-time data, making it helpful in identifying current network issues. However, it can also generate additional network traffic, which needs to be managed effectively.
Passive Monitoring
Passive monitoring involves analyzing network traffic that flows through the network devices. This approach can provide insights into network usage patterns, trends, and potential performance issues. However, it may not detect problems with devices that are currently not transmitting data.
Predictive Monitoring
Leveraging historical data and machine learning algorithms, predictive monitoring attempts to forecast potential issues before they occur. This proactive approach can help network administrators address problems before they affect network performance or lead to network downtime. However, it requires a significant amount of data and advanced analytics capabilities.
By combining these methods, network administrators can comprehensively understand their network’s health and performance. Regular monitoring helps to quickly identify and rectify issues, optimize resource usage, and plan for future capacity needs. As network technologies have evolved, monitoring tools and strategies have become more advanced, offering capabilities such as automated alerts, trend analysis, and integration with other network management systems.
Kentik in brief: Kentik helps teams modernize network device monitoring with a next-generation NMS that unifies SNMP polling, streaming telemetry, and custom metrics in one workflow. Kentik collects device health metrics like status, CPU, memory, interfaces, and errors at high resolution, then lets engineers explore and troubleshoot device issues using fast queries and natural-language assistance. With Kentik AI Advisor, teams can launch evidence-backed, multi-step investigations from alerts and standardize responses with runbooks and custom network context (see AI Advisor docs and Kentik AI settings).
Learn how AI-powered insights help you predict issues, optimize performance, reduce costs, and enhance security.

Why is Network Device Monitoring Important?
Network device monitoring is important because it ensures network devices’ optimal performance, availability, and security, which is vital for running network-based applications and services smoothly. In today’s environment, with cell phones always connected, cars connected, vending machines connected, and continuous inventory updates, we rarely run into people or devices that are not “connected” to the network.
Network device monitoring plays a crucial role in proactively identifying and resolving issues as they arise (network issues are a matter of “when,” not “if”), facilitating efficient management of network resources, and enhancing overall network security.
Network device monitoring equips administrators with detailed insights into the performance of individual devices throughout the entire network topology. As a result, administrators can promptly identify and mitigate irregularities by continuously tracking key device health metrics. This proactive approach prevents minor issues from escalating into significant network disruptions, thereby maintaining service quality and availability. Moreover, administrators can optimize resource allocation, improve network efficiency, and reduce operational costs by monitoring network traffic patterns and device usage.
Key Metrics in Network Device Monitoring
Key metrics, often called device health metrics, play a crucial role in network device monitoring. Some of these important performance metrics include:
- Device availability: Measures the status of a network device (online or offline, “up/down status”).
- CPU utilization: Monitors the percentage of CPU capacity that a device is currently using.
- Memory usage: Determines the amount of memory consumed by a device.
- Disk space: Evaluates the storage capacity used and available on a device.
- Device errors: Tracks the number and types of errors a device encounters.
- Uptime: Monitors the total time a device has been operational without interruption.
