What is NetFlow? An Overview of the NetFlow Protocol
What is NetFlow?
NetFlow is a Cisco-developed flow monitoring technology used to collect and export metadata about IP traffic flows (not packet payloads) from network devices. NetFlow records help teams understand who is talking to whom, which applications are consuming bandwidth, and where performance or security issues may be emerging.
NetFlow at a glance
- What it captures: Flow metadata such as source/destination IPs, ports, protocol, interfaces, byte/packet counts, and timing information.
- Where it runs: Routers, switches, firewalls, and hosts that act as flow exporters.
- Where it goes: Exporters send flow records to a collector, which stores/pre-processes them for a flow analyzer.
- Most common versions: NetFlow v5 (fixed fields) and v9 (template-based, extensible).
- Standards relationship: IPFIX is the IETF standard for exporting flow information and is based on the template approach introduced by NetFlow v9.
How NetFlow works (in 4 steps)
- Define a flow: Packets are grouped into a unidirectional flow using shared attributes (for example, source/destination IP and ports, protocol).
- Collect and cache: The exporter tracks flows in an on-device cache as packets traverse an interface.
- Export flow records: When a flow ends or times out, the exporter sends a flow record (metadata) to a collector, commonly over UDP.
- Analyze: The collector and analyzer turn raw flow records into dashboards, reports, alerts, and investigations.
Key NetFlow benefits and common use cases
NetFlow is widely used for:
- Traffic analysis: Identify top talkers, bandwidth hogs, and application mix.
- Security monitoring: Detect DDoS patterns, scanning, data exfiltration signals, and unusual east-west activity.
- Performance troubleshooting: Pinpoint congestion, drops, asymmetric routing symptoms, and “where it got slow.”
- Capacity planning and cost analysis: Forecast growth, validate circuit upgrades, and attribute usage to teams/apps/customers.
- Usage accounting: Support chargeback/showback and policy enforcement.
NetFlow vs IPFIX vs sFlow (a quick comparison)
| Format | Defined by | How it works | Best for |
|---|---|---|---|
| NetFlow v5 | Cisco (widely implemented) | Fixed-format flow records | Simple IPv4 flow monitoring, broad compatibility |
| NetFlow v9 | Cisco (template-based) | Templates define which fields appear in records | Extensible flow export (IPv6, MPLS, richer context) |
| IPFIX | IETF standard | Template-based export modeled on NetFlow v9 | Vendor-neutral interoperability and standardized field models |
| sFlow | InMon / sFlow.org ecosystem | Statistical packet sampling + interface counters (not a per-flow cache) | High-speed links and lightweight telemetry where sampling is acceptable |
Note: Some vendors casually refer to IPFIX as “NetFlow v10.” In practice, IPFIX is its own IETF standard, and many devices support exporting flow data using either NetFlow v9 or IPFIX.
Developed by Cisco Systems, NetFlow is used to record metadata about IP traffic flows traversing a network device such as a router, switch, firewall, or host. A NetFlow-enabled device generates metadata at the interface level and sends flow data information to a flow collector, where the flow records are stored to enable network traffic analytics and management.
A network operator can use NetFlow data to determine network throughput, packet loss, and traffic congestion at a specific interface level. NetFlow data also supports other network-level monitoring use cases such as DDoS detection and BGP peering.

The history of NetFlow and versions over time
NetFlow was introduced on Cisco routers in the mid-1990s and quickly became the most widely recognized name in flow monitoring. Over time, flow telemetry expanded beyond Cisco and evolved into multiple compatible formats and standards, including IPFIX (the IETF standard) and vendor equivalents (for example, J-Flow and NetStream).
NetFlow variants
While the term “NetFlow” is commonly used as shorthand for flow monitoring, production networks typically encounter several related formats:
- NetFlow (v5/v9): Cisco’s flow export formats. v5 is fixed-field; v9 is template-based and extensible.
- IPFIX: The IETF standard for exporting flow information, based on the template approach introduced by NetFlow v9.
