Harden Network Policy Management
Secure networks with actionable views of inbound, outbound, and denied traffic.
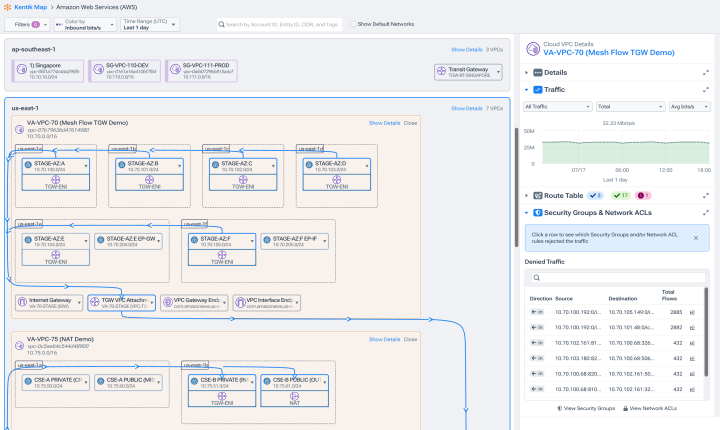
Boost productivity with easy tracking and filtering of denied traffic, enriched with policy metadata.
See traffic, enriched with deep business and security context, flowing across networks and multi-cloud accounts.
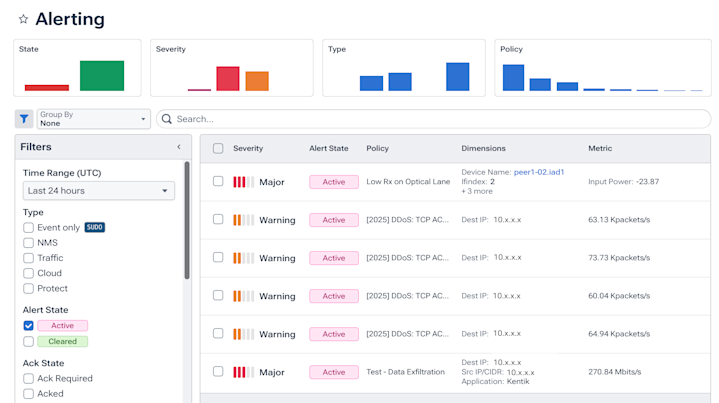
See security policy in action with alerts that help to quickly diagnose threats and understand their impact.
Monitor and automatically detect malicious traffic
- Detect anomalies, understand attack vectors, and identify embargoed country communications within real-time traffic.
- Establish a baseline for network behavior and get alerts on abnormal activity.
- Quickly correlate traffic patterns and find root causes with data enrichment, including IP reputation data.
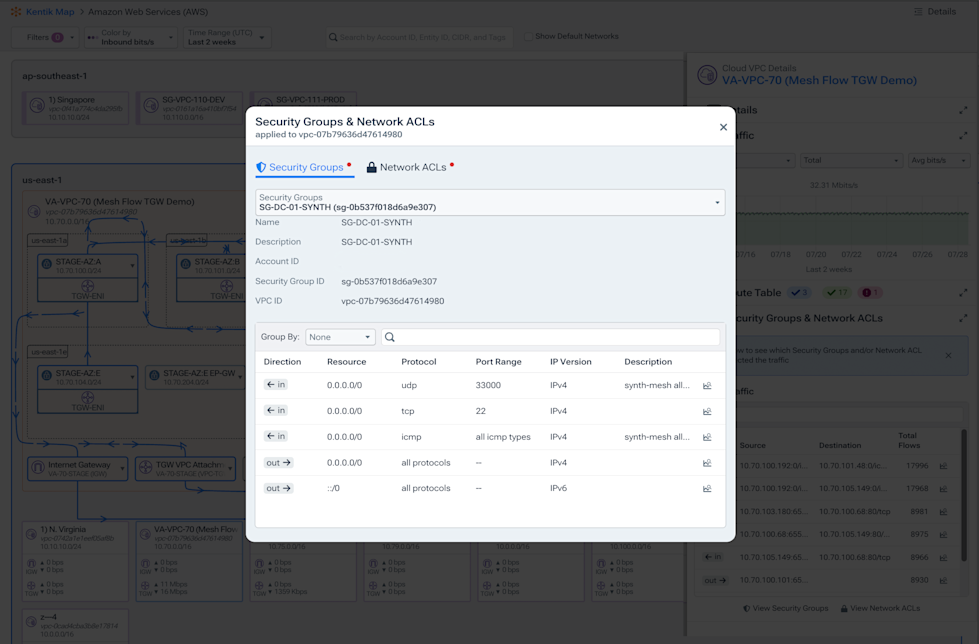
Audit traffic to network resources
- Quickly verify that perimeter, security group, and Access Control List rules match your security model.
- Use fast, fine-tuned queries to understand context-enriched traffic data when investigating bad actions.