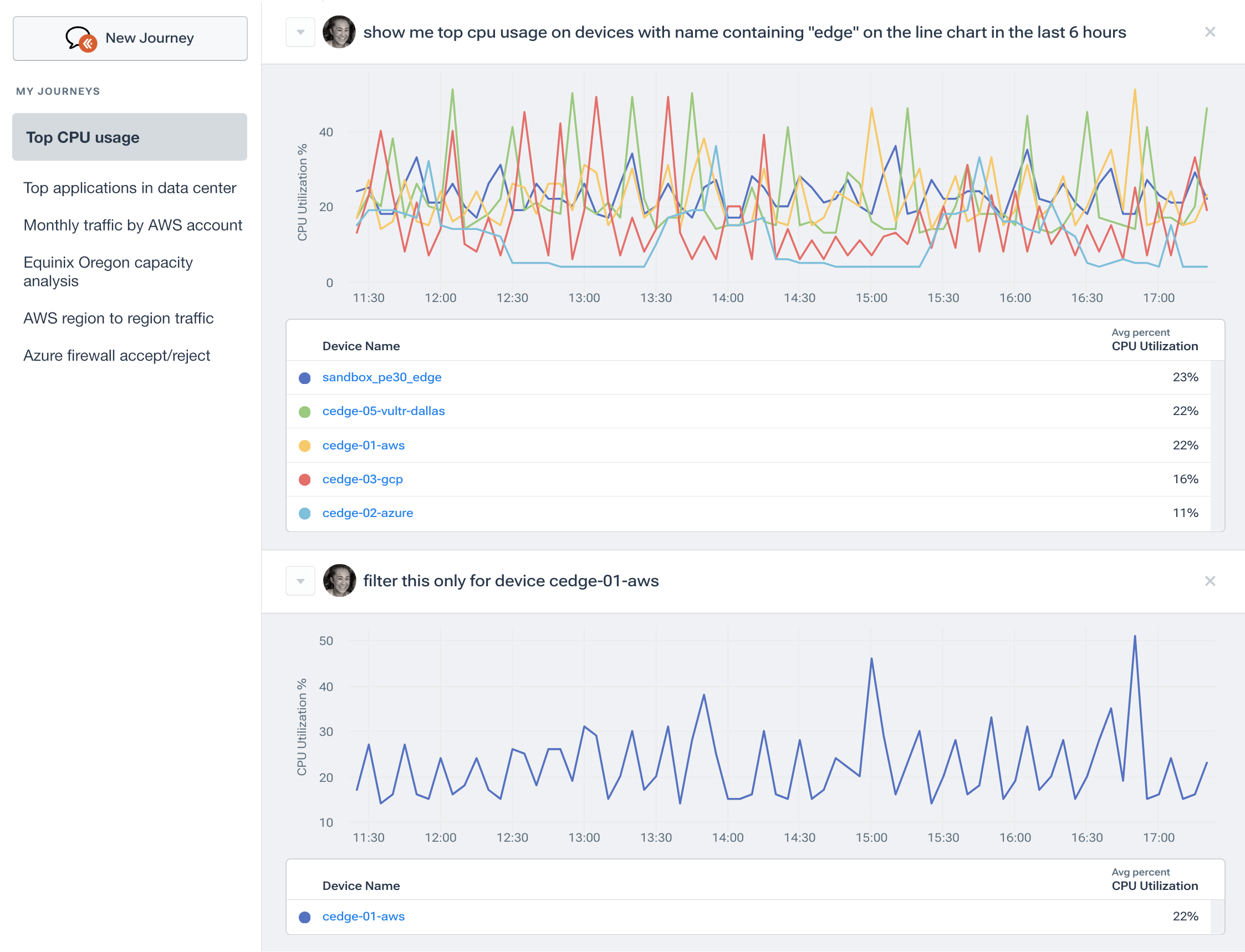
Network Device Monitoring Tools
Network device monitoring tools are software applications or SaaS platforms that continuously monitor network device performance. These tools collect data from various devices, analyze it to detect issues as they arise, and provide alerts to network administrators (including cloud administrators, site reliability engineers (SREs), NetOps, and DevOps teams).
Selecting the right network device monitoring tool depends on factors such as the size of your network, the types of devices you need to monitor, the complexity of your network infrastructure, and your specific monitoring needs.