- sFlow: A different approach that relies on statistical packet sampling and interface counters rather than maintaining a per-flow cache.
- Other vendor flow formats:
- J-Flow (Juniper), commonly aligned with NetFlow-style records
- NetStream (Huawei/3Com legacy)
- xFlow: A generic umbrella term used to refer collectively to flow formats (NetFlow, IPFIX, sFlow, and equivalents).
NetFlow versions
The fields that make up a NetFlow record depend on the exporter and export version. Cisco introduced multiple versions over time, with v5 and v9 being the most commonly encountered:
- v1: First implementation (obsolete), IPv4 only (no IP mask and AS numbers).
- v2: Cisco internal version, never released.
- v3: Cisco internal version, never released.
- v4: Cisco internal version, never released.
- v5: Widely deployed and supported by many vendors; fixed-field format; IPv4 only.
- v6: No longer supported by Cisco.
- v7: Similar to v5 with a source router field (historical/limited).
- v8: Aggregated forms (built from v5-style fields).
- v9: Template-based and extensible. Commonly used for IPv6, MPLS, and richer routing/security context.
Practical note: When teams say “we collect NetFlow,” they often mean “we collect flow records,” which may actually be NetFlow v5, NetFlow v9, or IPFIX depending on the device and config.
How does NetFlow work?
NetFlow components
NetFlow monitoring solutions are typically comprised of three main components:
- Flow exporter: A NetFlow-enabled device that generates flow records and periodically exports them to a flow collector.
- Flow collector: A service that receives, stores, and pre-processes flow records from exporters.
- Flow analyzer: An analysis application that turns flow records into dashboards, reports, alerts, and investigations.

Flow records and data
A NetFlow exporter (NetFlow-enabled device) identifies a flow as a unidirectional stream of packets having in common (at least) the following:
- Input interface port
- IP source address
- IP destination address
- Source port number
- Destination port number
- Layer 3 protocol field
- Type of service (ToS/DSCP)
These attributes define a flow and form the core flow key. The exporter tracks the flow in an on-device cache, maintaining counters and timestamps as packets are observed.
Each time a new unidirectional IP traffic flow starts traversing a device, a new NetFlow flow record is created and tracked in the device’s on-board NetFlow cache. The function of NetFlow is to export this network flow data to a NetFlow collector for storage and analysis.
When flow records are exported
A flow record is typically ready for export when one of the following is true:
- Inactive timeout: No new packets are observed for a configured duration.
- Active timeout: The flow is long-lived and exceeds the active timer (for example, a long download).
- Session end signal: A TCP FIN/RST indicates the flow is terminated.
At export, the flow record is encapsulated in a datagram and sent to a NetFlow collector that is typically external to a NetFlow-enabled device. The collector stores flow metadata in a record format defined by the export protocol (NetFlow v5/v9 or IPFIX).
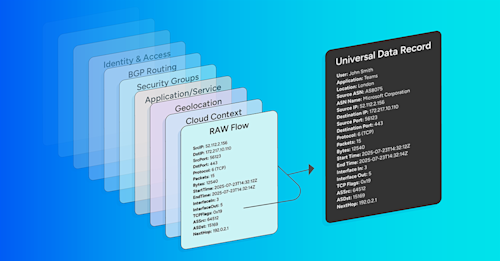
Common fields in a NetFlow record
A NetFlow record commonly includes:
- Source and destination IP address
- Source and destination TCP/User Datagram Protocol (UDP) ports
- Type of service (ToS/DSCP)
- Packet and byte counts
- Start and end timestamps (or equivalent timing fields)
- Input and output interface numbers
- TCP flags and encapsulated protocol (TCP/UDP)
- Routing/BGP context (next-hop address, source ASN, destination ASN, source/destination prefix mask)
After the flow collector receives flow records, a flow analyzer extracts insights so network teams can identify traffic patterns, investigate incidents, and troubleshoot performance.
Common NetFlow pitfalls (and how to avoid them)
These issues are common reasons NetFlow deployments under-deliver:
- Sampling confusion: Confirm whether exporters are sampling (and at what rate) before interpreting volumes or “top talkers.”