- Trace activity and transactions from multi-cloud environments in one platform.
Optimize network access policies using traffic insights
- Easily identify suspicious traffic flowing through permissive or misconfigured security policies.
- Quickly access the data needed to validate least-privilege enforcement, ensuring only required ports, protocols, and actors are allowed.
- Monitor allowed and rejected traffic to continuously track and manage security policy enforcement across the network.
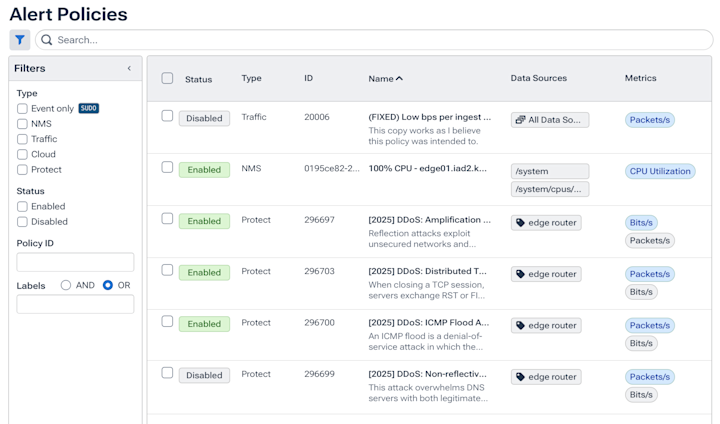
Automatically surface denied traffic on cloud environments
- Quickly resolve tickets related to common cloud connectivity issues to unblock teams.
- Find and fix high-impact connectivity issues right from the Kentik Map.
- Get alerts to instantly know and visualize what matters to your business.

“Kentik quickly shows you abnormalities in traffic flow and allows you to easily drill down to get more detail.”
Explore the platform
Network Policy Management FAQs
What is network policy enforcement and why does it matter for security?
Network policy enforcement is the process of making sure access controls (e.g., security groups, ACLs, firewall rules) actually behave the way they were intended — permitting only authorized traffic and blocking everything else. Effective enforcement helps reduce unintended exposure and attack surface, lets teams verify segmentation, and ensures compliance with internal security standards and regulatory policies. Kentik helps visualize allowed and denied traffic across environments so you can validate that enforcement aligns with policy intent.
How do I ensure compliance with segmentation policies across environments?
Ensure segmentation compliance by continuously validating observed traffic against intended policy across cloud and on-prem. Kentik helps by analyzing allowed and denied flows, enriching traffic with policy context, and alerting on drift or unexpected cross-segment communications so teams can verify least-privilege enforcement and remediate misconfigurations quickly.
How can I detect policy misconfigurations or gaps in real time?
Policy misconfigurations often show up as unexpected traffic flows or denied connections that shouldn’t occur under your intended rules. By correlating traffic with security metadata, continuous monitoring, and anomaly detection, you can surface suspicious activity quickly. Kentik lets you filter and investigate denied traffic, observe policy exceptions, and alert on traffic that violates expected security behavior so teams can fix misconfigurations before they become incidents.
How do I audit network policies in hybrid cloud and multicloud environments?
Audit hybrid and multicloud network policies by inventorying configurations across clouds and on-prem, continuously monitoring policy behavior versus actual traffic, and alerting on drift or unexpected access. Tools like Kentik correlate flow and policy enforcement to show mismatches between intended rules and observed traffic, helping teams tighten controls, detect misconfigurations early, and simplify compliance reporting.
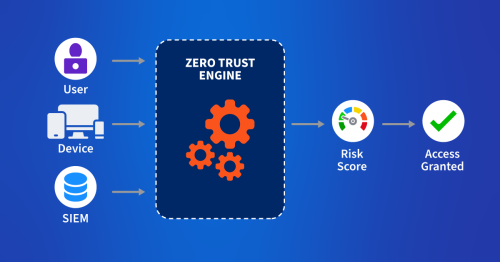
How can I ensure zero-trust policies are enforced at the network layer?
Treat “enforcement” as continuous verification: Confirm that only the required ports, protocols, identities, and paths are actually occurring, and alert when traffic violates least-privilege intent (unexpected east-west flows, rejected-traffic spikes, or new communications between sensitive segments). Kentik supports this by validating network policy outcomes against real traffic, highlighting unexpected exposure, and helping teams confirm segmentation and access controls behave the way they were intended. See: How to Harden Zero-Trust Cloud Network Policy “Kentik Blog: How to Harden Zero-Trust Cloud Network Policy”).
How do I prove compliance for network segmentation and microsegmentation?
Prove compliance by producing evidence that only the intended communications are occurring, including which workloads talk, on what ports, across which segments, and where blocked or rejected traffic indicates attempted policy violations. Kentik supports this by monitoring allowed and rejected flows across hybrid environments so teams can continuously audit microsegmentation outcomes and generate defensible evidence for security and compliance reviews.