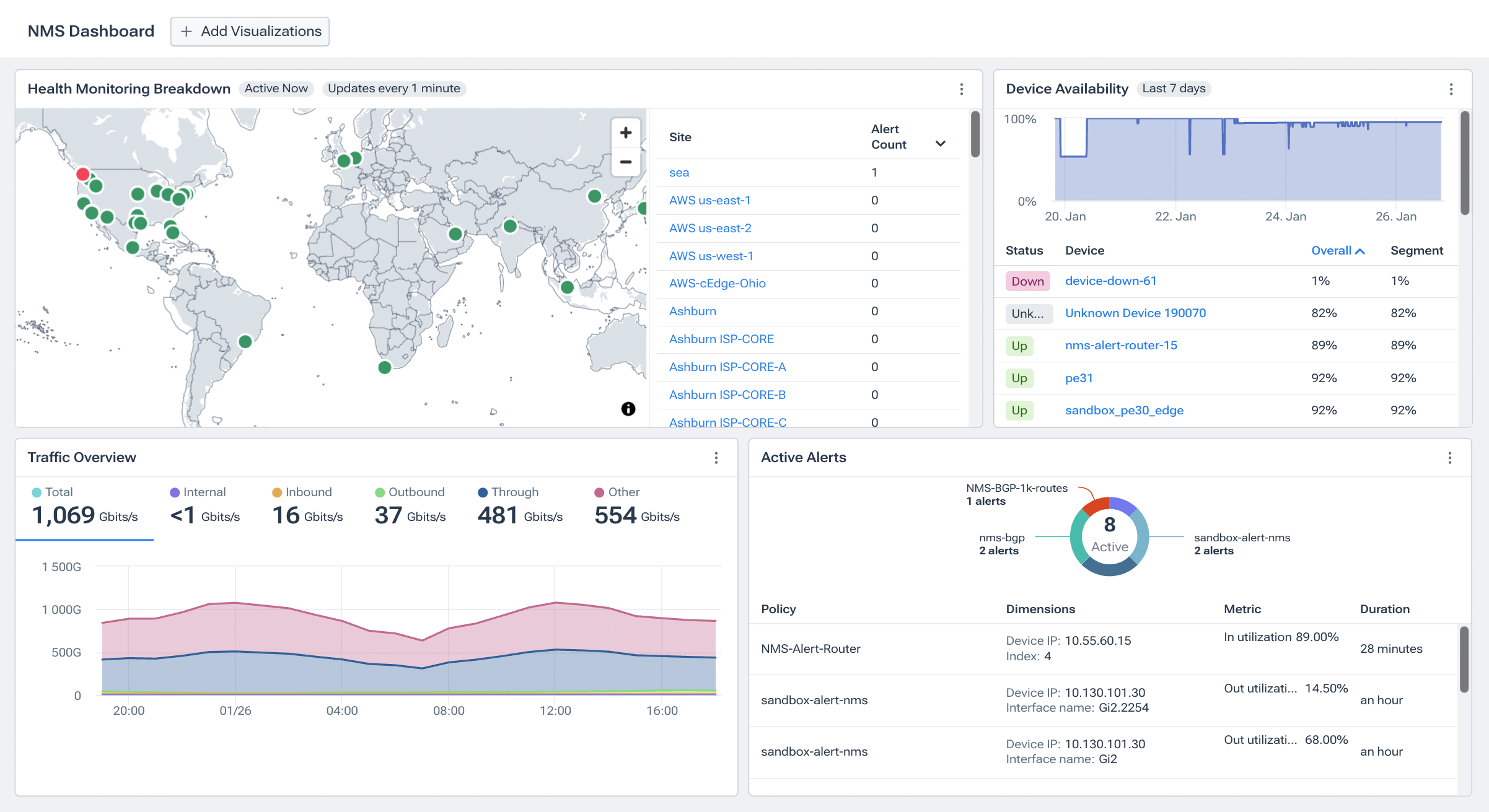
Types of Devices Monitored by Network Device Monitoring Tools
Network device monitoring tools can be used to manage a wide range of devices. Whether the devices are physical or virtual, on-premise or in the cloud, monitoring tools provide crucial insights into their performance and status. Examples of network devices that are commonly monitored include:
- Routers: Forward data packets between computer networks. Monitoring routers can help detect packet loss, latency, or unusually high traffic.
- Switches: Channel incoming data from multiple input ports to the output port that takes data toward its destination. Monitoring switches can help ensure efficient data routing and identify bottlenecks.
- Firewalls: Control network traffic based on security rules. Monitoring firewalls can help ensure policies are enforced and highlight unusual activity.
- Servers: Provide services across a network (physical or virtual). Server monitoring supports availability and performance for critical applications.
- Wireless devices: Wireless routers, access points, and connectivity devices. Monitoring helps maintain wireless quality and identify RF (radio frequency) issues.
- Virtual Machines (VMs): Software emulations of physical computers. Monitoring is critical for virtualized environments.
- Cloud devices: VPNs, VPCs/VNets, transit gateways, cloud firewalls, and load balancers. Cloud device monitoring provides visibility into health and performance in cloud-based environments.