- Timeout tuning: Active/inactive timeouts change record counts and granularity. Tune based on traffic patterns and investigation needs.
- UDP loss: If exporting via UDP, packet loss can drop flow records silently. Keep collectors close (network-wise) and monitor export/receive health.
- Template health (v9/IPFIX): Template-based exports require templates to be received and refreshed. Validate template refresh behavior and collector support.
- Clock sync: Timestamps are only as good as device time. Use NTP and validate clock drift.
- Asymmetric routing: One-direction visibility can mislead. Combine with routing/BGP context and multiple vantage points.
Enriching NetFlow data
Raw NetFlow (and related IPFIX, sFlow, and cloud flow logs) captures who-talked-to-whom, on which ports, and how much. Flow enrichment adds human-readable context from other systems so that network operators can quickly answer who, what, where, and why questions, without manual lookups.
Common NetFlow enrichment sources include:
- DNS and GeoIP for hostnames and geographic location.
- SNMP/device inventory for device and interface names, speeds, and roles.
- Routing/BGP context such as origin ASN, next hop, ultimate exit, and prefix.
- Cloud metadata including account/project, VPC/VNet, region/AZ, instance IDs, and gateway/interface type.
- Kubernetes/application context such as cluster, namespace, service/workload.
- Custom business tags which could include environment, owner, cost center, and customer data.
Enrichment is often applied as flow records are ingested so that each stored flow record retains accurate context over time and queries remain fast at scale. For a deeper discussion of why enriched flow belongs in daily operations, see our blog post “Why (Enriched) Flow Data Belongs in Every Network Operator’s Daily Toolbox”.
Why use NetFlow: key benefits and capabilities
NetFlow enables flow-based analysis that helps teams understand traffic patterns across networks and environments. Common benefits include:
- Optimized bandwidth usage and capacity planning
- Deeper visibility into network and application behavior
- Faster root cause analysis for performance slowdowns
- Identification and investigation of security threats
Common NetFlow-driven monitoring use cases include:
- Network, user, and application monitoring
- Capacity planning
- Cost reporting and analysis of network usage
- Network security
- Network troubleshooting
Related resources about NetFlow
For an excellent overview of flow extensibility and how flow telemetry evolved, see Kentik CEO Avi Freedman’s posts:
More NetFlow resources:
- The Network Traffic Analytics that Enterprises Need: Learn why traditional network monitoring tools don’t scale to meet today’s network visibility needs, why more enterprises are moving from faults & packets to flow, and how Kentik can help.
Related Kentipedia entries:
Standards and authoritative references
- Cisco NetFlow overview/config docs (NetFlow features and export formats): https://www.cisco.com/c/dam/en/us/td/docs/routers/asr920/configuration/guide/netmgmt/fnf-xe-3e-asr920-book.html
- IBM: What is NetFlow? (components and how it works): https://www.ibm.com/think/topics/netflow
- RFC 3954 (NetFlow v9, informational): https://www.rfc-editor.org/rfc/rfc3954.html
- RFC 7011 (IPFIX protocol, IETF standard): https://datatracker.ietf.org/doc/html/rfc7011
- Wikipedia (background, versions, and NetFlow/IPFIX relationship): https://en.wikipedia.org/wiki/NetFlow
Kentik in brief: Kentik is a network intelligence platform that collects flow telemetry (NetFlow, IPFIX, sFlow) and cloud flow logs, enriches it with context, and makes it easy to ask and answer traffic questions at scale.
In practical NetFlow terms, Kentik helps you:
- Collect and normalize flow and cloud traffic data across on-prem, cloud, and internet edges.
- Enrich raw flow with DNS, GeoIP, routing/BGP context, device/interface metadata, cloud tags, and custom business dimensions.
- Investigate performance and security issues faster with traffic analytics, alerts, and integrations, and optionally export enriched data to your own tools and data platforms.
