Get to the Bottom of Security Incidents
Never have to ask “what happened?”
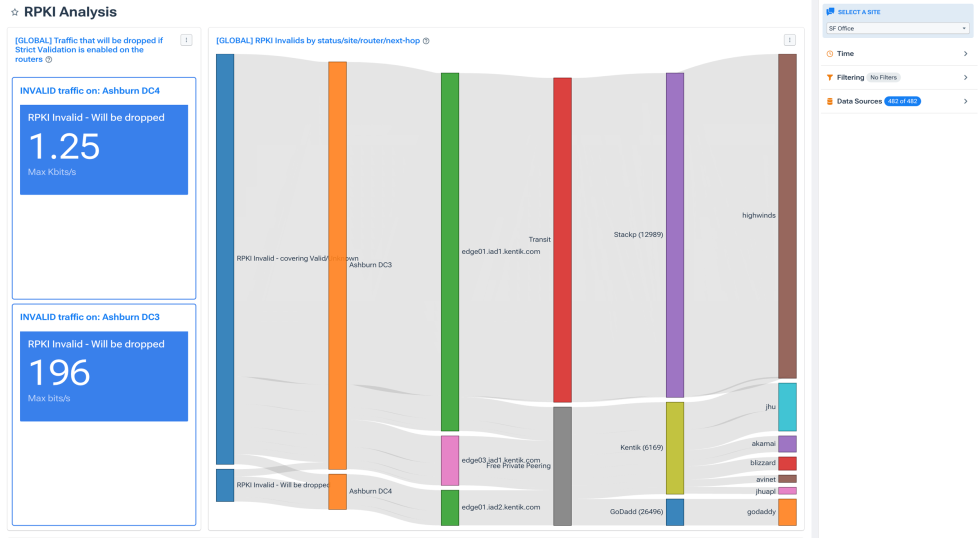
Reduce the guesswork
Achieve lossless lookbacks with full fidelity data.
Understand attack vectors
Understand timing, volume, and history of malicious traffic across the kill chain.
Protect from future threats
Close security gaps and understand bad actors.
Full-fidelity data retention
- Identify pre-breach reconnaissance.
- Understand historical data exfiltration/infiltration.
- Determine what accessed the network with global context, security, and business enriched metadata.
- Identify users with ID-enriched flow data.
Trace traffic inside and outside your networks
- Detect and alert on route hijacking incidents.
- Monitor and uncover unexpected traffic origins.
- Track changes in route propagation and identify BGP hijacks.
- Identify lateral movement and recon traffic.
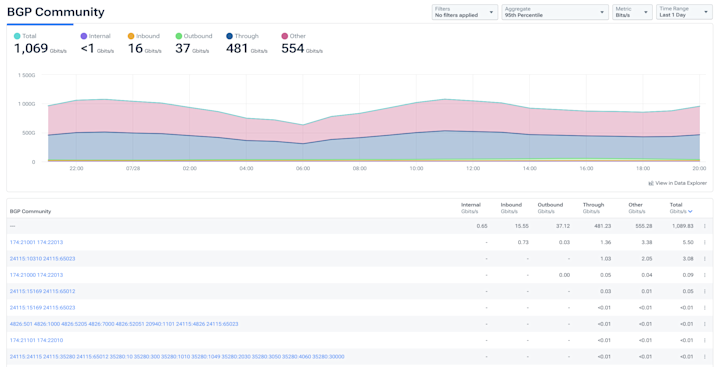
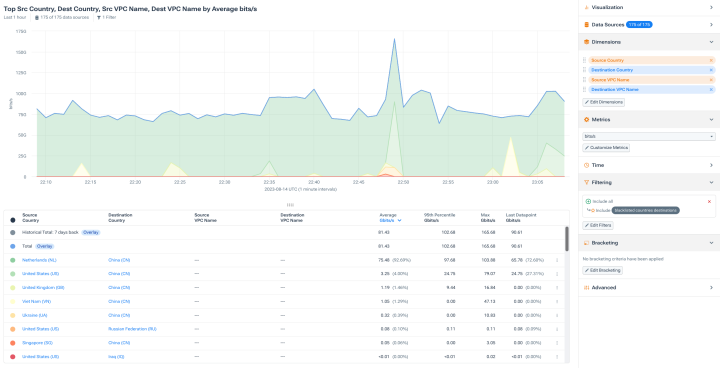
Built for complex networks
- Analyze across data center, clouds, and containers.
- Audit traffic to and from the network to identify prohibited domains or geographies.
- Keep granular fidelity even during large spikes in traffic.

“With Kentik, we can pinpoint the source of suspicious traffic virtually in real time.”
Tatsuya Mori
Senior Manager of IT Infrastructure/Network, Square-Enix
How to Perform a Forensic Analysis After a Security Breach
Explore the platform
We use cookies to deliver our services.
By using our website, you agree to the use of cookies as described in our Privacy Policy.