- Containers: Execution packages for cloud-native applications. Monitoring supports performance and availability of containerized apps.
- IoT devices: Connected sensors and devices that exchange data over networks. Monitoring supports reliability and security for these endpoints.
Each type of network device can present unique monitoring challenges, but with the right tools, administrators can maintain comprehensive visibility into performance and status. Monitoring a combination of these devices, especially in hybrid environments that mix on-premise and cloud-based devices, is essential for maintaining a healthy and efficient network.
Kentik’s network device monitoring tool (Kentik NMS) supports many types of network devices via SNMP or streaming network telemetry (where supported). Kentik also provides powerful hybrid and multi-cloud monitoring and visibility capabilities for cloud and container-based network devices.
Network Device Monitoring Techniques and Protocols
There are several techniques and protocols employed in network device monitoring, each providing a different perspective on the status and health of network devices.
Simple Network Management Protocol (SNMP)
SNMP is an IETF standard protocol for collecting and organizing information about managed devices on IP networks. SNMP operates in a client-server model where network devices act as servers, and the monitoring system acts as a client. SNMP collects information related to device status, configuration, and performance, which is then stored in a management information base (MIB) and can be queried by network administrators.
Implemented nearly universally in every network-connected device, SNMP can be used to track a wide variety of health and performance metrics beyond whether the device is available (its “up/down status”), including:
- Core network device metrics: Metrics such as CPU utilization, memory utilization, disk or other storage usage, bandwidth utilization, and uptime.
- Network error metrics: Metrics indicating potential issues, including dropped packets and packet loss rate.
- Hardware device-specific metrics: Metrics reflecting physical aspects of network hardware, including temperature and fan speeds.
- Non-routable interface status: Monitoring management interfaces that don’t route production traffic but are critical for operations and administrative access.
Streaming Telemetry
Streaming telemetry is often considered the next evolutionary step from SNMP in device monitoring data collection. It differs from SNMP in how it works, if not in the information it provides. Streaming telemetry solves some of the problems inherent in polling-based SNMP, especially when teams need higher-resolution signals.
The various forms of streaming telemetry, such as gNMI, structured data approaches (like YANG), and other proprietary methods, offer near-real-time data about device status. Instead of waiting minutes for subsequent polling, teams can observe device behavior continuously.
Because data is pushed from devices rather than polled at prescribed intervals, streaming telemetry can provide far higher-resolution data compared to SNMP. This push-based model is generally more efficient, and telemetry processing can happen in hardware at the ASIC itself instead of on the device’s CPU. As a result, it can scale in larger networks without affecting device performance. (See our blog post for a deeper look at streaming telemetry vs SNMP.)
Syslog and Log Files
These files contain messages about the device’s activities, including operational status, error messages, and other event data. Syslog is a standard protocol for sending log messages from devices to a central log server. Logs are crucial for troubleshooting, monitoring device performance, and maintaining security. They can also provide valuable insights during forensic investigations.
NetFlow Monitoring
NetFlow is a protocol developed by Cisco for collecting IP traffic information and monitoring network traffic flow. NetFlow captures metadata about network packets (such as source IP, destination IP, ports, and protocol) and aggregates it into flows, providing visibility into traffic patterns and trends.
Numerous variations on NetFlow from different vendors, such as sFlow (from InMon) and J-Flow (from Juniper Networks), offer similar functionality.
Cloud-based Device Monitoring
This refers to monitoring techniques designed for cloud devices (e.g., VPNs, VPCs, transit gateways, cloud firewalls, load balancers) hosted in cloud environments. Given the distributed and dynamic nature of the cloud, traditional monitoring solutions may not always suffice.
Cloud devices often support NetFlow-like telemetry in the form of VPC Flow Logs, providing visibility into IP traffic going to and from network interfaces in a Virtual Private Cloud (VPC).

Service Mesh
Originally developed by Lyft as Envoy, Istio is a framework for network traffic management. Istio is an extension of Envoy that adds policy enforcement and telemetry collection. While not a monitoring protocol per se, Istio offers key functionalities that aid in monitoring applications deployed in distributed microservices architectures. It provides detailed insights into service behavior, enabling efficient troubleshooting, performance tuning, and security monitoring.