Learn how AI-powered insights help you predict issues, optimize performance, reduce costs, and enhance security.

FAQs about NetFlow
Does NetFlow capture packet payloads?
No. NetFlow exports metadata about traffic flows (who talked to whom, on which ports and protocols, how much, and when). It does not export the contents of packets.
What is a “flow” in NetFlow?
A flow is typically a unidirectional stream of packets that share common properties such as source and destination IP addresses, source and destination ports, and the Layer 3 protocol. Devices group packets into flows so they can summarize traffic efficiently.
What is a NetFlow record, and what fields does it include?
A NetFlow record is a summary of a flow. Common fields include source/destination IPs and ports, protocol, input/output interface, byte and packet counts, and start/end timestamps. Many deployments also include routing context such as next hop and ASN data.
What are NetFlow exporters, collectors, and analyzers?
- Exporter: a router/switch/firewall/host that observes traffic and creates flow records.
- Collector: a service that receives flow records and stores or pre-processes them.
- Analyzer: a tool that queries flow data to produce dashboards, reports, alerts, and investigations.
When does a device export flow records?
Export usually happens when a flow ends or “ages out.” Common triggers include:
- Inactive timeout (no packets seen for a period)
- Active timeout (long-lived flow exported periodically)
- Session termination signals such as TCP FIN/RST (when supported)
What’s the difference between NetFlow v5 and NetFlow v9?
NetFlow v5 uses a fixed set of fields and is most commonly associated with IPv4.
NetFlow v9 is template-based, meaning the exporter can define which fields appear in records. That flexibility enables richer context (for example, IPv6 and MPLS fields) and makes v9 a foundation for more extensible flow export.
NetFlow vs IPFIX: what’s the difference?
NetFlow is a Cisco-originated flow export format family (most commonly v5 and v9). IPFIX is the IETF standard for exporting flow information and uses a template-based approach similar to NetFlow v9. In mixed-vendor environments, IPFIX is often preferred for interoperability.
NetFlow vs sFlow: which should I use?
NetFlow (and IPFIX) summarize traffic by building and exporting flow records. sFlow is sampling-based and is designed for scalability on very high-speed links. If you need precise per-flow visibility and can support the overhead, NetFlow/IPFIX is common. If you need lightweight, scalable telemetry where sampling is acceptable, sFlow is often a good fit.
How does sampling affect NetFlow accuracy?
Some devices can export unsampled flow data, while others use sampling to reduce overhead. With sampling, only a subset of packets is selected for analysis, so totals are estimates and must be interpreted using the configured sample rate. Sampling can still be very useful for trend analysis, anomaly detection, and top-talkers, but it changes how you should read absolute volumes.
What are common NetFlow troubleshooting gotchas?
A few repeat offenders:
- Sampling rate is unknown or mismatched (leading to bad volume assumptions)
- UDP export loss (missing records during congestion)
- Template issues in v9/IPFIX (collector does not receive templates or refreshes)
- Timeouts too high/low for your use case (granularity vs record volume)
- Device clocks drift (timestamps become misleading)
How Kentik supports NetFlow monitoring
Kentik turns raw flow records into operational answers by combining collection, enrichment, and analysis in one place.
1) Collect and normalize flow and cloud traffic
Ingest NetFlow v5/v9, IPFIX, and sFlow from network devices, plus cloud flow logs, so you can analyze traffic across hybrid and multicloud environments without stitching together separate tools.
2) Enrich flow at ingest for faster investigations
Attach human-readable context to flow records as they arrive, such as hostnames, geography, interface names/speeds, routing and ASN context, cloud account and region metadata, Kubernetes and application tags, and your own business dimensions. This keeps context consistent over time and speeds up queries.
3) Analyze, alert, and integrate
Use enriched flow analytics for capacity planning, troubleshooting, and security investigations. When you need to operationalize flow beyond the UI, export enriched records to downstream systems (data lakes, SIEMs, observability platforms) to support your workflows.
To experience Kentik’s NetFlow monitoring features for yourself, start a free trial or request a personalized demo.