Each of these protocols and techniques offers different capabilities, and the choice depends on specific requirements. In practice, teams combine multiple telemetry types to achieve comprehensive device monitoring.
Predictive and Proactive Device Monitoring with Streaming Telemetry + AI
SNMP remains the baseline for device monitoring, but many modern teams need to know what happened in the last 30 seconds, not just the last 5 minutes. This is where streaming telemetry and AI-driven workflows complement traditional polling.
Why streaming telemetry makes predictive monitoring more practical
Predictive monitoring depends on two things: (1) high-quality historical data and (2) enough time resolution to capture short-lived events. Streaming telemetry provides a stronger foundation for predictive monitoring because it captures more granular device behavior in near real time.
Kentik NMS supports both SNMP and streaming telemetry and normalizes data into a consistent schema so dashboards and workflows remain consistent regardless of collection method (see NMS Setup docs). In Kentik, enabling streaming telemetry changes collection behavior in meaningful ways. For example, SNMP polling for CPU, memory, and interface statistics can be replaced by telemetry collection, with a default telemetry interval of 30 seconds, and CPU collected every 2 seconds (details: NMS Setup: Adding Streaming Telemetry).
Where AI helps in network device monitoring
Higher-resolution telemetry improves detection, but it can also increase noise. AI helps most when it reduces toil:
- Faster investigation: Kentik AI Advisor can interpret natural language prompts and execute multi-step investigations across device metrics, traffic flow data, syslog, traps, and synthetic tests (see AI Advisor docs).
- Instant “what changed?” triage: Kentik’s Cause Analysis reduces manual traffic slicing by automatically detecting changes and producing a hierarchical breakdown of the dimensions driving a spike or drop (see also Cause Analysis in the KB).
In practice: streaming telemetry helps you detect sooner, and Kentik AI helps you understand faster.
Benefits of Network Device Monitoring
Network device monitoring offers several benefits:
- Proactive problem solving: Administrators can detect potential issues early and address them before they escalate by continuously monitoring device performance.
- Better management and control: Monitoring provides insights into device performance and usage, enabling better resource management and control.
- Improved network efficiency: Monitoring can help improve efficiency by identifying bottlenecks and other issues.
- Enhanced security: Monitoring can help detect unusual activity that could indicate a security breach.
Setting Up Network Device Monitoring
Setting up effective network device monitoring is fundamental to adopting a proactive and responsive approach to network management. Initial steps and considerations include:
Defining Monitoring Objectives and Metrics
Identifying the right key performance indicators (KPIs) is crucial for targeted monitoring. By defining these KPIs, administrators can establish meaningful thresholds and set up alerts for critical events, ensuring prompt detection and response to potential issues. (For a deeper dive on best practices around alert strategy, see Network Monitoring Alerts.)
Monitoring Device Health and Configuration
For effective monitoring, it’s vital to configure devices for protocols like SNMP, streaming telemetry, or flow data collection. Routinely updating device firmware and software helps ensure monitoring tools can access accurate device metrics without compatibility issues.
Data Visualization and Reporting
Visualizing monitoring data through dashboards and graphs can give a clearer view of performance and trends. Periodic reports generated from this data further facilitate analysis. Ongoing visualization and reporting helps administrators make informed decisions and optimize network health.
Runbook-Driven Device Alert Response with Kentik AI Advisor
Collecting metrics is only half the battle. To reduce downtime and alert fatigue, teams need a reliable, repeatable process for responding when device alerts fire.
Kentik supports a “runbook-driven” approach using Runbooks + Custom Network Context + AI Advisor, enabled under Kentik AI and configured in Kentik AI settings.
Runbooks: codify how investigations should run
In Kentik, Runbooks are predefined, Markdown-formatted recipes that guide AI Advisor through diagnostic steps for specific alerts. Runbooks can:
- be assigned to one or more alert policies,
- start the investigation from an alert with relevant context already in place,
- minimize human (and AI) error by enforcing a systematic troubleshooting approach (details: Kentik AI settings: Runbooks).
Custom Network Context: teach the AI your environment
Kentik AI also supports Custom Network Context: up to 100K characters of Markdown describing your environment (naming conventions, IP schemas, site definitions, critical apps, escalation contacts, maintenance windows). Kentik AI uses this context in all conversations in your organization, improving relevance and consistency (details: Kentik AI settings: Custom Network Context).
Example: a practical runbook outline for “Device CPU High”
Use this as a starting template for a device alert policy runbook:
-
Confirm the condition
Verify CPU percent, duration, and whether the issue is isolated or widespread (same site, same role, same vendor). -
Check correlated device health
Memory trend, interface errors (CRC/discards), queue drops, and recent interface flaps. -
Check whether traffic behavior explains the spike
Identify interfaces with the biggest change during the CPU spike. Use traffic breakdowns (and Cause Analysis when needed) to identify dominant contributors. -
Check event evidence
Review syslog/traps around the start time. Validate whether a change window overlaps (from Custom Network Context). -
Assess impact
Identify whether critical paths, peers, or services are affected (and validate experience when necessary with synthetics). -
Recommend the smallest safe next step
If transient and low impact: keep watching and tune thresholds/baselines.
If persistent and impactful: fail over, reroute, isolate a noisy interface, or escalate to vendor TAC with evidence.
Kentik AI Advisor can run many of these steps automatically as part of an alert investigation, while keeping its steps and evidence visible (see AI Advisor docs).
Network Device Monitoring vs. Network Performance Monitoring
While the terms Network Device Monitoring (NDM) and Network Performance Monitoring (NPM) may seem synonymous, they represent distinct but complementary aspects of network management. Both are essential for maintaining a healthy and efficient network, but they focus on different elements and serve unique purposes.
Focus of Network Device Monitoring
Network Device Monitoring (NDM) focuses on the health and status of individual devices within the network. It involves tracking key metrics such as availability, CPU usage, memory usage, disk space, device errors, and uptime. NDM aims to ensure each device functions properly and identifies potential issues before they escalate.
NDM involves monitoring a wide range of devices, including routers, switches, servers, firewalls, VMs, and cloud devices. It can help detect hardware failures, software crashes, overloaded resources, and other device-specific issues. By providing real-time or near-real-time information about each device, NDM enables administrators to maintain overall network health.
Focus of Network Performance Monitoring
Network Performance Monitoring (NPM) focuses on the performance and quality of service of the network as a whole. It involves measuring, diagnosing, and optimizing the service quality of network traffic. Key metrics in NPM include latency, packet loss, jitter, and bandwidth usage.
NPM tools often provide features such as traffic analysis, capacity planning, network mapping, and Quality of Service (QoS) analysis. They can help identify bottlenecks, bandwidth hogs, and performance issues related to network traffic. NPM helps ensure optimal service delivery and user experience by providing insights into how network traffic impacts performance.
Complementary Roles of NDM and NPM
While NDM and NPM focus on different areas, they are closely related and often used together. For example, a device failure detected by NDM could explain a performance issue identified by NPM. Conversely, a performance issue might lead administrators to check the health of individual devices.
A robust network management strategy typically involves both NDM and NPM, providing administrators with a holistic view of network health and performance.
For example, Kentik’s network intelligence platform integrates both network device monitoring and network performance monitoring features, enabling comprehensive visibility and control. This integrated approach helps teams identify device-specific and network-wide issues quickly, maintaining optimal performance and availability.
Correlating Device Health with Traffic and Experience
Device monitoring answers “Is the box healthy?” but users feel outcomes: latency, loss, failed transactions, and slow apps. That’s why modern monitoring architectures treat device metrics as one pillar in a broader system.
A useful framing is the “three pillars” of modern monitoring architecture:
- Network infrastructure metrics (device and interface health)
- Traffic analysis (what changed and where traffic is flowing)
- Synthetic testing / digital experience monitoring (how it feels from the outside)
(For the full framework, see Network Monitoring Architecture.)
A practical correlation workflow for device alerts
When a device or interface alert fires, use this correlation loop to get to root cause faster:
- Confirm device health (NMS)
Validate CPU/memory trends, interface errors, and recent state changes using device metrics (for example, via Kentik NMS).
- Identify traffic drivers (flow + Cause Analysis)
Check whether traffic shifted onto the device or a specific interface. If the “why” isn’t obvious, use Cause Analysis to quickly isolate which dimensions (apps, destinations, ASNs, sites) drove a spike or drop, then drill down to validate.
- Validate experience impact (synthetics)
If the device sits on a critical path, validate whether users are impacted using Kentik Synthetics (latency/loss/jitter, path views, page loads/transactions, public and private agents).
- Close with an evidence-backed narrative (AI Advisor)
Use Kentik AI Advisor to summarize what changed, scope impact, and recommend next actions, while keeping supporting data visible for verification.
This is the difference between “monitoring the boxes” and running a modern NetOps workflow: device health, traffic behavior, and experience all inform the same incident story.
Challenges in Network Device Monitoring
Despite its benefits, network device monitoring is not without its challenges:
- Network complexity: Modern networks can be incredibly complex, making monitoring a challenging task.
- Device heterogeneity: Networks often consist of devices from many manufacturers, each with different protocols and metrics, which can complicate monitoring.
- Scale of monitoring: As networks grow in size and complexity, so does the task of monitoring, increasing the risk of oversight and missed issues.
- Cloud-based environments: While cloud-based networks offer benefits, they also present unique challenges, including issues of visibility and control.
Modern network intelligence and observability solutions such as Kentik address a wide array of monitoring use cases and technologies. While Kentik NMS performs the core functions of traditional device monitoring tools, Kentik also offers flow-based traffic analysis, synthetic monitoring and testing, cloud/container monitoring, and more.
Network Device Monitoring Best Practices
To effectively monitor network devices, consider the following best practices:
- Regular device monitoring: Monitor devices continuously to catch potential problems before they escalate.
- Utilize multiple monitoring techniques: Combine methods (SNMP/telemetry, logs, flow, synthetics) for a more complete picture.
- Establish baselines: Normal behavior patterns make it easier to detect meaningful deviations.
- Proactive alerting: Set up alerts to be notified immediately when potential issues arise.
- Continual optimization and review: Regularly tune thresholds, reduce noise, and update response procedures.
Network Segmentation and Isolation
Segmenting the network simplifies monitoring and expedites troubleshooting by categorizing devices into manageable groups. Isolating critical devices enhances security, limiting exposure to threats and ensuring dedicated performance monitoring for crucial network components.
Redundancy and Failover Planning
Implementing device redundancy ensures continuous monitoring even when a primary device encounters issues. Failover plans help ensure uninterrupted observability by providing automatic switching to a backup system, preventing potential outages.
AI in Network Device Monitoring: From Alerts to Answers
Traditional device monitoring is good at telling you that something happened (device down, CPU high, interface errors). The more difficult part is converting an alert into a fast, confident answer: what changed, what’s impacted, and what should we do next? That’s where AI can help, not by replacing telemetry, but by turning telemetry into a consistent investigation workflow.
A practical AI-assisted device monitoring loop looks like this:
- Detect: an alert fires (CPU, memory pressure, interface errors, flaps).
- Gather: pull the most relevant device, interface, and time-window context automatically.
- Scope: identify blast radius (devices, interfaces, sites, dependencies).
- Explain: summarize likely causes with supporting evidence (graphs, tables, comparisons).
- Recommend: propose the smallest safe next step (rollback, failover, escalate, keep watching).
Kentik’s model for this is an AI agent: Kentik AI Advisor interprets natural language questions and can plan and execute multi-step investigations across the telemetry already in Kentik, while showing step-by-step logic and the data behind its conclusions (see AI Advisor docs).
A key guardrail for operational safety: AI Advisor is read-only and does not make changes to network device configurations. (Kentik documents this explicitly in the AI Advisor guidelines section.)
AI becomes most valuable when it can see enough context. Kentik’s own guidance is that AI Advisor works best when paired with the broader Kentik data foundation (device metrics, flow data, cloud telemetry, syslog/traps, and synthetics) so it can reason across device health, traffic behavior, and experience signals. Learn more in the blog post: Introducing Kentik AI Advisor: The Future of Network Intelligence.
Network Device Monitoring with Kentik’s Next-Generation Network Monitoring System
Kentik’s network observability solution facilitates an in-depth understanding of overall network performance as well as individual network device health. It enables proactive monitoring of critical device metrics, providing NetOps professionals with essential insights for maintaining network health and efficiency.
Kentik offers a suite of advanced monitoring solutions designed for today’s complex, multi-cloud network environments. The Kentik Network Intelligence Platform empowers NetOps pros to monitor, operate, and troubleshoot networks from on-premises to the cloud.
Kentik isn’t just a network device monitoring solution. Its SaaS network intelligence platform delivers visibility into network flow, powerful synthetic monitoring capabilities, and Kentik NMS, a next-generation network device monitoring solution.
To learn how Kentik can bring the benefits of network intelligence and observability to your organization, request a demo or sign up for a free trial today.
FAQs about Network Device Monitoring
What do you mean by network device monitoring?
Network device monitoring is the continuous observation and analysis of the health and status of network devices to proactively identify issues and maintain overall network health. Kentik supports this with Kentik NMS, which collects device health metrics and makes them easy to query, alert on, and troubleshoot.
What’s the difference between active, passive, and predictive network device monitoring?
Active monitoring checks device status with periodic requests (like pings), passive monitoring analyzes traffic flowing through devices, and predictive monitoring uses historical data and machine learning to forecast issues before they occur. Kentik supports an integrated approach by combining device metrics (NMS), traffic context, and AI-driven workflows to move from detection to diagnosis faster.
Which device health metrics matter most?
Common device health metrics include availability (up/down), CPU utilization, memory usage, disk space, device errors, and uptime. Kentik NMS collects and visualizes these metrics and supports higher-resolution collection via streaming telemetry where available.
What kinds of devices should a monitoring program cover?
A robust program typically monitors routers, switches, firewalls, servers, wireless devices, VMs, cloud network constructs (like gateways and load balancers), containers, and IoT devices. Kentik NMS is designed to monitor a wide range of device types and supports hybrid and multi-cloud visibility as part of a broader network intelligence platform.
What protocols and data sources are used for network device monitoring?
Common techniques include SNMP, streaming telemetry, syslog/log files, flow telemetry (NetFlow/sFlow/IPFIX), and cloud flow logs, plus service mesh telemetry in microservices environments. Kentik supports these approaches by combining device monitoring (SNMP/streaming telemetry) with traffic and cloud telemetry in one system.
Why is streaming telemetry considered an evolution beyond SNMP?
Streaming telemetry is push-based and provides higher-resolution, near real-time device status data compared to polling intervals, often with less device overhead. Kentik NMS supports both SNMP and streaming telemetry, and can collect very high-frequency metrics (like CPU) when streaming telemetry is enabled.
How is network device monitoring different from network performance monitoring (NPM)?
Network device monitoring focuses on the health and status of individual devices, while NPM focuses on network-wide service quality metrics like latency, loss, jitter, and bandwidth behavior. Kentik is designed to bring both together, correlating device health with traffic and performance context to speed root cause analysis.
What are common challenges in network device monitoring?
Common challenges include network complexity, heterogeneous device vendors and metrics, scale, and cloud environments that limit visibility and control. Kentik addresses these by providing vendor-agnostic monitoring and unifying device monitoring with flow analytics, synthetics, and cloud/container visibility.
What are best practices for effective network device monitoring?
Best practices include monitoring regularly, using multiple monitoring techniques, establishing baselines, proactive alerting, and continually reviewing and optimizing your monitoring strategy. Kentik supports baseline-driven monitoring patterns and alert workflows, and Kentik AI helps teams standardize investigations with repeatable runbooks.
Why do network segmentation and redundancy matter for monitoring?
Segmentation helps simplify monitoring and troubleshooting by grouping devices, while redundancy and failover planning help keep monitoring continuous even when systems fail. Kentik NMS supports scalable monitoring approaches and helps teams keep device and interface visibility consistent across complex environments.
How should teams visualize and report on device monitoring data?
Dashboards and graphs help show trends and anomalies, while periodic reports support deeper analysis and optimization planning. Kentik provides dashboards for device and interface metrics and supports fast querying so teams can build operational views that fit their environment.


